Cyberattacks are numerous and do not distinguish between companies and individuals when targeting a target. You’ve most likely heard the term “cyber threat” in the media before, but what exactly are we talking about? Other ways you may have heard this are “cyberthreat”, “cyberattack” or similar.

What is a Cyber Threat?
Today the term “cyber threat” is used predominantly in the world of information security.
A cyber threat is a malicious act conceived with the purpose of damaging systems, stealing data or any purpose that has the purpose of causing damage of any kind. Viruses, data breaches and DDoS attacks are included. Even if the threat is virtual, what is real is the attacker’s intent as well as the potential impact. While many cyberattacks are mere nuisances, some are quite serious. Some even potentially threaten human lives.
The potential impact that these kinds of attacks can have is often underestimated. Most of the time, the attacks are easily identifiable and do not pose much risk. Instead, other times it happens to come across some more sophisticated threats, difficult to identify, which represent a big problem even for many companies.
Cyber threats are a major concern for businesses. Cyberattacks can lead to power outages, government equipment failures, and breaches of state secrets. They can manipulate telephone and computer networks or, as in the case of ransomware, they can cripple entire systems by making data inaccessible.
Every day new companies and organizations set foot in the digital world with awareness of the risks associated with their technological infrastructures. In some cases, cyber threats are underestimated and this often means great economic and image damage for the company that has underestimated cyber threats and security.
The increase in IT-related risks is real, as are data security solutions. The best thing to do is to take the necessary safety measures right away.
Types of Cyber Threats
The types of cyber threats are numerous, and it must also be considered that they are constantly evolving. The intent of hackers is usually to secure an economic gain by carrying out sabotage, espionage or data theft operations. As a result, they can be expected to do everything possible to achieve their ends.
Virtually every cyber threat falls into one of the following ten types of risks. Hackers have an abundance of options to choose from in order to operate. Furthermore, computer literacy is all in all poor, so hackers often have an easy time, especially for small local realities.
The 10 most common types of computer threats
Malware
It is a type of software that executes a malicious command on a device or within a computer network, corrupting data or taking control of the system.
Phishing
Phishing is an e-mail attack that consists of tricking the recipient into revealing confidential information or inviting him to download malware by clicking on a link in the body of the message. These are real scams, which we have talked about extensively in other articles. Often they don’t even involve great IT skills on the part of the attacker, just a little social engineering.
Vishing
Vishing is a more sophisticated form of phishing in which the hacker uses VoIP technology to contact the victim, attempting to trick them. There is also a variant that instead uses text messages to attack, it is called smishing.
Man in the Middle
As the name suggests, this type of attack refers to when a hacker intervenes in a conversation posing as one of the two parties, with the aim of stealing sensitive information. What we often don’t think about is that the conversation is between two machines and therefore not immediate to monitor.
Trojan viruses
The origin of its name is inspired by the famous Trojan Horse of ancient Greece. Trojan is a type of malware that infiltrates a computer system by hiding its true nature. For example, it could impersonate known software and then release malicious code once inside the host device.
Ransomware
Ransomware is an attack that uses encryption to make information on a system inaccessible. The aim is to demand a ransom in exchange for being able to access the data again. Possibilità che a volte, in realtà, non è nemmeno assicurata.
DDoS attack
It occurs when the attacker uses many devices to overload a target, such as a website, with requests, causing it to crash or become instabilities.
Attacks on IoT devices
This is an increasingly popular attack due to the nature of the targets. Devices such as sensors or industrial plants connected to the network are vulnerable to multiple types of cyber threats. The hacker could take control of the device and then later use it in a DDoS attack. Alternatively it could steal the information present in the device itself obtaining important data to continue the attack. Given their number of frequently out-of-date operating systems, IoT devices are a very attractive target.
Malware in mobile applications
Phones and tablets are just as vulnerable to malware as any other device. È possibile inserire malware all’interno di app, nei siti web o nelle e-mail sfruttando il phishing. Once compromised, a mobile device can provide access to personal information, location data, and financial accounts.
A recent example of this type of eventuality is Pegasus software, which is used to monitor and collect data from journalists around the world. (Source: The Guardian)
Practical defense and prevention solutions
Cyber threats are always expanding and improving. Millions of them are created every year, many of them follow the aforementioned characteristics, but others are technologically more complex and more powerful.
