Estimated reading time: 13 minutes
Vishing is a particular type of phishing that uses VoIP (Voice over IP) technology to carry out attacks. Unlike traditional landline telephone services, with VoIP technology it is possible to carry out telephone conversations using the Internet connection.
Hackers often use VoIP in their vishing attacks because this allows them to spoof their caller ID with great ease. Posing as an employee of a legitimate entity, such as a bank, the police or a well-known company, Hackers try to obtain personal and financial information of their victims.
With the information obtained it is possible to access a bank account and empty it. Furthermore, it is possible to commit fraud, scams and other crimes using the identity of the victim. Identity theft is a crime that has been on the rise in recent years, which is another reason to inform yourself and stay alert.
Vishing: how to recognize the attack
Vishing attacks usually use automatic text-to-speech systems to redirect the victim to a telephone number controlled by the hacker, but this does not exclude the possibility that a hacker could engage in a real conversation with his victim. The information most commonly targeted by vishing attacks is bank account data. However, many times, hackers also try to obtain access credentials to well-known services such as Microsoft, Apple or Google.
Using social engineering, hackers carrying out vishing attacks trick their victims into extorting money. Generally, scammers attempt to create a sense of urgency or try to alter the emotional state of their victims. This is to force you to pay quickly and without thinking deeply about what is happening.

Vishing: common attack patterns
Vishing attacks can be different from each other, although they always have common goals. A scammer who uses this type of attack could disguise his Caller ID by pretending to be an authoritative person or any known person. They may also leave pre-recorded messages containing threats in their victims’ email inboxes. Not just emails, hackers could also exploit SMS to carry out their scams, as in cases of smishing.
Scammers usually approach their victims by posing as people of authority or exploit the victim’s personal relationships. Below you will find a list of the most commonly adopted scam schemes.
Most common Vishing attacks
Debt collection agency scam
The scammer pretends to be an official of a debt collection agency. The scammer threatens legal consequences or even arrest if the victim does not pay his debts, even if the victim actually has no debt.
Romance scams
the hacker pretends to be a love interest for his victim who he meets on a dating app or site. He or she may sometimes pose as an old flame from the past who urgently needs money for some family or medical reason.
Tech support scam
The scammer poses as a tech support employee and claims there is a serious technical problem on the victim’s computer. The scammer, in this case, uses fear and a sense of urgency to gain remote control of the victim’s computer. It will then install malware passing it off as diagnostic software. Once you gain remote control of your computer, you can access files or any personal information stored on your computer.
There are real companies that live with this type of “business” in Asian countries. Furthermore, there are known creators and white-hat hackers on YouTube who intercept these scammers and try to carry out reverse (social) engineering to trap these criminals. Some of these creators have achieved remarkable results, causing some of these scammer companies to shut down.

Business and investment scams
Scammers pose as financial experts and convince victims to pay sums of money for investments. Scams centered on cryptocurrencies have been spreading a lot lately, driven by the utopia of making a lot of money in a short time.
Charity scams
Scammers pose as members of charities to convince victims to donate to their cause. These fake organizations don’t actually do any charitable work and the money donated goes directly to the scammers. It is very common for them to use photos of children or people suffering from illnesses to appeal to the human sense of compassion.
Insurance scams
Using the information they have on the cars registered to their victims, they try to offer them advantageous insurance offers. With this strategy it is possible not only to collect other personal information on one’s victims, but also to defraud them financially if the victim decides to purchase the policy proposed by the hacker.
How is it possible to defend yourself from vishing
It is often difficult for victims to recognize vishing attempts because it is not unusual for banks and other entities and organizations to request sensitive information by telephone. Vishing attacks are increasingly sophisticated and can include pre-recorded messages and other ways to increase credibility.
We at SOD suggest several ways to detect vishing attempts, below are some strategies to adopt to recognize this type of attack. The best defense against these frauds, as in the case of phishing, is to know how to identify them immediately and not to spread any personal information by telephone, especially if the request is unexpected.
You should always be careful when using poorly traceable forms of payment such as cash, gift cards and prepaid cards. Additionally, you should pay particular attention to the characteristics of the phone call, such as the tone or accent of the person making the call or the urgency of the call. These can be alarm bells that signal the possible presence of a case of vishing.
To avoid falling victim to vishing, it is advisable to never answer calls from unknown numbers. Another useful tip is to never comply with requests from a suspicious person, such as pressing buttons when asked or answering suspicious questions.
If you are not sure about a number from which calls are received, you can always do an internet search and see if the number belongs to a service we use that is perhaps contacting us with a real problem.
In many countries, social media is used to communicate with the public. Many platforms use protection systems to verify the actual authenticity of government and banking profiles, therefore you should never trust an entity without these badges.

Conclusions
The types and mechanisms of intrusion are increasingly sophisticated. Phishing, smishing and vishing attempts are now a constant in our lives, continually putting our personal data at risk. As we have seen in many situations, data is the most valuable commodity on the internet, so protecting it must be a priority!
To concretely defend ourselves, the use of professional tools is the only safe path to take. Our SOCaaS service protects against vishing but is also a complete tool that guarantees corporate security, identifying and blocking all kinds of threats.
Additionally, SOD also organizes ethical attack campaigns to test the resilience of a company’s employees. After the attacks, the data collected is used to organize training sessions geared towards the specific characteristics of the company and the resilience shown by employees.
For information on the ethical phishing services we offer or to better understand how SOCaaS could be an ideal solution for your company, do not hesitate to contact us by pressing the button below.
Useful links:

Cyberattacks are numerous and do not distinguish between companies and individuals when targeting a target. You’ve most likely heard the term “cyber threat” in the media before, but what exactly are we talking about? Other ways you may have heard this are “cyberthreat”, “cyberattack” or similar.

What is a Cyber Threat?
Today the term “cyber threat” is used predominantly in the world of information security.
A cyber threat is a malicious act conceived with the purpose of damaging systems, stealing data or any purpose that has the purpose of causing damage of any kind. Viruses, data breaches and DDoS attacks are included. Even if the threat is virtual, what is real is the attacker’s intent as well as the potential impact. While many cyberattacks are mere nuisances, some are quite serious. Some even potentially threaten human lives.
The potential impact that these kinds of attacks can have is often underestimated. Most of the time, the attacks are easily identifiable and do not pose much risk. Instead, other times it happens to come across some more sophisticated threats, difficult to identify, which represent a big problem even for many companies.
Cyber threats are a major concern for businesses. Cyberattacks can lead to power outages, government equipment failures, and breaches of state secrets. They can manipulate telephone and computer networks or, as in the case of ransomware, they can cripple entire systems by making data inaccessible.
Every day new companies and organizations set foot in the digital world with awareness of the risks associated with their technological infrastructures. In some cases, cyber threats are underestimated and this often means great economic and image damage for the company that has underestimated cyber threats and security.
The increase in IT-related risks is real, as are data security solutions. The best thing to do is to take the necessary safety measures right away.
Types of Cyber Threats
The types of cyber threats are numerous, and it must also be considered that they are constantly evolving. The intent of hackers is usually to secure an economic gain by carrying out sabotage, espionage or data theft operations. As a result, they can be expected to do everything possible to achieve their ends.
Virtually every cyber threat falls into one of the following ten types of risks. Hackers have an abundance of options to choose from in order to operate. Furthermore, computer literacy is all in all poor, so hackers often have an easy time, especially for small local realities.
The 10 most common types of computer threats
Malware
It is a type of software that executes a malicious command on a device or within a computer network, corrupting data or taking control of the system.
Phishing
Phishing is an e-mail attack that consists of tricking the recipient into revealing confidential information or inviting him to download malware by clicking on a link in the body of the message. These are real scams, which we have talked about extensively in other articles. Often they don’t even involve great IT skills on the part of the attacker, just a little social engineering.
Vishing
Vishing is a more sophisticated form of phishing in which the hacker uses VoIP technology to contact the victim, attempting to trick them. There is also a variant that instead uses text messages to attack, it is called smishing.
Man in the Middle
As the name suggests, this type of attack refers to when a hacker intervenes in a conversation posing as one of the two parties, with the aim of stealing sensitive information. What we often don’t think about is that the conversation is between two machines and therefore not immediate to monitor.
Trojan viruses
The origin of its name is inspired by the famous Trojan Horse of ancient Greece. Trojan is a type of malware that infiltrates a computer system by hiding its true nature. For example, it could impersonate known software and then release malicious code once inside the host device.
Ransomware
Ransomware is an attack that uses encryption to make information on a system inaccessible. The aim is to demand a ransom in exchange for being able to access the data again. Possibilità che a volte, in realtà, non è nemmeno assicurata.
DDoS attack
It occurs when the attacker uses many devices to overload a target, such as a website, with requests, causing it to crash or become instabilities.
Attacks on IoT devices
This is an increasingly popular attack due to the nature of the targets. Devices such as sensors or industrial plants connected to the network are vulnerable to multiple types of cyber threats. The hacker could take control of the device and then later use it in a DDoS attack. Alternatively it could steal the information present in the device itself obtaining important data to continue the attack. Given their number of frequently out-of-date operating systems, IoT devices are a very attractive target.
Malware in mobile applications
Phones and tablets are just as vulnerable to malware as any other device. È possibile inserire malware all’interno di app, nei siti web o nelle e-mail sfruttando il phishing. Once compromised, a mobile device can provide access to personal information, location data, and financial accounts.
A recent example of this type of eventuality is Pegasus software, which is used to monitor and collect data from journalists around the world. (Source: The Guardian)
Practical defense and prevention solutions
Cyber threats are always expanding and improving. Millions of them are created every year, many of them follow the aforementioned characteristics, but others are technologically more complex and more powerful.
Fortunately, however, there are also more and more highly qualified companies in the field of IT security that offer cutting-edge tools and services that help prevent, identify and promptly block all kinds of IT attacks.
Threat detection tools
Threat detection tools are an essential part of a company’s cybersecurity technology stack. Threat detection is also the first defense against any Cyber Threat.
Specific solutions, such as the use of a SOCaaS, for example, are of vital importance for safeguarding an IT infrastructure, thanks also to the integration of the SIEM engine which includes UBA and UEBA, guaranteeing complete control also over the users.
Another useful tool is definitely ACP. Acronis Cyber Protect is a solution that integrates data protection and management to safeguard your endpoints, data and systems. Its automation capabilities provide unparalleled protection, enabling businesses to increase their productivity and reduce risk.
Vulnerability Assessment & Penetration Test (VA-PT)
Services like VA & PT are field tests that test the infrastructure in a concrete context. Our teams of white hat hackers find vulnerabilities within the system to point the finger at weaknesses to fix.

Conclusions
We have learned what a cyber threat is and its most common types, also discovering which solutions can be adopted in order to guarantee better corporate and employee safety.
What countermeasures has your company taken to protect your safety? If you would like more information about it, you can contact us by pressing the button below. We offer ad hoc services and solutions to strengthen corporate defenses.
Useful links

Estimated reading time: 5 minutes
Every year the number of attacks that threaten the security of devices, computer systems, servers and network infrastructures is growing steadily. This is done by taking advantage of the vulnerabilities present in these systems. Among the many types of attacks, particular attention must be paid to the pass the ticket (PTT) attack.
With a pass the ticket attack it is possible to take advantage of the Kerberos network protocol, present in all major operating systems, to access a user’s session without having his login credentials. An attack of this type can be difficult to detect and is usually able to bypass the most common system access controls.