Fortunately, however, there are also more and more highly qualified companies in the field of IT security that offer cutting-edge tools and services that help prevent, identify and promptly block all kinds of IT attacks.
Threat detection tools
Threat detection tools are an essential part of a company’s cybersecurity technology stack. Threat detection is also the first defense against any Cyber Threat.
Specific solutions, such as the use of a SOCaaS, for example, are of vital importance for safeguarding an IT infrastructure, thanks also to the integration of the SIEM engine which includes UBA and UEBA, guaranteeing complete control also over the users.
Another useful tool is definitely ACP. Acronis Cyber Protect is a solution that integrates data protection and management to safeguard your endpoints, data and systems. Its automation capabilities provide unparalleled protection, enabling businesses to increase their productivity and reduce risk.
Vulnerability Assessment & Penetration Test (VA-PT)
Services like VA & PT are field tests that test the infrastructure in a concrete context. Our teams of white hat hackers find vulnerabilities within the system to point the finger at weaknesses to fix.

Conclusions
We have learned what a cyber threat is and its most common types, also discovering which solutions can be adopted in order to guarantee better corporate and employee safety.
What countermeasures has your company taken to protect your safety? If you would like more information about it, you can contact us by pressing the button below. We offer ad hoc services and solutions to strengthen corporate defenses.
Useful links
Estimated reading time: 6 minutes
Despite some seasonal declines, ransomware is still a serious security threat, especially for those who underestimate it . It is often thought that to protect yourself from ransomware it is enough to have a backup copy of your data. This point of view does not take into consideration various aspects. One of them is the relationship between ransomware and NAS ( Network Access Storage ), where you often store a backup copy of the server, thinking it is enough.
Ransomware attacks are capable of rendering entire disks unusable by encrypting the file system . Network disks are at risk, which can also be encrypted, reducing the effectiveness of a backup stored on a NAS.

Definition of Ransomware
Ransomware, as we have seen in other articles, is a form of malware that encrypts the victim’s files. The attacker then demands a ransom from the victim to restore access to data against payment .
Users are shown instructions on how to pay a fee to obtain the decryption key. Costs can range from a few hundred euros to thousands, payable to cybercriminals in Bitcoin.
Once the malware gets executed, it’s almost always too late. In fact, often the victim does not notice until the ransom demand is made or when the entire disk has been completely encrypted.
How ransomware works
There are several ways that ransomware can take to access a server. One of the most common delivery systems is phishing . Some attachments arrive at the victim’s computer in an e-mail message, masked from a harmless file.
Once executed, these software masquerading as harmless files can take control of the victim’s computer, especially if they have social engineering tools built in which trick users into allowing administrative access . Tracing back to the server isn’t as complicated as it might seem.
Some other more aggressive forms of ransomware, such as NotPetya , exploit security holes to infect computers without the need to trick users.
There are several things malware could do once it has taken over the victim’s computer, but by far the most common action is to encrypt some or all of the files it has access to. If you want to get into the technical, here’s more information on how encryption takes place.
The most important thing to know is that at the end of the process, files cannot be decrypted without a mathematical key known only to the attacker . The victim is presented with a ransom note and explained that without a payment, the files will remain inaccessible.
Regardless of the requests and how the ransomware is unleashed in the first place, the thing to note is that there is no data that can be saved. So, if your customers’ data is on a server, they can be involved in such an attack.
If the ransomware encrypts file systems and not just individual files, the problems could multiply.

Ransomware, NAS and backups
One of the ways to mitigate the risk is to have a backup available with which to restore the data without having to surrender to payment. The best practices for management backups do not want there to be backups on the same machine, so it is possible that they are kept on network disks, always accessible from servers. But in fact those disks are part of the machine, as they are accessible.
These disks, called NAS (Network Access Storage), are great solutions for managing files on a network, but they can become as useless as the server in the event of a ransomware attack. If the attack encrypts the file systems, it is possible that finding the remote folders on the NAS encrypts those as well, rendering the backup unusable.
The targets of a ransomware
There are several ways attackers choose which organizations they target with ransomware attacks. Sometimes it’s a matter of opportunity – for example, attackers might target universities because they tend to have smaller security teams and a disparate user base that share many files, making it easier to penetrate their defenses.
On the other hand, some organizations are tempting targets because they seem more likely to pay a ransom quickly. For example, government agencies or medical facilities often need immediate access to their files. .