Pass The Ticket: what it is and how it works
Kerberos
Before understanding in detail what a PTT attack is and how it works, it is advisable to clarify the Kerberos network protocol since an attack of this type uses this protocol. Kerberos is a network protocol designed by MIT in the 1980s and became a standard IETF in 1993. It is used for strong authentication between different terminals through a symmetric key encryption system, without transmitting any passwords.
The advantage of using the Kerberos protocol lies in its strong authentication system between client and server. This makes it very effective against phishing and “ man in the middle ” attacks.
Kerberos is integrated into all major operating systems belonging to well-known companies such as Microsoft, Apple, Red Hat Linux and many more.
With a pass the ticket attack it is possible to exploit Kerberos authentication to gain access to a user account. The consequences that such an event could entail are not are to be underestimated. Among the many imaginable scenarios, for example, there could be the possibility that the compromised account enjoys high administrative privileges thus guaranteeing the hacker full access to resources.
The attack
A pass the ticket attack allows you to gain privileged access to network resources without having to use any user passwords . Here’s how: In Active Directory, a Ticket Granting Ticket (TGT) serves to prove that a user is just who he says to be. Through some tools and techniques, a hacker could collect these tickets and use them to request Ticket Granting Services (TGS) in order to access resources present in other parts of the network.
A PTT attack could involve risks even if the compromised account does not have particular administrative privileges since the hacker, through the Lateral Movement, may be able to gain access to other accounts and devices.
The difference between pass the ticket and an attack pass the hash lies in the fact that the former exploits TGT tickets that have an expiration of a few hours, while the latter uses NTLM hashes that change only in case a user decides to change his password. A TGT ticket must be used within its expiration time or renewed for a longer period of time.
How to Defend and Prevent a Pass The Ticket Attack
Keeping a network and the devices connected to it safe is a very important factor. You must always have protocols and software that are able to guarantee effective protection from all kinds of threats , with up-to-date systems that keep sensitive information safe. Enterprises can take advantage of endpoint detection and response technologies. Local detection of multiple tickets used for the same session will be possible.
Account case without-privileges
In the event of a pass the ticket attack, if the compressed account from which the TGT or TGS was stolen was a low-privilege account, the mitigation could be quite simple. Just reset the user’s Active Directory password. Such an action would invalidate the TGT or TGS, preventing the hacker from generating new tickets.
Case-account with privileges
Conversely, if the PTT attack compromised a privileged account, limiting the damage is much more difficult. In these cases, companies could respond to the attack by resetting the Kerberos TGT service to to generate a new signing key, making sure to delete the compromised key.
Next you need to drill down into Kerberos logs and Active Directory information to investigate and find out which network resources have been compromised. In this way it is also possible to understand which data may have been stolen. The technology SIEM allows organizations to assimilate, analyze and analyze this data.

Protection from attack
To ensure complete protection of an infrastructure, also preventing pass the ticket attacks, it is good to use valid detection technologies such as UEBA and SIEM. In fact, it is possible to prevent Pass The Ticket attacks by analyzing the behavior of users and entities. The solution UEBA , in these cases, would ensure the quick identification of any compromised account, blocking it in order to mitigate the damage.
Some software SIEM also allow not only to analyze traditional logs but are also able to provide an accurate analysis of security , analyzing the behavior of the network and users in order to detect promptly the presence of any threats to the infrastructure.
Conclusions
We have seen what a pass the ticket attack is and how companies can adopt specific solutions to intercept the dangers and anomalies of an entire IT infrastructure. This allows us to mitigate threats more effectively.
A complete solution, as we have seen, involves constant and granular communication monitoring . The solution we propose for this purpose is a SOCaaS .
If you want to know our dedicated security services, do not hesitate to contact us. You can use the button below, we will be happy to answer any of your questions.
Useful links:

Estimated reading time: 6 minutes
Cyber Threat Analytics applications monitor security logs and the network to promptly detect any malware infections (for example, attacks zero day e i ransomware), the compromise of the system, the activities of “ lateral movement ”, pass-the-hash , pass-the-ticket and other advanced intrusion techniques. The use of a SOCaaS allows to extrapolate data from sources such as firewalls, proxies, VPN, IDS, DNS, endpoints, and from all devices connected to the network with the aim of identifying harmful models such as “beaconing”, connections to generated domains digitally, actions performed by robots and all anomalous behaviors.
Our system SOCaaS is equipped with artificial intelligence that enriches and transforms events SIEM, so you identify threats across your entire IT environment, including business-critical applications.
What are the-advantages at the enterprise-level?
The use of a SOCaaS. Below is a list with only some of the advantages that the use of SOCaaS can entail rapid detection of violations, reducing the impact of these. Additionally, a SOCaaS provides comprehensive threat responses and investigations, decreases monitoring and management costs, as well as compliance costs.
The use of a SOCaaS also allows you to receive quantified and non-subjective reports on threats and risks.

SOCaaS use cases
After a general overview of the advantages that the use of SOCaaS could offer to the company, let’s see in what contexts it is normally used .
A SOCaaS consists of elements that are very suitable to be applied in case of abnormal execution of applications, as well as in the analysis of bot traffic to a malicious website.
In other cases, SOCaaS identifies unusual DNS queries, a possible remote command and control activity, analyzes the spikes in bytes to external destinations and then also checks the traffic, relating it in an application / port context.
Other scenarios in which the use of SOCaaS is ideal are the detections of exploits, sessions of unusual duration, but also connections to IPs or blacklisted domains and anomalous activity in general.
Finally, it can also detect targeted SPAM attacks and phishing attempts.
Threat Models
By analyzing threat indicators it is possible to detect correlated behaviors on multiple data sources, to also detect all those threats that usually go unnoticed. Multiple threat indicators occurring in a scheme and involving similar entities tend to present a greater risk of posing a real threat.
The Threat Models define these patterns and combine threat policies and indicators to detect related behaviors across multiple data sources, identifying threats that may go unnoticed. Below are some of the more common Threat Models that are included in the use of a SOCaaS
Lateral Movement Detection
This Threat Model detects the possible scenarios of “ lateral movement “, used by attackers to progressively spread across a network in search of key resources and data. The signs of such an attack can be varied and we can divide them into three categories: Abnormal authentication, suspicious privileges, abnormal process.
Abnormal authentication is usually detectable by some clues. For example if an account accesses a host that has never been reached before. Or if explicit credentials are used on multiple hosts, or if a suspicious authentication type / process is detected.
Concerning suspicious privileges, here are some indicators detectable with the use of a SOCaaS:
- abnormal provisioning activity
- suspicious escalation of privileges
- abnormal access to network share objects
An abnormal process is detected in this way through the use of a SOCaaS: an unusual process code, or the suspicious creation of scheduled tasks. Alternatively, suspicious changes to the registry settings may be detected.
Detection of compromised hosts
This model is employed in the use of SOCaaS to detect hosts showing signs of infection and compromise by relating host and network based anomalies to the same entity.
A possible alarm is given by anomalies in outgoing traffic . This occurs when traffic goes to random domains or known malicious hosts. In other cases, however, an abnormal number of domains contacted is another alarm bell detectable through the use of a SOCaaS.
anomalies in the endpoint are found when rare processes or suspicious use of ports or protocols by the process itself are found. One possibility is also to detect an unusual agent.
APT detection using a SOCaaS
Detection APT detects attacks on health care networks , where the attacker’s aim is usually to obtain a unauthorized access to a network with the intention of remaining undetected for an extended period.
This includes phishing attempts , detection of a network scan or circumvention of controls. In the delivery phase, however, traffic to random domains, an anomaly in DHCP traffic or traffic destined to known malicious hosts may be identified.
During an exploit , the indicators can be: the detection of activity from terminated accounts, anomalous DNS traffic, but also a suspicious authentication process. Another possible indicator identifiable with the use of SOCaaS is an anomaly in the speed of the network.
Through the use of a SOCaaS, cases of data exfiltration can also be detected. The signals in this case are l ‘Unauthorized upload of data over the network.
Detection model Phishing using SOCaaS
This model is able to detect possible phishing attempts towards users within the organization . We’ve talked about it in other articles as well, and here are some indicators of this type of attack. A wake-up call is definitely the detection of known phishing campaigns. It is also not uncommon for spear phishing attacks to be detected.
The use of a SOCaaS is also able to identify possible phishing attempts or persistent phishing campaigns, thanks to the comparison with emails from senders / domains / IP addresses known in the blacklists. As usual, beware of suspicious email attachments, but the use of a SOCaaS could automate, at least in part, the checks.
It is then possible to identify outbound traffic anomalies , for example that towards random domains, which is also a possible phishing signal. Classic traffic to malicious hosts, an abnormal number of rare domains accessed, can also be indicators.

Host / Account Enumeration on LDAP
Usually used to identify potential assets or account enumerations on the network by malicious entities.
Running suspicious processes
- Abnormal process / MD5 detected
- Use of possible sets of AD (Active Directory) enumeration tools
- Detected use of malicious tools and utilities
Network scanning
- Possible AD accounts / enumeration privileges
- LDAP or SMB service count
- Abnormal number of Kerberos service ticket requests
- Port scanning
Authentication anomalies
- Accounts accessing a host for the first time
- Using never-before-seen accounts on the network
- Abnormal number of failed authentication requests
Reconnaissance followed by potential exploitation
This threat model aims to identify successful network reconnaissance attempts, followed by indicators of exploitation.
External scanning
- Scanning ports from external hosts
- Enumerating hosts from external hosts
Network scanning
- Possible count of AD accounts / privileges
- Enumeration of LDAP services
- Unsolved number of Kerberos service ticket requests
- Spikes in traffic LDAP
- Enumeration of SMB services
Anomalies in processes
- Detection of abnormal processes or MD5
- Suspicious creation of scheduled tasks
- Suspicious changes to registry settings detected
Conclusions
We have seen what are the major SOCaaS use cases, taking a look at some of the most common threat models that it includes in its protection system. For information on malware threat patterns and threat identifiers visit this article.
Using a SOCaaS is a solid and highly valuable business solution, ask us what it can do for your business, we will be happy to answer any questions.
Useful links:

Estimated reading time: 5 minutes
Il cybercrimine, sta mirando sempre più ai dispositivi mobili ed è sempre in continua evoluzione. Sui social network e tramite i nostri contatti personali riceviamo sempre più spesso tentativi di truffe mascherati da semplici inviti. Dai rapporti e dai comunicati della polizia postale possiamo notare come negli ultimi anni stiano aumentando i casi di Smishing, che ogni anno causano consistenti danni economici ad aziende e privati per centinaia di migliaia di euro.

Cos’è lo Smishing
Con il termine “Phishing”, ci riferiamo a tutte quelle attività fraudolente messe in atto dagli hackers con il fine di trarre in inganno un individuo. Altri fini possono essere sottrarre informazioni sensibili e utilizzarle per commettere illeciti di natura fiscale.
Lo Smishing si differenzia dal Phishing per via dell’utilizzo degli SMS come strumento di contatto. Il nome viene proprio dalla crasi di SMS e phishing.
Questa tipologia di attacco solitamente avviene sfruttando l’ingenuità del malcapitato, inducendolo a scaricare dei malware autoinstallanti o invitandolo a compilare dei moduli con le proprie informazioni personali. Questi malware si mascherano da comuni applicazioni, in modo da non insospettire la vittima. Nel caso in cui l’utente rilasci delle informazioni all’interno di queste applicazioni, i dati inseriti verranno automaticamente inviati all’hacker, che potrà usarli a suo piacimento.
Analogie con il phishing
Altre tipologie di Smishing, invece, prevedono l’invio di messaggi di testo apparentemente provenienti dalla nostra banca, da un’organizzazione di credito, da un’azienda o da un individuo che conosciamo, nel quale riponiamo fiducia. Di solito questi messaggi contengono segnalazioni riguardanti presunti movimenti sospetti o problemi per l’accesso ai servizi bancari. Sfruttando la fiducia che un individuo pone nei confronti di una banca, l’hacker conduce la sua vittima verso un sito web fasullo.
Infatti, il testo del messaggio, oltre a contenere un messaggio allarmante per la vittima, contiene anche almeno un link che reindirizza il malcapitato verso un sito fraudolento.
Questo tipo di siti lo abbiamo visti anche negli attacchi di phishing, e sono creati appositamente dall’hacker con la speranza che la richiesta di dati sensibili sia compilata. Questa può essere sotto forma di un form di login della banca, del tutto simile a quello originale.
Dei dati raccolti, poi, possono essere fatte varie cose. Potrebbero essere rivenduti, usati per ricattare la vittima o per rubarne altri account che utilizzano la stessa combinazione di user e password. Quest’ultima eventualità è il motivo per cui le password dovrebbero essere uniche e non condivise con vari servizi.
Come difendersi
Per difendersi dagli attacchi di Smishing, non è necessario adottare sofisticate tecniche di difesa.
Essendo dei tentativi di raggiro, potrebbero essere facilmente evitati ignorando il contenuto dei messaggi fraudolenti. Di fatto questa tipologia di attacco, per poter funzionare, necessita dell’interazione da parte dalla vittima. Senza un’interazione da parte dell’utente, è impossibile attuare questa tipologia di attacco informatico.

Individuare tentativi di Smishing.
Ecco alcune tipologie di messaggi o situazioni sospette a cui fare attenzione e di cui valutare bene la provenienza:
– Avvisi urgenti sulla sicurezza, messaggi che promettono denaro o premi gratuiti, offerte o regali. Questi sono tutti dei campanelli d’allarme. Molto probabilmente si tratta di un tentativo di raggiro. Fare leva su un senso di urgenza è tipico di questi attacchi. Una tecnica simile viene usata nel marketing per fare fretta al cliente e spingerlo ad acquistare.
– Gli istituti finanziari o i commercianti non utilizzano mai gli SMS per chiedere ai loro clienti di aggiornare le informazioni relative al proprio conto personale. Soprattutto, non chiedono mai informazioni sensibili, come ad esempio i numeri di una carta di credito.
Un SMS che contiene questo genere di richieste, probabilmente è un tentativo di Smishing. In caso di dubbi inoltre, è possibile contattare la propria banca per avere spiegazioni in merito alla richiesta, in modo da accertarsi se si tratta effettivamente di un tentativo di Smishing oppure no.
– Evitare di cliccare sui link presenti in un messaggio se non si è sicuri che l’SMS provenga realmente da una fonte attendibile.
– Prestare particolarmente attenzione ai numeri telefonici che sembrano sospetti. Questi numeri spesso sono collegati a degli strumenti che hanno la funzionalità di inviare SMS direttamente da una casella e-mail. I truffatori utilizzano questo sistema per evitare di fornire il loro numero di telefono.
– Mai conservare credenziali d’accesso, dati bancari, o informazioni personali sensibili sullo smartphone. Se si utilizza quest’accortezza, sarà impossibile per un hacker ottenere questi dati, anche se dovesse utilizzare un malware.
Mai salvare nulla su un dispositivo, è sempre opportuno avvalersi di sistemi di archiviazione tradizionali, come carta e penna o la nostra cara e vecchia memoria. Alternativamente, affidarsi a un servizio di gestione delle password come Bitwarden.
– Mantenere sempre la calma, anche se il testo del messaggio dovesse contenere minacce o scadenze. Mai abboccare all’amo.
– Denunciare i tentativi di attacco di smishing alla Polizia Postale. Segnalando queste truffe è possibile evitare che altre persone possano cadere nello stesso raggiro.

Conclusioni
Come abbiamo visto in questo articolo, i tentativi di truffa sono in continua crescita. Fortunatamente però, a nostro supporto ci sono istituzioni che indagano costantemente, bloccando i responsabili di queste truffe. Ricordiamo sempre di fare sempre attenzione ogni qualvolta che si forniscono delle informazioni personali. Bisogna sempre verificare che la fonte alla quale stiamo affidando i nostri dati sia attendibile.
Quando si tratta di un’azienda, tuttavia, consigliamo di prendere in considerazione un servizio per fornire gli strumenti adeguati ai dipendenti per contrastare lo smishing o il phishing. I nostro servizio di phishing etico può aiutare a individuare quali siano le vulnerabilità aziendali. Inoltre, organizziamo dei training ad hoc sulle basi dei risultati dei test per aiutare i dipendenti a saper riconoscere i tentativi di phishing e smishing.
Per saperne di più su come il nostro servizio di phishing etico potrebbe aiutare la tua azienda, non esitare a contattarci, saremo lieti di rispondere ad ogni domanda.
Useful links:
Link utili:

Estimated reading time: 9 minutes
There was a dramatic 1160% increase in malicious PDF files in 2019-2020. It went from 411,800 malicious files to 5,224,056. PDF files are an enticing vector of phishing as they are cross-platform and allow attackers to engage more users, making their scam schemes more credible than a text email with a simple link.
To lure users to click on links and buttons embedded in phishing PDF files, there are five main schemes used by attackers: Fake Captcha, Coupon, Play Button, File Sharing and E-commerce.
Data analysis
Data collected from the platform WildFire by Palo Alto Networks was used to analyze the trends . A subset of phishing PDF samples were collected throughout 2020 on a weekly basis. Over 5 million cases of phishing with PDF were analyzed for 2020 alone and the increase in the incidence compared to the total number of documents sent rose by 1160%.
In particular: in 2019 the total number of files analyzed was 4.5 billion, of which about 411 thousand were found to be malware (0.009%). In 2020, following the analysis of over 6.7 billion documents, 5.2 million were found to be phishing vectors with PDF (0.08%).
Phishing with PDF, the most commonly analyzed methods
Five major phishing schemes have been identified from the dataset and will now briefly analyze them in order of distribution. It is important to keep in mind that files used in PDF phishing attacks often act as a secondary step and work together with their carrier (for example, an email or article containing them).
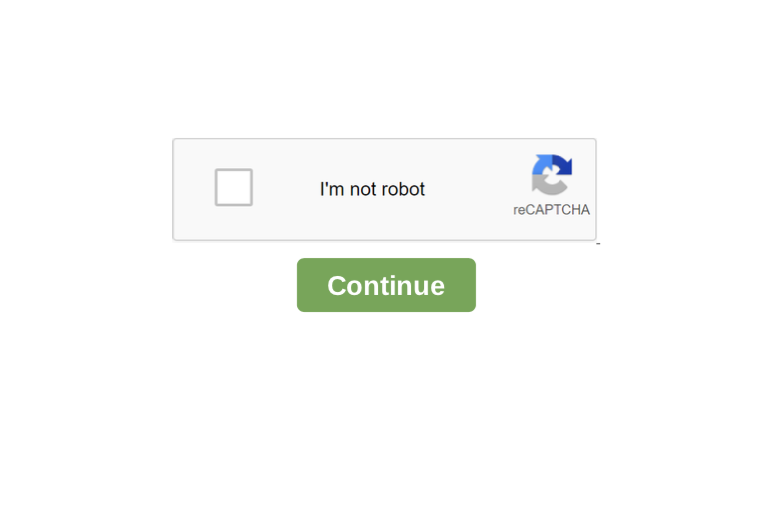
1. Fake CAPTCHA
PDF files Fake CAPTCHA , as the name suggests, require users to verify themselves through a fake CAPTCHA . CAPTCHAs are challenge-response tests that help determine whether a user is human or not.
However, the observed PDF phishing cases do not use a real CAPTCHA, but an image depicting a CAPTCHA test . As soon as users try to “verify” by clicking the continue button, they are taken to a website controlled by the attacker.
The figure below shows an example of a PDF file with a fake CAPTCHA embedded, which is just a clickable image.
2. Coupon
The second category identified are coupon themed phishing PDF files and often used the logo of a major oil company .
A significant amount of these files were in Russian with notes like “ПОЛУЧИТЬ 50% СКИДКУ” and “ЖМИТЕ НА КАРТИНКУ” which translate to “get 50% off” and “click on the picture” respectively. The figure below shows an example of these types of phishing PDF files:

Similar to other campaigns seen in the past, these PDF phishers have also taken advantage of traffic redirection for the reasons mentioned above . Analyzing several of them, it was found that they use two traffic redirectors. The figure below shows the chain of a sample:
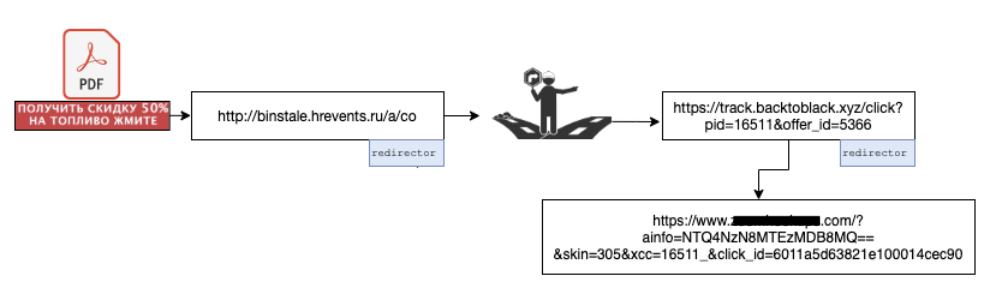
The entry website took us to another website ( track [.] backtoblack.xyz ), on which another redirect was set.
Eventually, you are directed to an adult dating site through a GET request with some parameters filled in such as click_id , which can be used for page monetization. All these redirects occurred through HTTP 302 redirect messages. Research showed that the offer_id parameter of backtoblack [.] Xyz controls which site the user ends up on .
3. Static image with a play button
These PDF phishing scams don’t necessarily carry a specific message, as they are mostly static images with a video play button superimposed, so they look like videos you need to start.
Although different categories of images were observed, a significant part of them used nudity or specific economic / monetary themes as the subject such as Bitcoin, stock charts and the like to lure users to click on the play button.
The image below shows a PDF file with a Bitcoin logo and a clickable play button.
By clicking the play button, as you can guess, you are redirected to another website. In most of the tests carried out, the redirect pointed to https: // gerl-s [.] online /? s1 = ptt1 .
From the domain name, one could assume that the site is also in the realm of online dating. However, at the time of this writing, the site has been removed. Unlike the previous campaign, there was only one redirect involved , and it was noted that all redirects had the following format:
id-6-alphanumeric-characters [dot] sed followed by a main domain, similar to those listed below:
http://pn9yozq[.]sed.notifyafriend.com/ http://l8cag6n[.]sed.theangeltones.com/ http://9ltnsan[.]sed.roxannearian.com/ http://wnj0e4l[.]sed.ventasdirectas.com/ http://x6pd3rd[.]sed.ojjdp.com/ http://ik92b69[.]sed.chingandchang.com/
http://of8nso0[.]sed.lickinlesbians.com/
4. Sharing files