Law firms and other organizations with sensitive data may be willing to pay to keep news of a compromise hidden , and these organizations are often particularly sensitive to a data exfiltration threat.
However, it has been noted that some ransomware is capable of spreading itself on the network . In fact, no one is completely safe, especially if the data stored on the servers is sensitive.

Ransomware and NAS: how to manage backups
As we have seen, ransomware is no small threat to the data stored on corporate servers. Now let’s see what precautions you can take to protect your data and servers.
Do not use NAS for backups
Se il ransomware arriva a un NAS, quasi certamente lo cifrerà rendendo il backup inaccessibile. Evitare questo problema è facile: usare il cloud!
The server provider should offer the ability to store machine backups on the cloud . This means that the backups are not always reachable by the server and therefore the software is unable to encrypt them.
This is the standard of our VPS service . In case of compromise, in fact, it is sufficient to restore the virtual machine to an earlier state through one of the backups stored in the cloud .
Alternatively, you can backup on premise , ie locally, physically in the company. Using the Acronis Backup service you can perform a backup on an external disk not connected to the network.
Another solution, hybrid of the previous ones, is to create a backup through Acronis and store it in the cloud and not locally. You maintain the advantage of having a remote backup that is not connected to the server constantly.
Preventing attacks
Finally, it is correct to mention that there is another solution, the precautionary solution. With the use of our service SOC and thanks to the use of latest generation analysis systems, it is possible to immediately identify a malware or an attack ransowmare and block it before it does damage.
Whether it is adopting best practices for backup and storing them remotely, or adopting a SOC to protect this aspect and many others in the field of IT security , SOD is available to discuss the situation and find a solution tailored to the needs of your company.
Contact us to ask for information, we will be happy to answer any questions.
Useful links:
Useful links:

Estimated reading time: 8 minutes
Looking to up the ante and earn more money with the ransomware , i Cybercriminals are increasingly using a tactic known as double extortion ransomware . Not only do they encrypt data and demand a ransom from the victim to regain access. They also threaten to upload them online if their conditions are not met.
Let’s take a step back, ransomware is one of the most common types of malware. It targets a company every 14 seconds and it cost $ 11.5 billion in 2019 alone . Typically, hackers who carry out these attacks break into a system to steal data and delete it if the victim doesn’t pay a ransom.

Why do hackers prefer double-extortion ransomware?
The rise of double extortion ransomware proves that cybercriminals are constantly expanding their arsenal. Paolo Passeri, director of cyber intelligence at the software firm Netskope , says these attacks they have become popular because they are the easiest way for hackers to make money.
Passeri Says: “With double extortion ransomware attacks, even if a backup is available, attackers can put more pressure on the victim to pay the ransom . The increased pressure comes from the potentially serious consequences of a data leak, for example economic and reputational damage. Groups like REvil are even more creative: they don’t just leak data, they monetize it by auctioning it on the dark web and putting even more pressure on their victims. “
When conducting a double extortion ransomware attack, hackers start spending more time on the overall strategy . Sparrows warns that scammers are no longer taking an opportunistic approach. Instead, they are carefully selecting their target and method of attack to increase the ransom money they make . He explains: “ the threat actors select their victims, choosing organizations whose businesses could be affected by a data leak “.
The spear phishing is the primary means of distributing double extortion ransomware, but cybercriminals are also by exploiting vulnerabilities in on-premises devices such as VPN concentrators. “In the past few months, nearly all major VPN technologies have suffered severe vulnerabilities that have been exploited for similar attacks,” says Passeri.
“This is unfortunate given the current situation with forced telework where these remote access technologies play a crucial role in ensuring business continuity during Covid-19. These systems are directly exposed to the Internet, so threat actors can scan them and then exploit any vulnerabilities discovered “.
Risks of Doxing : diffusion of private data
Double extortion ransomware provides more opportunities for cybercriminals, allowing them to extort victims twice. They can ask for a first payment to decrypt the files and a second payment not to make them public.
This technique, also known as doxing , is been used by an increasing number of ransomware groups over the past year. The consequences of doxing are more severe for the victim, so they often come down to demands. This means more money in the pockets of cybercriminals to fund new strains of ransomware and support other criminal activities.
Improvements in malware and financial incentives for hackers have led to the growth of double extortion ransomware attacks. In the past, ransomware encrypted files and hackers stole data, but it was rare to do both.