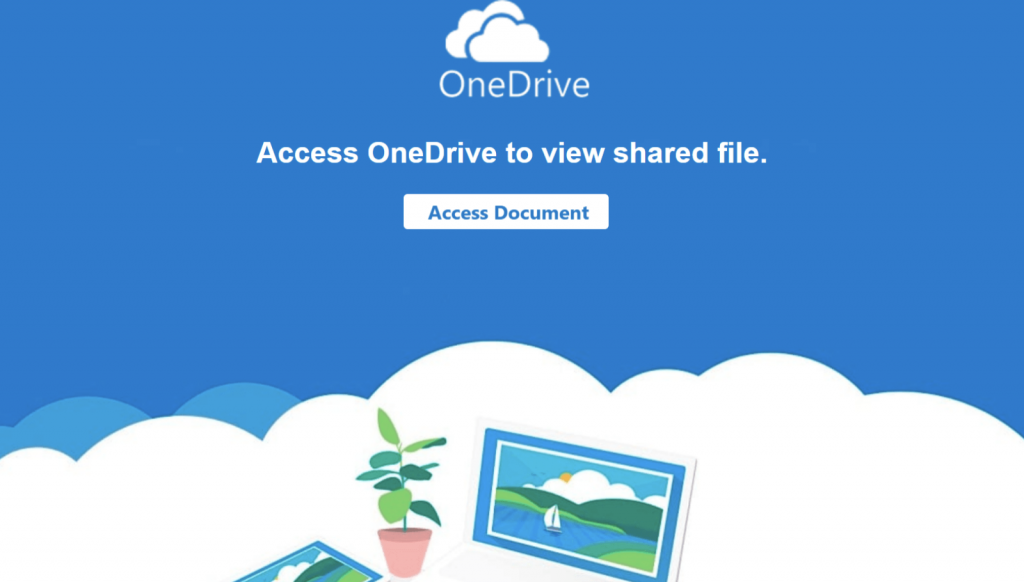
This category of PDF phishing uses popular online file sharing services to grab the user’s attention . They often inform the user that someone has shared a document with them. However, for reasons that may vary from one PDF file to another, the user cannot see the content and apparently has to click on an embedded button or link . The image above shows a PDF with a Dropbox logo asking the user to click on the button to request access.
Below, similarly, an image of a PDF file with a OneDrive logo, prompts the user to click on “Access Document” to view the contents of the file.
As the number of cloud-based file sharing services grows, it wouldn’t be surprising to see this theme grow and continue to be among the most popular approaches.
Clicking the “ Access Document ” button takes you to a login page with an Atlassian logo, as shown below. There are two options to use for logging in: Microsoft email or other email services.
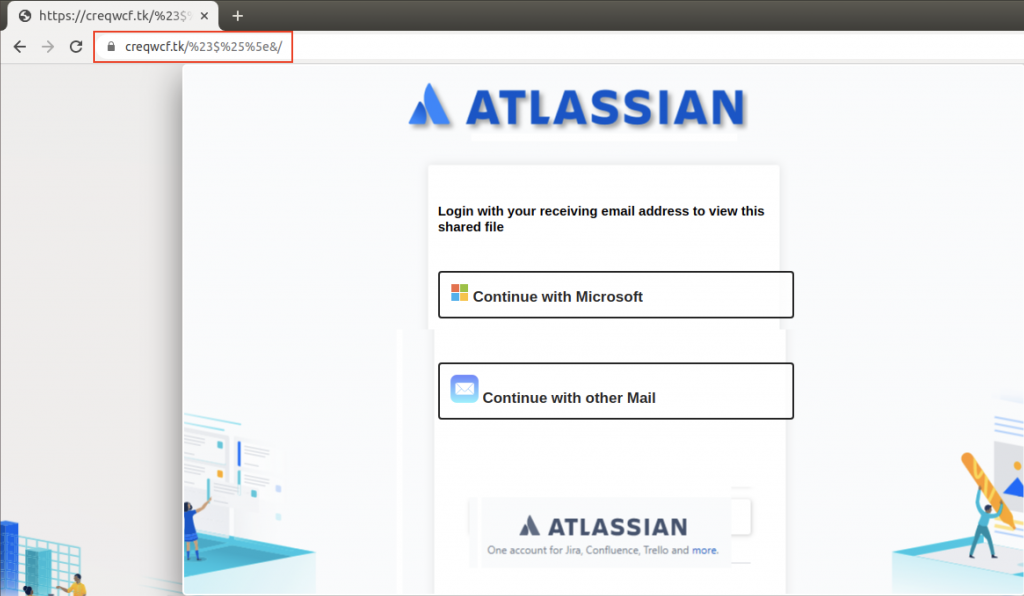
Atlassian Stack is geared towards business, so we assume this campaign was aimed at business users. Each of these links has been designed to resemble a legitimate email login page.
For example, “ Continue with Microsoft ” takes you to a page that looks somewhat similar to the one you come across upon entering the legitimate https://login.live.com , as shown below:
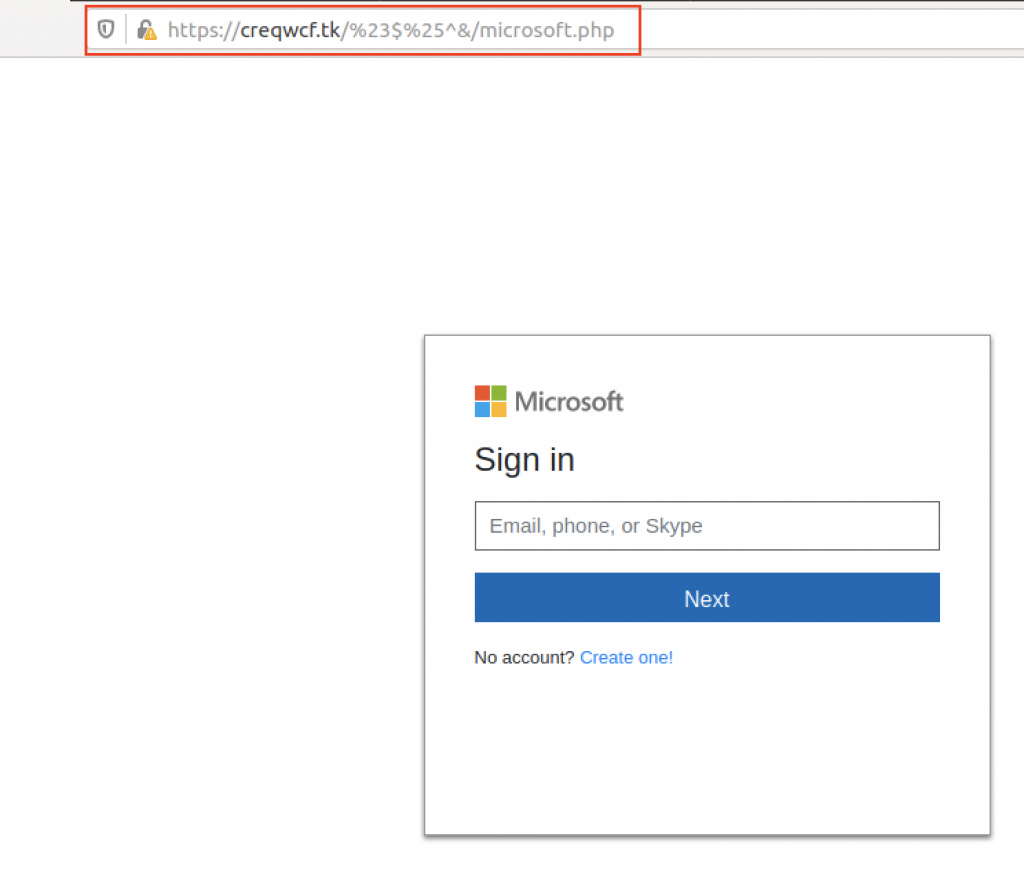
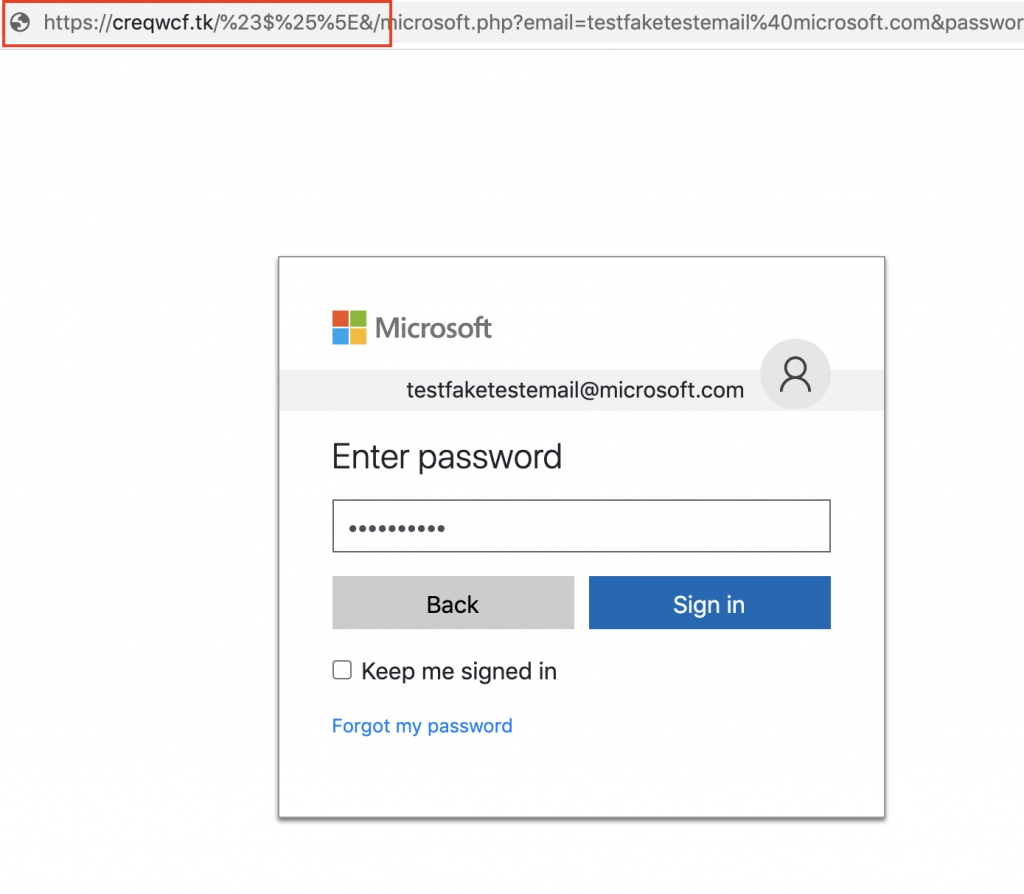
After entering an email address, we proceed to another page that asks us to enter our password.
It was observed that the stolen credentials were sent to the attacker’s server through parameters in a GET request.
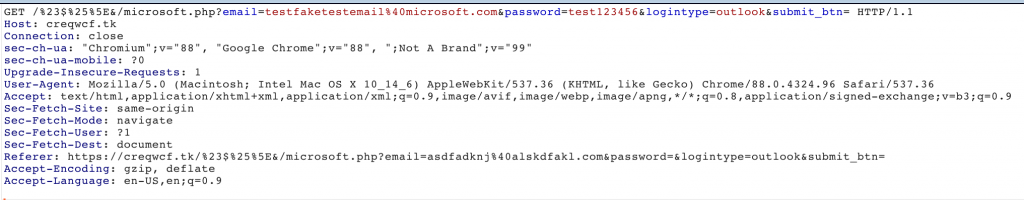
After entering your credentials, you are returned to the first login page.
We would like to point out that, when we visited this site, it was already reported as phishing by major browsers such as Google Chrome and Mozilla Firefox.
However, during the research, we proceeded to test the whole path with fake credentials to further investigate and investigate the method of phishing with PDF.
5. E-commerce
Embedding e-commerce themes in emails and phishing documents with PDF is not a new trend. However, there has been an upward trend in the number of fraudulent PDF files that have used brands of international e-commerce to induce users to click on embedded links.
The image below shows an example of a PDF phishing scam that notifies the user that their credit card is no longer valid and that they must “ update their payment information ” in order not to interrupt. the benefits of Amazon Prime .
Similarly, another image below shows a document that informs the user that their Apple ID account will be suspended if they do not click on the link to update their information.
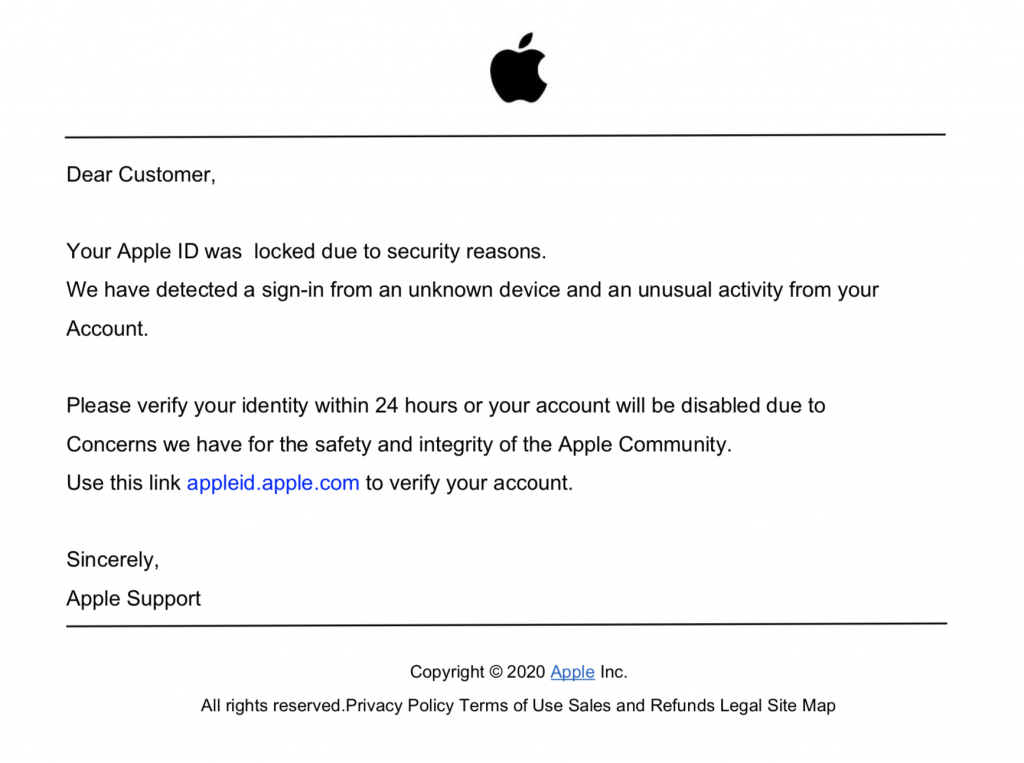
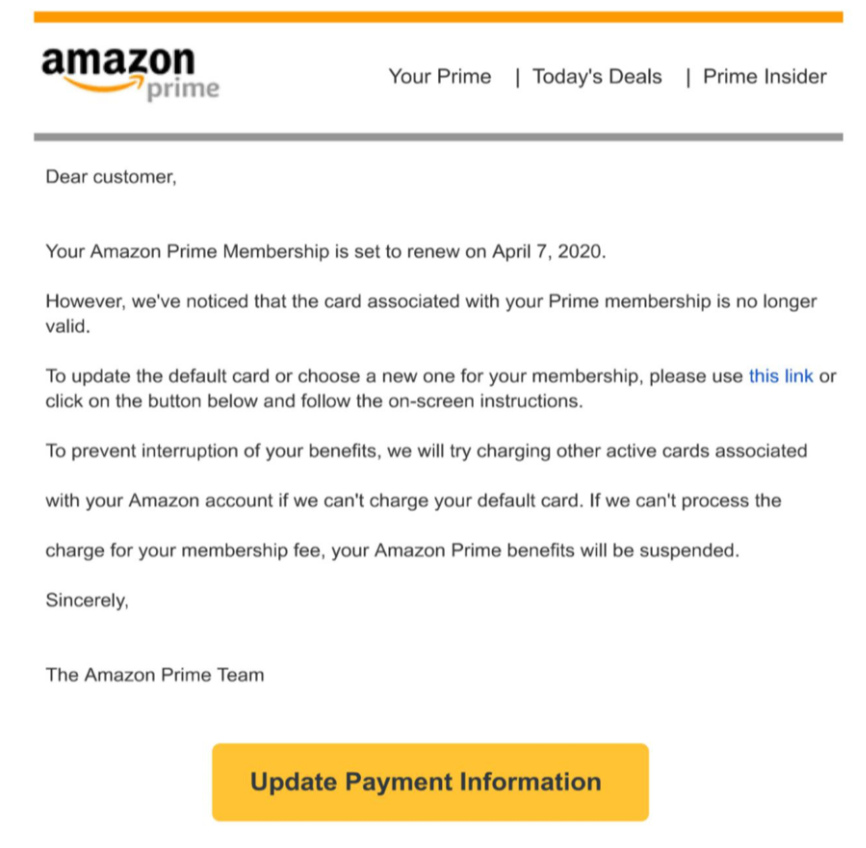
At the time of analyzing the data for the purposes of this article, all websites in this specific PDF phishing campaign have been deleted. It is worth noting that most of these e-commerce themed files used https: //t.umblr [.] Com / for redirection purposes.
Conclusions
We’ve covered the most common PDF phishing campaigns of 2020 along with their distribution and general functioning. Data from recent years shows that the amount of phishing attacks continues to increase and social engineering is the main vector for attackers to take advantage of users.
Previous research has shown that large-scale phishing can have a click-through rate of up to 8% . Therefore, it is important to double-check and double-check files that you receive unexpectedly, even if they come from an organization you know and trust.
For example, why was your account blocked out of thin air, or why did someone share a file with you when you least expected it?
It is with a critical eye and thinking before acting that you are best protected against phishing campaigns of any kind. We have seen several times how damaging phishing attacks can be that hit , so we recommend that you evaluate our ethical phishing service for your company’s employees.
Through ethical phishing campaigns we will be able to test employees and retrieve important data that will then be used to design and carry out specific training tailored to the people involved.
To find out more, contact us, we will be happy to answer any questions.
Useful links:

Estimated reading time: 8 minutes
Successful phishing attacks are increasing rapidly and so is the variety of forms they come in. Today I want to bring a couple of examples of phishing reported in the last period on the Italian territory by the CSIRT ( Computer Security Incident Response Team ).
Millions of users around the world are put at risk every day, statistically, one every 30 seconds. Cybercriminals are evolving and so are their techniques.
But it’s not just the traditional phishing scam that is catching on, but spear phishing and CEO fraud now also offer a much more damaging reach to the enterprise. For businesses, a successful attack could mean millions of dollars in damage.
Since it is known that users, even corporate users, tend to be lazy and do not manage their passwords effectively, even a phishing campaign aimed at individuals could provide useful credentials to later target corporate accounts. For this reason, one of the most effective defenses is the training of users, who, knowing the danger, can avoid it altogether.

Why does phishing work?
Before giving concrete examples of phishing that took place in Italy, it is interesting to understand why it is a technique that works so well. According to a white paper from Ostermann Research in 2017, phishing is the main concern of security teams.
There are 5 main reasons, identified by Ostermann Research, why phishing is still a real danger.
1. Lack of awareness
Undoubtedly, the predominant reason is the lack of “ security awareness “. More specifically, the lack of training on issues such as phishing and ransomware are the main reasons for the success of these attacks.
2. Need for more information
The use and notoriety of the Dark Web have lowered the commercial value of stolen data. The price of a credit card record dropped from $ 25 in 2011 to $ 6 in 2016 , which means that cybercriminals have had to adapt their attention to new ways to earn the amount of money they did in the past.
3. Lack of adequate protection
Companies are not doing enough to reduce the risks associated with phishing. There is a lack of proper backup processes, as well as an inability to identify weaker users who need further training.
In addition, there is a lack of strong control processes, such as double confirmation for every bank transfer request. Neglecting these protocols means putting yourself directly in the hands of some of the most common fraudulent techniques.
4. Ease of finding tools
The availability of phishing kits and the rise of ransomware-as-a-service (RaaS) gave would-be hackers an easy opportunity to enter the market and compete with sophisticated criminal organizations.
The most troubling part of this growing trend is that even people with little or no computer experience are reaping the benefits of these easy-to-obtain tools.
5. Attacks leverage people’s weak points
As we have seen with social engineering , leveraging some factors can lower people’s guards . Alternatively, you aim for a sense of urgency to ensure that the necessary checks are not carried out before taking action. At other times it is guilt or shame that are used as a weapon to request money directly, as in the case of ransomware .
Among the examples of phishing that we will see shortly, I believe that the main factors for which they succeed are ignorance of IT (security) and feelings of guilt or urgency transmitted in the messages used in attacks.
Examples of 2021 phishing on Italian territory