We now have bots that can scan the web for unprotected data, steal it, encrypt it or delete it, and leave a ransom note for the owner, all in one automated attack. The hacker can then collect a ransom for the data and sell the data to other criminals, playing double-crosses with minimal effort .

An aggressive-tactic
There has been an influx of double extortion ransomware attacks in the past year. Hackers gained traction in late 2019 when high-profile groups like Maze began exploiting aggressively this tactic.
In these particularly aggressive cases, the hacker would extract a copy of the data before encrypting it . This way the attacker not only prevents the victim from accessing her data, but also keeps a copy of the data for himself.
To claim responsibility and put pressure on the victim during the negotiation process, the attacker often released small chunks of data online. If the deals are blocked or failed, the attacker publishes all the stolen data or sells it to third parties . This creates a significant violation against the victim.
What to do
To defend against these attacks, there are several steps companies should take . For example, keeping systems updated to ensure that known vulnerabilities are resolved. It is also imperative that organizations have a layered security approach that includes the use of data loss prevention tools . An example is the service offered by SOD Acronis Cyber Protect Cloud . The system can stop the extraction or encryption of the data which initiates these double extortion attacks.
But what can organizations do if they can’t successfully mitigate one of these attacks?
Organizations should try to include a last line of defense that isolates and stops illegitimate encryption immediately . This mitigates the risk when traditional prevention-based security has been compromised or bypassed. Robust backup processes, including air-gap backups, should also be considered to make it more difficult for criminals to encrypt or disable critical data stores.
Consequences
If an organization falls victim to a double extortion ransomware attack, there are often dire consequences. Criminal groups are increasingly blatant, even dystopian names like Maze, Netwalker and REvil, are an indication of this inclination. Their pride leads them to display exfiltrated data as online trophies and even sponsor clandestine hacking contests to display their malware. In a kind of cyber show-off . < / p>
For the victims, the consequences can be devastating. Travelex, a currency exchange service, went into receivership with the loss of 1,300 jobs in the UK following a ransomware attack . During the heist, the cyber gang REvil asked the company to pay $ 6 million in 48 hours. The company has faced the threat of publishing credit card information, national insurance numbers and birth dates of its customers.
It is clearly critical that companies do everything they can to identify and stop these attacks before they cause more damage. Preventing these attacks proactively is much better than mitigating their effects, with all the financial costs and reputational damage they entail .
Most attackers gain access through human error . For this, together with technical measures such as internal data access management and back-up, staff training and supervision are key elements in an organization’s defenses .
Victims essentially have two choices, both of which are costly: if they refuse to pay, they face a catastrophic data breach with exposure to painful regulatory fines and civil demands; if they pay the ransom, they still have no guarantee that the data will be returned.

Handle double-extortion ransomware
While getting hit by ransomware can deal a severe blow to any business, companies should be cautious when asked to pay a ransom. Doing so could involve even greater risks . There is no certainty that these hackers will not ask for more money without releasing the data anyway.
It is important for companies to secure their networks and conduct mock test < / a> to mitigate the ransomware threat . Such simulated attacks will help spot vulnerabilities within the organization without the risk of facing serious financial problems and having to answer very difficult questions from customers.
Implementing strong resilience measures is the best way to prevent double extortion ransomware. Ransomware is often a secondary infection. Threat actors seek to exploit known vulnerabilities, particularly in relation to remote access protocols and applications that are critical for working from home.
Critical to mitigating this is ensuring that vulnerabilities are patched in a timely manner and that network data logs are monitored for any unusual activity or data exfiltration. < / strong> There is therefore a potential window of opportunity to remedy any primary infection (which precedes the ransomware) and thus prevent the ransom note process from developing.
Education
Organizations need to educate staff about the risks of double extortion ransomware and how it is executed . Individual users can also be of great help by being aware of the potential of unsafe attachments. They should also be cautious about clicking any email links received in any communication , particularly with the recent resurgence of Emotet , a known malware.
There are two defense strategies for dealing with double extortion ransomware. First, robust backups, to make sure you don’t your hands tied if hackers gain control of your data. Then, encryption, to make sure that if an attacker threatens to expose your data, it’s protected too.
These approaches should then be incorporated into a broader strategy: careful monitoring of the network that could allow attackers to be cut off, and promoting employee IT education not to fall victim to phishing attacks which are often the main cause of a ransomware incident.
The threat of double extortion ransomware is undeniable, with cybercriminals carefully targeting and creating these attacks in an attempt to increase the size of ransom.
Organizations often feel they have no choice but to pay the ransom to avoid the leak of sensitive data. But it’s actually a Russian roulette game and the stolen information can still find its way online. Therefore the focus must be on prevention and risk mitigation .

Small and medium-sized businesses have little room for maneuver when it comes to investment. Precisely for this reason, every step that involves an expense is weighed and evaluated in every aspect before being carried out. We know the fears that underlie such reasoning, and for this reason we have decided to dedicate an article precisely to the advantages that SOD services can offer to small and medium-sized enterprises. The adoption of cloud services for small businesses is an important step that requires some study.
Services available in the cloud
Cloud computing means, in practice, that it is not necessary to store your data. The data are stored and accessible online. The cloud is a highly secure physical location – called the Datacenter – located outside the corporate headquarters, which hosts many servers on the network that serve all users. By taking advantage of the support of a provider such as SOD, it is possible to relocate hardware and software resources in a datacenter and take advantage of the benefits that derive from it.
Cloud solutions for small businesses
Cloud computing naturally has different implications for small businesses than individuals or large companies. This is due to the fact that the user’s needs vary considerably. Both as a type of infrastructure required and as a specific service.
In fact, various main cloud computing options are available to meet various needs: infrastructure as a service (IaaS), platform as a service (PaaS), software as a service (SaaS) and backup as a service (BaaS).
If you think of cloud service models as a pyramid, the IaaS is at the base, because it allows the existence of remote infrastructures. PaaS is the next or intermediate level, which allows users to create infrastructure-based applications. SaaS and BaaS are at the top level providing end users with complete and immediately functional products and services.
Cloud solutions for small businesses are typically SaaS and BaaS solutions.
Common examples of SaaS cloud solutions for small businesses
SaaS-type online solutions include professional versions of apps also used by private individuals, such as Hootsuite, Shopify, Mailchimp, G suite and many others. But of course, specific cloud solutions for small and medium-sized businesses go beyond these familiar examples, and help increase productivity or facilitate marketing and sales.
Other rather important solutions for small and medium-sized enterprises are cloud backup and online storage. This is because, regardless of their size, companies today must manage an ever larger amount of data, and they must also do it securely.
In terms of security, it is also good to specify that a backup is not simply a synchronized folder. In fact, it often happens that online storage services are misunderstood and considered a backup method.
Professional tip: to protect your data you should have backup functions that allow you to restore everything you need to pick up where you left off before a data loss occurs.
Our advice is always to contact professionals not only for the purchase, but also for advice. In fact, the available solutions are manifold and offer functionality that may not be necessary. This is where a managed service provider (MSP) comes in, such as Secure Online Desktop. We can help you in choosing and setting up the ideal infrastructure for your specific case.
Why choose us
Small businesses are often challenged to understand and manage the complexity of IT systems, with the risk of finding themselves stuck because they are out of their knowledge. An MSP can help, thanks to the experience gained in the field. But it’s better if the company is local.
In fact, if it is true that small businesses can easily access many cloud solutions, adoption is not always easy. Being able to turn to professionals who are based in their own territory offers that additional level of tranquility for those who deal with local professionals. The initial setup, the specific choice of functionality and the initial size of the service, are all variables that are easily misrepresented by non-professionals.
An overview of the key solutions
The services we offer give greater value to small businesses. Not only because they are customized solutions, but also because we have clear what their needs will be in the future, thanks to our experience. We can therefore advise in advance how to move when the company starts to grow.
By contacting us, the customer will be able to concretely plan the growth of his company and infrastructure. Starting from the immediately necessary solutions, up to the planning of the specific ones based on the expected growth and possible unexpected events.
[btnsx id=”2931″]
Useful links:
Modern Data Protection
How to Completely Safeguard Businesses – with Ease
Simplify is often a valuable mantra of success. Yet in a complex and ever-evolving IT environment, it isn’t necessarily the go-to approach for service providers. In the case of data protection, simplification may not only seem unlikely, but potentially unwise. Fortunately, certain innovative cloud technologies now make it simple for companies to scale their infrastructure and defend that growth with efficient backup and recovery solutions.