“Eni gas and electricity reimbursement”
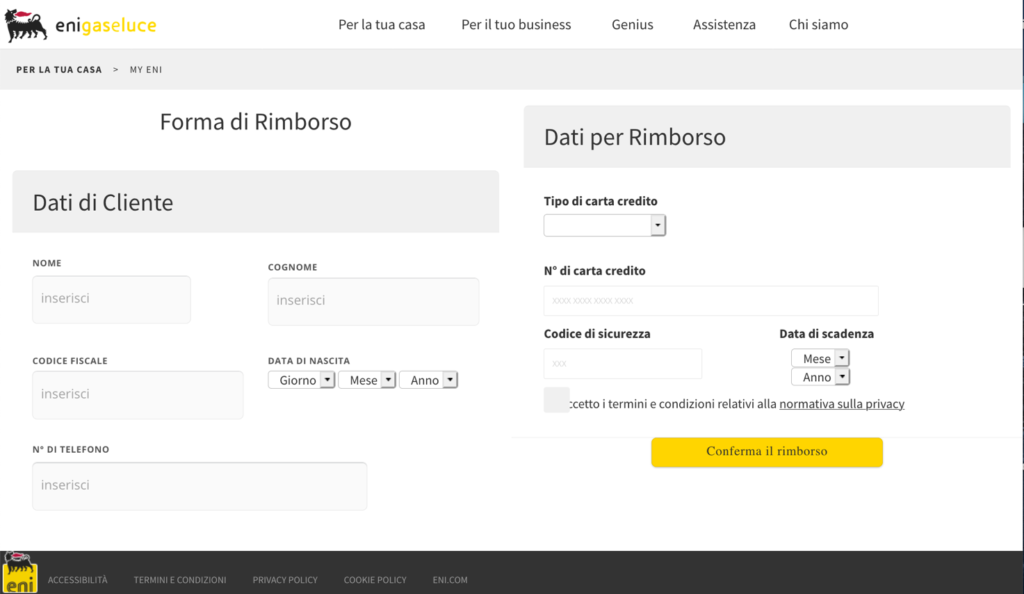
This campaign, reported in March 2021 , uses as a pretext a fake reimbursement from ENI Gas e Luce in order to steal personal data and banking information from the victims. The promise of a refund and seemingly legitimate web pages are key elements of the attack.
The following personal data are requested: name, surname, date of birth, social security number and telephone number. In addition, the following are also required: credit card type, number, expiration date and security code.
The victim reaches the phishing page by following a link to hxxps: //legendaryfirewitch.tumblr [.] com / eni , a page hosted on the Tumblr social platform. From here the user is redirected, using a Javascript script, to a page similar to the ENI website.
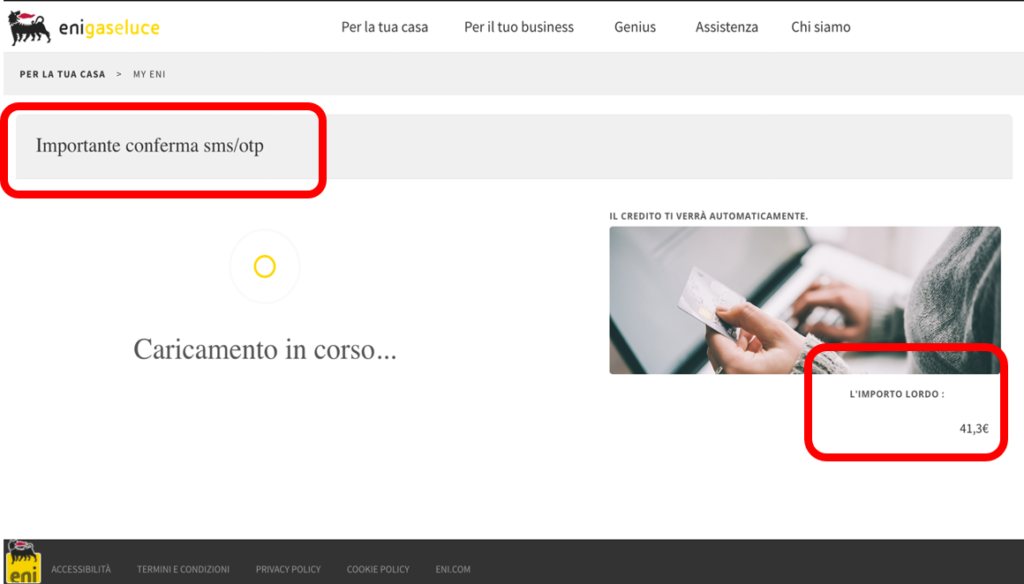
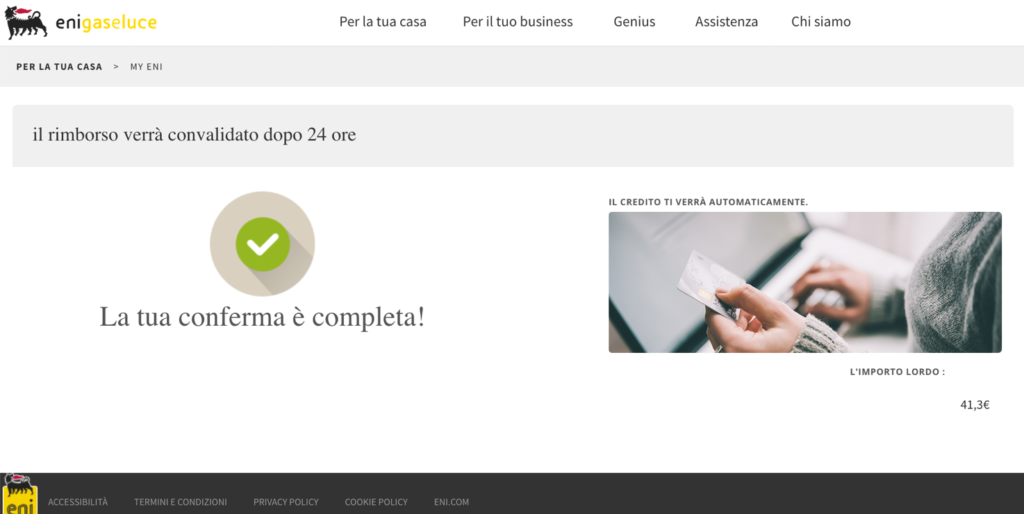
After entering the credentials in the form, two screens appear. A summary and a confirmation. Note that the SMS / OTP confirmation method is mentioned in the summary screen but is not required of the victim. Finally, you are directed to the real ENI website.
To defend yourself, always pay attention to the URLs of the pages you visit. These often contain elements of obvious wrongdoing. For example the ru extension of the pages.
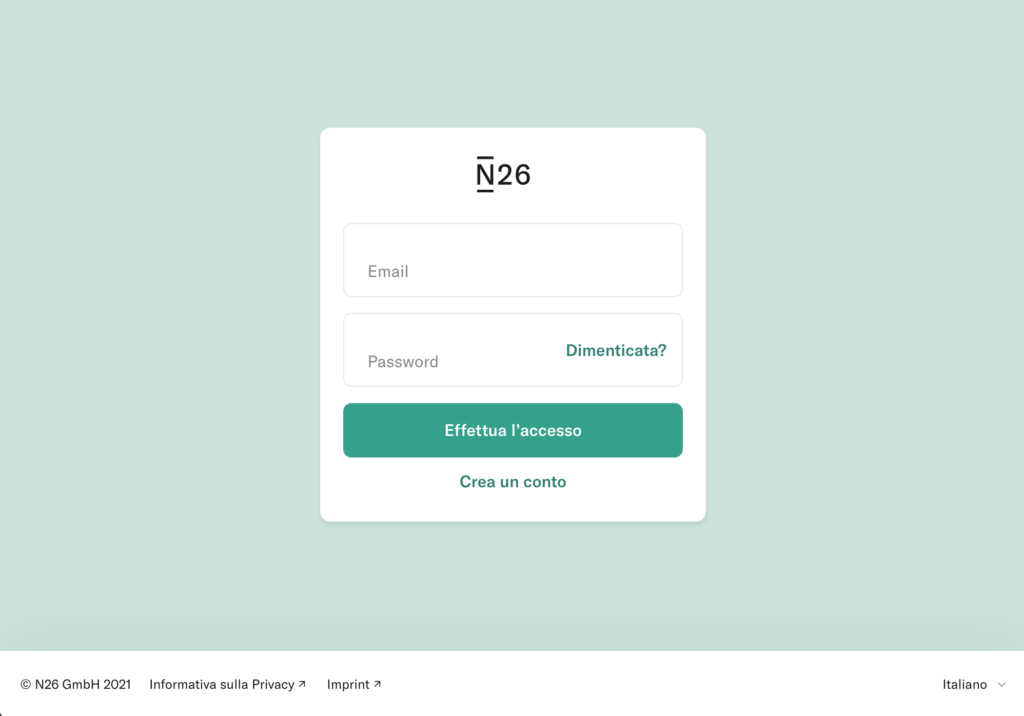
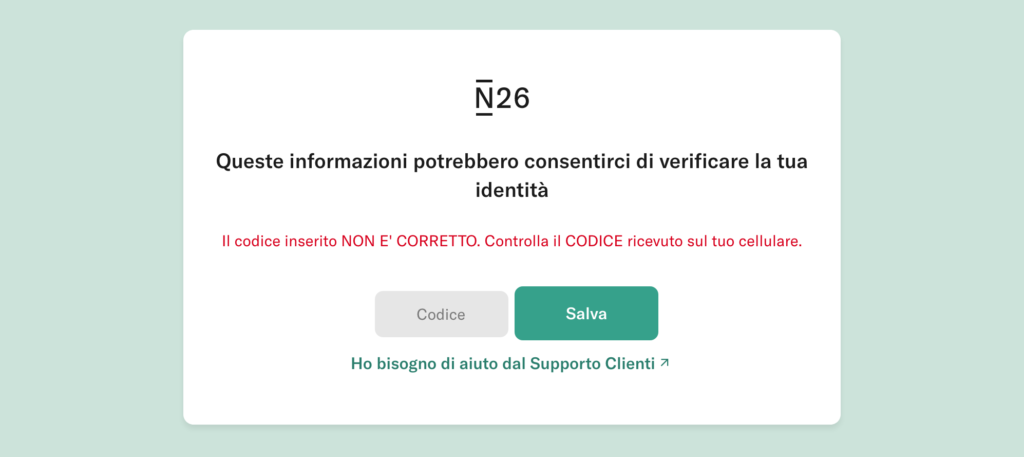
Bank Account Phishing Example (N26)
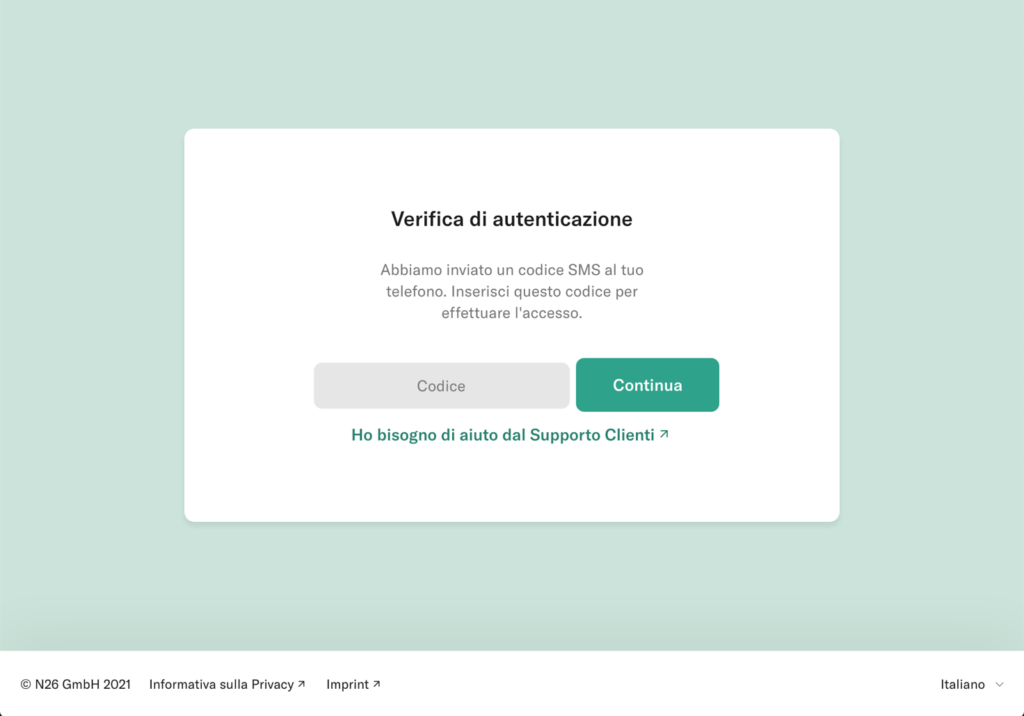
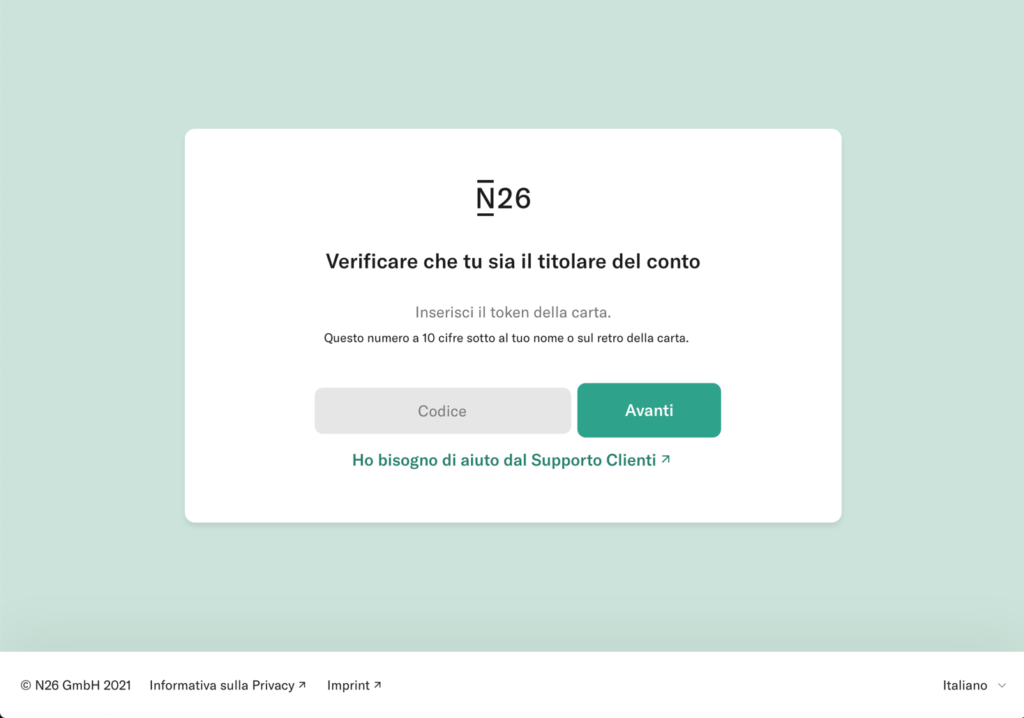
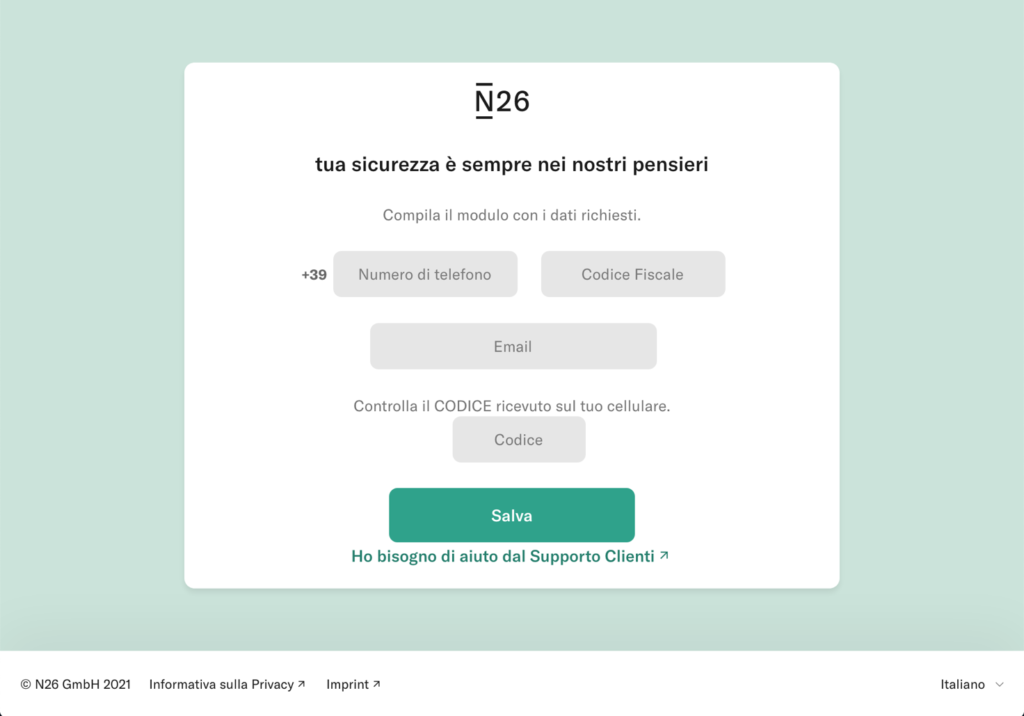
At the end of March 2021, a campaign affecting the customers of the N26 online bank was reported. Through SMS and email, users are asked for personal data, personal information (telephone number and social security number ) and the OTP code and the unique access token of the credit card.
Through a landing page very similar to that of N26, you are asked to log in to the service. The user enters the login credentials, the card code and then personal information is also requested. The excuse is to check the user’s data.
After entering the data, the victim is informed that the entered OTP code is incorrect and a new one is requested. This happens 3 times, until a server error page is shown.
The data has now been entered and sent to the attacker, who can access the victim’s account thanks to the information collected.
Conclusions
The phishing examples listed in this article are just two of all those regularly reported on the CSIRT site. Scams are often completely avoidable, if only you knew the basics of detecting a fraudulent web page.
Always valid advice: before following a link received, go to email, it is better to visit the site from your browser, without using the URLs provided in the message. Email communications are often notifications that must also be reflected on the account page on the site.
Those who fall victim to a phishing attack are likely not able to recognize threats in general. This can become a risk for the whole company.
The best defense is to invest in your employees. This can be done through ethical phishing campaigns followed by targeted training consolidate the problems found. At SOD, we can help your company recognize weaknesses and then provide employees with the information they need to raise the bar.
Contact us to find out how we can specifically help your company to raise the defenses against phishing and make the infrastructure more secure.
Useful links:
Useful links:

Estimated reading time: 7 minutes
Ethical hacking means the application for good of hacking techniques. The term “hacker” was coined in the 1960s at the Massachusetts Institute of Technology (MIT) to describe experts who used their skills to re-develop mainframe systems, increasing their efficiency and allowing them to perform more tasks.
Nowadays, the term normally describes experienced programmers who gain unauthorized access to computer systems by exploiting weaknesses or using bugs, motivated by bad intentions. For example, a hacker could create algorithms to crack passwords, break into networks, or even interrupt network services.

With the rise in popularity of the Internet and e-commerce, negative hacking has become the most commonly known form. An image reinforced by its representation in various forms of news and entertainment. Typically, the main thrust of malicious / unethical hacking is the theft of valuable information or financial gain.
That said, not all hacking is bad . In fact, there is a second type of hacking: ethical hacking. It could be argued that this is the original type of hacking. In fact, the first hackers did not have any negative intent, rather, their purpose was to optimize and improve existing systems.
What is ethical hacking and why do we need it?
Ethical Hacking is the authorized practice of bypassing the security of a system to identify potential data breaches and threats on a network . The company that owns the system or network allows ethical engineers / hackers to perform such activities in order to test the system’s defenses . So, unlike malicious hacking, ethical hacking is planned, approved, and most importantly, legal .
Ethical hackers are meant to investigate your system or network for weaknesses that malicious hackers could exploit or destroy. They collect and analyze information to understand how to strengthen system / network / application security. By doing so, they can improve security so that it can better resist attacks or mitigate them .
Ethical hackers are hired by organizations to prevent data breaches . In essence, this is the reasoning: to understand how a thief could enter your house, the best thing is to pretend to be thieves and use their techniques.
Note that the reasoning implies that those who perform ethical hacking do not know the state of the system they are about to breach , so they will not be influenced in any way in carrying out certain activities or breaching only certain parts of the system . For the company, this means that the best ethical hacker they can find is someone outside the security team.
The activity of ethical hackers
Ethical hacking controls key vulnerabilities that include many aspects of the computer system such as: changes in security settings, exposure of sensitive data, breach of authentication protocols, etc.
Of course, every business infrastructure is made up of a potentially unique combination of tools, hardware and software. For this, the ethical hacker must field a lot of knowledge, customized tools and specific procedures that are almost never the same from project to project. This is good, because, just like malicious hackers, the ethical hacker is also pushed to stay up to date on industry news, test new techniques and study new ways to mitigate the risk.
Types of hackers
The practice of ethical hacking is called “white hat” hacking and those who perform it are called white hat hackers . In contrast to ethical hacking, “Black Hat” describes practices that involve security breaches. black hat hackers use illegal techniques to compromise systems or breach data.
Unlike white hat hackers, hackers “ Gray Hat ” do not ask for permission before entering the system , but their motives do not I’m malevolent. In fact, gray hats are also different from Black Hats in that they do not hack for personal or third party advantage. These hackers break into systems for fun, usually informing the owner of any threats they find . Gray hat and black hat hacking are both illegal because they both constitute an unauthorized breach of the system, even if the intentions are profoundly different.
The intentions
The best way to distinguish between white hats and black hats is to take a look at their motives . black hats are motivated by personal gain, profit or harassment; while white hats (ethical hackers) seek and remediate vulnerabilities, so as to prevent other hackers from taking advantage of them.
Let’s look at other differences between the two types of hackers together.
Techniques used
Ethical hacking duplicates the techniques and methods used by malicious hackers in order to uncover the flaws in the system. By replicating all the steps of cyber criminals, you can find out how an attack on the system happened or could happen . If they find a weakness in the system or network, they report it immediately and fix the flaw. These types of services are usually called vulnerability assessment and penetration testing , and are also offered by SOD.
Legality
Even if the ethical hacker follows the same techniques and methods as the black hat hacker , only one practice is legally acceptable . Hackers usually break the law by breaking into systems without consent, while ethical hackers get permission from system owners who hire them to test infrastructure.
Property
Ethical Hackers are employed by organizations to break into their systems and detect security problems. The black hat hackers do not own the system or work for someone who owns it.

Benefits of ethical hacking
Learning ethical hacking involves studying the mentality and techniques of black hat hackers to learn how to identify and correct vulnerabilities within networks. The study ethical hacking can be applied by security professionals in all industries and in a multitude of sectors. This sphere includes the network defender , the risk management and the quality assurance tester .
However, the most obvious benefit of learning ethical hacking is its potential to inform and improve and defend corporate networks. The primary security threat to any organization is a hacker . Learning, understanding and implementing how these criminals operate can help security officers prioritize potential risks and learn how to best remedy them.
It should be noted that hacking must not be understood as relating only to IT infrastructures but to the entire technological apparatus of a company . Social engineering , for example, leverages the human factor to gain access to places, physical or virtual, where valuable data is stored. Furthermore, through phishing campaigns , it is possible to trick users of a system into providing their passwords and “giving” access to malicious people.
SOD services for the security of your company
Every company that handles sensitive customer data must ensure that the procedures and systems used are sufficiently secure. As mentioned before, having internal personnel carry out tests and vulnerability tests could be a weapon double-edged. Even if you have a security expert, you have to consider that having to violate systems that he may have set up himself, increases the risk of a false positive.
For this reason, companies like SOD provide services geared towards the evaluation and testing of corporate security measures.
From the classic Vulnerability Assessment and Penetration Test , designed to test network hardware and software , you can switch to services that physically test corporate security or even the management procedures of sensitive data.
With the physical security addons techniques are put in place to gain access to offices , try to reach network control units or servers, but also attempts to tamper with or install unauthorized hardware.
As regards the human factor, a ethical phishing service is also available, through which a phishing campaign is launched towards the company and employee reactions are tested . This identifies the weak points that will then be used to organize an ad hoc training path.
As you can see, SOD provides companies with complete security services. Please feel free to contact us to request further information or ask us any questions you may have.
Useful links:

Estimated reading time: 6 minutes
Cyber Security is the practice of defending computers, servers, mobile devices, electronic systems, networks and data from malicious attacks. It is also known as Information Technology Security and Electronic Information Security . The term applies in a wide variety of contexts, from business to mobile computing and can be divided into a few common categories.
We can divide cyber security into several areas of interest which I list briefly below. In almost every situation listed, SOD has a dedicated service.
Cyber Security areas of interest
network security is the practice of protecting a computer network from intruders, whether it is targeted attacks or generic malware .
application security focuses on keeping software and devices free from threats. A hacked application may be providing access to data that it was designed to protect. Robust security begins in the design phase , well before a program or device is deployed. This is why analyzing the code of an app is essential before it is released.
operational security includes processes and decisions in the management and protection of resources and data. The permissions that users have when accessing a network and the procedures that determine how and where data can be stored or shared all fall within this scope.
Disaster recovery and business continuity define how an organization is able to respond to a cyber security incident or any other event that causes data loss . Disaster recovery policies dictate how the organization restores its operations and information to return to the same operational capacity as before the event. business continuity is the plan the organization resorts to as it tries to operate without certain resources.