 Know your enemies
Know your enemies
Human error is as damaging as ever and natural threats such as fire and flood still persist. Meanwhile, cyber threats are growing in number and complexity. Whatever the cause might be, if the lights go out for even an hour, companies are at risk.
|
43% of ransomware attacks are aimed at SMBs (1) |
$8,58 1per hour is the average cost of downtime (2)
|
(1) Small Business Trends (2) The Aberdeen Group
 Modern Data Protection – Shore up defenses
Modern Data Protection – Shore up defenses
The best defenses are usually based on a layered data protection strategy. First, you start with standard approaches, like passwords and encryption, traditional anti-virus protection and mobile wipe.
Then you secure everything, from emails and endpoints to servers, with a backup solution that actively protects against ransomware – so even customer backups are safe.
Secure cloud backup provides the last line of defense by protecting a business’ bottom line. Following the 3-2-1 rule of backup (creating three copies of your data, on two types of storage, with one located off-site) keeps your files safe and avoids the worst-case scenario – bankruptcy – should a disaster strike and destroy your local copies.
 Embrace efficiency
Embrace efficiency
With the emergence of the cloud, today there are even more solutions available to enhance business productivity. While that means you also have more systems and data to protect, it doesn’t need to be a problem. When it comes to data protection, the cloud can streamline and strengthen defenses without crippling your customer’s budget.
 Use one comprehensive solution
Use one comprehensive solution
With the right backup solution, it’s easy to ensure complete data protection – including protecting virtual and mobile systems – so you no longer need to independently monitor and secure data across multiple environments. Modern solutions also let you:
1. Support more customers with centralized backup and recovery management
2. Experience unprecedented flexibility to choose any solution for any customer need
3. Protect all data seamlessly and remotely, in any location and any environment
4. Rest easy knowing the entire infrastructure, across multiple business locations, remains secure
 Enjoy instant gratification
Enjoy instant gratification
The cloud can offer a complete defense that scales as your customers’ businesses do. Just add-on cloud-based disaster recovery services and you can have businesses running again instantly. It’s that simple.
Modern Data Protection
[btnsx id=”2931″]
Read more:


subscription
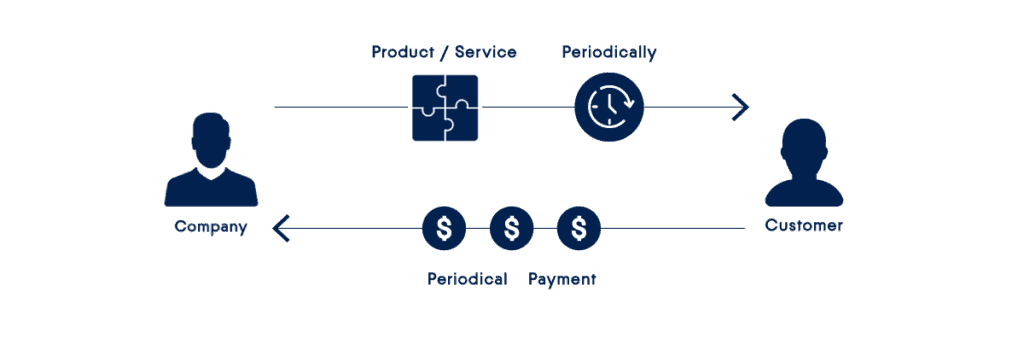
Subscription is a convenient way to receive updates, products or services on a regular and ongoing basis. This business model has stood the test of time. Over the years, satisfied customers have used regular services by subscribing news, magazines, CDs, wine and even opera tickets. And then the cloud arrived. The cloud has made IT complex easy and cheap, thanks to the familiar service delivery subscription model.
Today, public cloud computing services have revenues of $ 246.8 billion. By 2020, Gartner says, cloud adoption strategies will affect over 50% of IT outsourcing contracts. Service providers are rushing to get on board.
Subscription
The subscription is an agreement to regularly receive products or services by paying in advance. It has become a default business model for service providers. Even those service integrators who have made their name by selling individual software licenses are currently switching to a subscription or a software-as-a-service service delivery method to stay alive and grow their customer base.
For customers, the subscription is based on practicality, scalability and economy. The consumption model of the OpEx-based subscription service beats the traditional CapEx model in all ways. Instead of spending hundreds and often thousands of euros on hardware devices and software licenses (and therefore worry about maintenance and upgrades), companies pay a manageable monthly fee just for what they use and only for the service they need.
Subscription models
There are two popular subscription models designed to attract new customers allowing them to try the service before engaging in a full subscription.
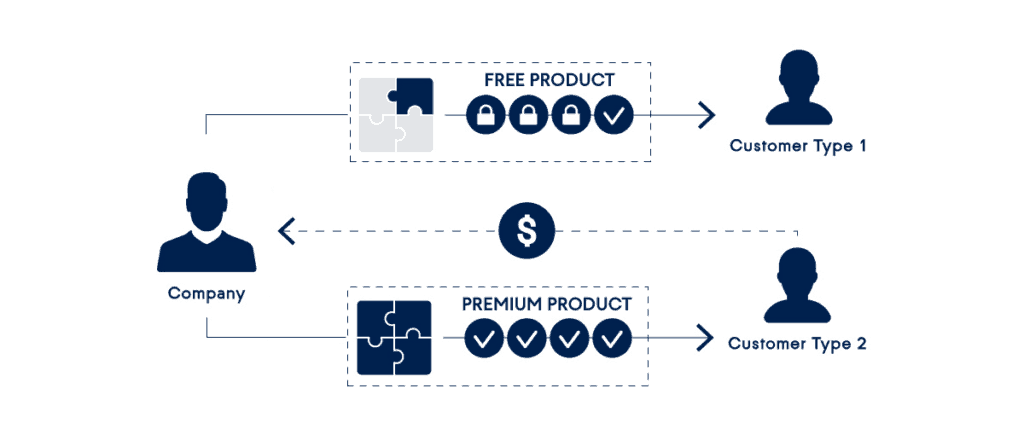
Freemium
A freemium business model offers a free basic service and additional paid features. This has become one of the dominant business models in the mobile app market and is widely adopted by cloud-based service providers. LinkedIn, Dropbox, Yammer and millions of other vendors have adopted this model, using free features as a powerful marketing tool. Users are more likely to direct the service to others when it’s free and easy to use. There are also signs that the freemium model is even more successful than the 30-day trial because it relieves customers from the cumbersome cancellation process when they are trying out the service for the first time.
As with the Acronis Cloud Backup service, the Freemium option allows you to have a free plan for a computer with local backup storage and then charge a fee for additional services such as cloud storage and other devices.
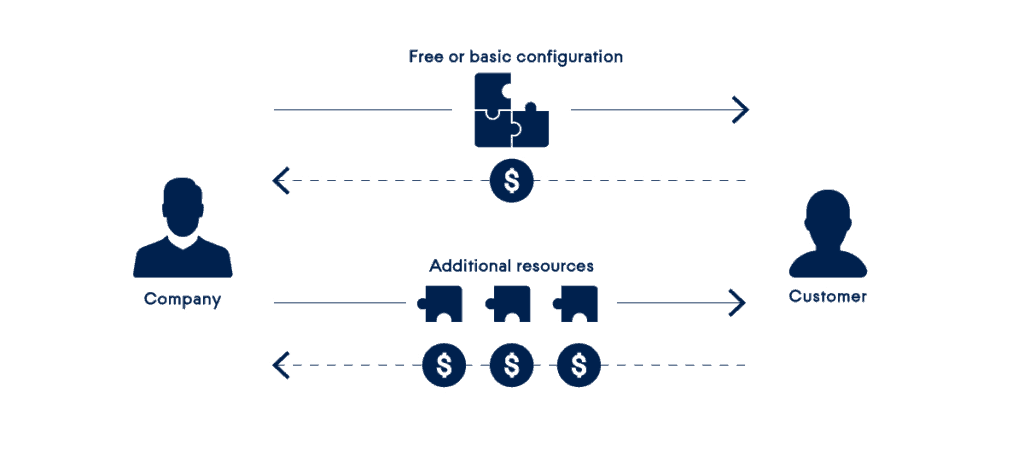
Bait and Hook
This subscription business model offers to offer a basic service at a low price, or even free, and to charge the full price for additional resources. The origin of this subscription method is often attributed to Gillette, a razor company that is known for selling cheap razor kits and expensive blade refills. Today this model is widely used by mobile phone companies (free telephone with a long-term service plan), printer manufacturers (cheap printers, expensive ink) and many other companies where most of the revenue comes from consumables .
With the Acronis Cloud Backup service, on the other hand, you have a free plan with a limited amount of storage space in the Cloud. This will allow customers to register and try the fully functional service before purchasing additional Cloud storage to meet their needs. In this section you can consult the complete list of demo services that Secure Online Desktop makes available to its customers.
Acronis Cloud Backup
The Acronis Cloud Backup service is specifically designed to meet the ever-increasing needs of customers oriented to the above-mentioned subscription models.
[btnsx id=”2931″]
Useful links:
A Hybrid Cloud Backup Solution for System Integrator and reseller
BaaS | Cloud Backup | Backup as a Service
New Acronis Cloud Backup model for end users and new reseller plan
How to have your computer network under control

BaaS (Backup as a Service) is the service that allows your company to save a copy (off-site copy) of data in Cloud. In this way, you can store your information in a safe place and then restore it at any time in case of disaster.
BaaS is one of the ways to implement backup 3-2-1 rule.
Secure Online Desktop provides its customers with two different ways to implement BaaS to offer a range of different options based on different business needs.
[btnsx id=”2931″]
Backup as a Service
Veeam Cloud Connect
The first BaaS (Backup as a Service) solution uses the well-known Veeam technology, widely used by millions of customers around the world, to extend its Veeam local installation to Secure Online Desktop Cloud. The related service is called Veeam Cloud Connect and allows Veeam users to select Secure Online Desktop as a cloud service provider directly from the Veeam console via the “BACKUP INFRASTRUCTURE -> ADD SERVICE PROVIDER” panel or by searching it with the “FIND SERVICE PROVIDER” link.
Pros and cons of the Veeam Cloud Connect solution
Pros:
1) No installation – No additional software or hardware devices are needed in the company;
2) Simplicity – The customer can turn on Cloud Provider functionality from the Veeam Backup & Replication console with a simple click;
3) No new console – You will not need to use a new tool or access additional consoles because all Cloud backups are perfectly visible within the already existing Veeam Backup & Replication console;
4) No VPN – There is no need to establish any additional encrypted channel between the client and the Secure Online Desktop as communications are encrypted through SSL during transit and are encrypted to the source with AES algorithm.
5) WAN Accelerator – With Veeam’s WAN accelerator capability, you can optimize backup communications to reduce time and optimize Internet bandwidth usage.
Cons:
1) It is necessary to have the Veeam solution already in the company;
2) Only the devices supported by the Veeam solution can be protected from backup.
[btnsx id=”3902″]
Acronis Cloud Backup
The second BaaS solution uses instead of Acronis technology and its Anydata engine. Similarly to the first, this service allows you to have an off-site copy on our Cloud and to perform full recovery (the entire virtual machine in case of virtualized environments) or partial (the single file or folder) of your data with a simple click.
Pros and cons of the Acronis Cloud Backup solution
Pros:
1) No other backup software is required – Within the service, the software agents needed to operate with Cloud Backup System will be provided. This way the service can also be used for local copies;
2) Full Protection – Acronis Cloud Backup covers many types of devices, applications, and operating systems including mobile devices;
3) No limit on systems to be protected – The service is billed only on the basis of the storage size in Cloud without any limit on the number of systems to be covered by backup;
4) Local backups – The software agents provided by the service and its backup policies allow you to keep backup over even on any local storage at your site without any additional cost.
Cons:
1) It is necessary to install or distribute agents on all systems that you want to cover from the service.
[btnsx id=”4193″]
Customers
Twitter FEED
Recent activity
-
SecureOnlineDesktop
Estimated reading time: 6 minutes L'impatto crescente delle minacce informatiche, su sistemi operativi privati op… https://t.co/FimxTS4o9G
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The growing impact of cyber threats, on private or corporate operating systems… https://t.co/y6G6RYA9n1
-
SecureOnlineDesktop
Tempo di lettura stimato: 6 minuti Today we are talking about the CTI update of our services. Data security is… https://t.co/YAZkn7iFqa
-
SecureOnlineDesktop
Estimated reading time: 6 minutes Il tema della sicurezza delle informazioni è di grande attualità in questo peri… https://t.co/tfve5Kzr09
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The issue of information security is very topical in this historical period ch… https://t.co/TP8gvdRcrF
Newsletter
{subscription_form_1}© 2024 Cyberfero s.r.l. All Rights Reserved. Sede Legale: via Statuto 3 - 42121 Reggio Emilia (RE) – PEC [email protected] Cod. fiscale e P.IVA 03058120357 – R.E.A. 356650 Informativa Privacy - Certificazioni ISO