The human part of cyber security
End User Education addresses the most unpredictable factor in cybersecurity: people . Anyone can accidentally introduce a virus into an otherwise secure system by not following security best practices. For example, teaching users to delete suspicious email attachments and not insert unidentified USB drives is vital to the security of any organization .
In this area, particular importance should be given to scams, phishing and in general social engineering, which relies on the element usually more weak computer system: the operator.
The scope of cyber threats
The global cyber threat continues to evolve at a rapid pace, with a increasing number of data breaches every year . A report from RiskBased Security revealed that 7.9 billion documents were exposed to data breaches in the first nine months of 2019. This figure is more than double (112%) of the number of documents exposed in the same period the previous year.
I medical services , retailers and government agencies have experienced the most breaches , with malicious criminals responsible for most accidents. Some of these industries are more attractive to cybercriminals because they collect financial and medical data, but all companies using networks can be targeted for their customers’ data, corporate espionage, or to attack customers .
What governments do
With the scale of the cyber threat set to continue to grow, the International Data Corporation predicts global spending on cyber security solutions will reach a record $ 133.7 billion by 2022 . Governments around the world have responded to the growing cyber threat with guidance to help organizations implement effective cybersecurity practices.
In the United States, the National Institute of Standards and Technology (NIST) has created a cyber security framework , to combat the proliferation of malware code and aid early detection. The framework recommends continuous, real-time monitoring of all electronic assets .
The importance of system monitoring is resumed in the “ 10 steps to cybersecurity “, a guide provided by the UK government’s National Cyber Security Center . In Australia, the Australian Cyber Security Center (ACSC) regularly publishes guidance on how organizations can counter the latest cybersecurity threats.
In Italy we have the national framework for cyber security which provides tutorials, guides and European standards on cyber security .
MSSP and cyber security services
A Managed Security Service Provider (MSSP) provides monitoring and management in outsourcing for security devices and systems. In practice it takes care of all cyber security measures for the company requesting the services.
SOD is an MSSP and the services offered include protection and monitoring of various sectors of the corporate IT department.
Our verification services include vulnerability and penetration testing , as well as the analysis of safety procedures . With the SOC as a Service service we provide the potential of a Security Operation Center , relieving the company of installation and management costs. The SOC adopts latest generation technologies such as SIEM Next Gen and UEBA , which introduce analysis by an AI for motoring logs and users .
SOD uses security operations centers to provide 24/7 services designed to reduce the number of operational personnel that a company must manage, while still guaranteeing levels of cyber security excellent.
But defense fronts don’t stop at software and machines, must also include the most unpredictable element: the end user . That’s why our offer for companies also includes people-oriented services, as we will see shortly.

End user protection
End user protection is a crucial aspect of cyber security . After all, it is often the end user who accidentally loads a malware or other form of malware on their device .
As suggested earlier, the security protocols set up by SOD analyze software in real time. Through behavioral analysis systems we can monitor both the behavior of a software and the user . In the case of an attack based on lateral movement , for example, abnormal accesses and requests by a user can be indicators of an attack in progress.
But we don’t stop there, we can test the company against techniques of social engineering , phishing and physical tampering. Thanks to the ethical hacking services and consequent report, we are able to identify the company’s weak points and suggest effective strategies to mitigate the risks. In the case of phishing, we also organize ad hoc training based on the weaknesses highlighted in the report.
Through the physical security service, in addition to the IT vulnerability testing services, we put ourselves in the play the bad guys and try to carry out physical attacks . For example, we try to enter corporate buildings that should be protected, we try to reach network infrastructures and install potentially harmful hardware, etc.
Thanks to a team of ethical hackers and trained and trained operators, we test every aspect of cyber security before a risk becomes a problem .
If you want more information about our services or have any questions, don’t hesitate to contact us.
Useful links:

Estimated reading time: 9 minutes
Spam seems to reach every single email account we use , no matter how careful we are or what the address provider is. How do spammers get all of our email addresses? Can we do something to hide our email address from common spammer techniques?
Unfortunately, there’s not much you can do to stop spammers from bombarding you with emails. There are some tips that will help protect you, but spammers will probably find your email address anyway .
The problem is not so much the unwanted advertisement message, but rather what it means that you received a message. How did you react? Did you delete it? Did you click on any links? Have you flagged it as spam? Any action could bring useful information to attackers without you noticing.
Let’s face it more clearly and start with a question: where do spammers find our e-mails?
Spammer techniques for retrieving e-mail addresses
Nobody gives their email to a website and expects it to end up in the hands of a scammer. Yet it’s not uncommon for someone to find their inbox full of unsolicited spam emails.
Stolen databases
The simplest of the techniques spammers use to collect large lists of active email addresses is through stolen account databases. These password thefts happen with frightening regularity. Companies like Adobe, LinkedIn, eHarmony, Gawker, Last.fm, Yahoo !, Snapchat and Sony have all been compromised in recent years .
Leaked databases are normally considered a security threat because they often display account names and passwords. However, generally show email addresses as well. Spammers can download these leaked databases and add the millions of email addresses to their lists . Spammers know that most of these email addresses should be active , so these databases are excellent for them.
This is probably how most spammers are finding email addresses to send spam. There really isn’t much you can do to protect yourself from a spammer who gets your address this way.
A site like Have I been pwned? can tell you if the information of your account may have been spread .
You can protect yourself from password theft by using different ones, unfortunately, you must always use the same email address everywhere , it would be unthinkable to have an address for each service used.
Link in mail messages
If you receive spam emails, you should avoid clicking on the links in the email . If you find an “Unsubscribe” link in an email from a legitimate company, it’s probably safe to click it. A real company doesn’t want to spam and potentially run into anti-spam laws, so they will simply remove you from their list.
However, if you see an “Unsubscribe” link (or, even worse, a “Buy Now!” link) in an email that looks very unprofessional and scam, the spammer will not necessarily remove you from his lists .
This is where things get more complex. They will notice your click and their systems will identify your email address as active . They know you’re there, and you may see larger amounts of spam after clicking the link.
The same goes for uploading images in spam emails. Do not click the “Upload images” button, or spammers will know that you have opened the email . Even if you don’t see an image in the message, there may be a small tracking pixel that allows the spammer to identify you if you upload the asset.
This is why most email clients don’t automatically upload images.

E-mail scraping, search for unencrypted e-mails on the net
Another spammer technique to retrieve addresses from the network is to scrape them ( scraping ) from the unencrypted data on the network. There are software out there that read files on the net and find those that contain e-mails and save them. A bit like Google’s crawlers do when they crawl a site, but with malicious intent.
You may have seen a comment where someone leaves their address to be contacted. The bot that scans the network will save similar addresses.
The spammer adds this address to his spam lists et voilà , spam is served . This is why eBay provides a temporary email address where you can be reached rather than including your real email address. This technique is probably less common now that spammers have huge leaked account databases to work with.
Spammers can also try to acquire valid email addresses by browsing other places that are publicly available, such as whois records for a domain . These records show an email address associated with the person or organization that registered the domain name.

Purchase of email addresses
Another spammer technique, definitely for lazy hackers, is to buy addresses from databases that provide them.
Unscrupulous people sell email lists to spammers for a low price. These addresses were often distributed on CD in the past , and may still be, but the leaked account databases have probably eliminated some interest in this market.
Spammers can also simply exchange their mailing lists with each other, making sure other bad guys get their hands on your address once it happens the first time.
Please be aware that this technique is not entirely illegal. When we subscribe to a service, we often have the possibility to provide our e-mail address to third parties for advertising purposes. Some users accept without reflection and without verifying whether it is an obligation to subscribe to the service or not. .
I personally happened to be contacted by a person who, with no intent to spam, but to make up the number, had bought my address from a contact resale agency, divided by areas of interest. If he had been a spammer, he could have used a similar service.
How to protect your address
Spammers can also obtain email addresses in other ways but the methods listed above are some of the most common.
There isn’t much you can do to prevent your email address from being leaked and receiving spam.
- – you can avoid putting your e-mail address on the web in plain text form
- – never click on a link
- – don’t upload a image in a suspicious email.
However, your address will almost certainly end up in the hands of a spammer at some point.
Actually, you don’t have to worry so much about whether the address is in circulation, but about how the address is used, especially if it is active.
Spammer techniques of using addresses
Once a scammer obtains your email address, it is very likely that they will use it to take advantage in any way possible . The better he is, the greater the risks.
Many will send you spam emails, with the hope of collecting private information such as credit card numbers . They will try to trick you into believing that you have won something, or that they have a profitable item for sale. Hackers may also use your email to steal your identity and send messages to your contacts . Remember the techniques of Zombie Phishing ?
Other scammers will use your personal information to try to access your other accounts . Most people reuse the same passwords for different accounts, which means that hackers who have access to one account can easily infiltrate the others.
This is why using the same passwords around the web is highly discouraged and not secure at all.
Create botnets
One of the reasons why you should never actively interact with spam messages is that interactions send hackers an important piece of information: the address is active, someone uses it on their device.
An active address, once discovered, is a perfect target for more specific attacks than phishing , and since all addresses are at risk, even corporate ones, from phishing you can easily get to a double extortion ransomware .
In the latter case, the threat of a DDoS attack may already come from mentioned zombie phishing technique, and it could all have started with some spam message.
The computers that will basically send requests to the server to perform the DDoS attack could themselves be part of a botnet created as a result of techniques used by spammers .

Phenomenology of an attack
As a first spammer technique, company addresses are retrieved . This can be done through scraping or database buying on the dark web. Next, to check which addresses are active , a couple of spam campaigns are sent. Nothing harmful, fake newsletters with an obvious Unsubscribe message, or a tracking pixel.
Note: A tracking pixel is usually a very small transparent image that is uploaded from a remote server. Just check how many times it has been downloaded and by whom to understand which addresses are active and which are not .
As a result, the contact database will have shrunk to a list of active addresses , in which users have been inattentive enough to click on a link from a suspicious email.
Finally, to these selected addresses, is sent a real phishing message containing malware or a request to intervene on a seemingly legitimate web page . For example, the request to reset your credentials via the attached link.
The unsuspecting user, thinking he is doing a safe thing, follows the link, enters the credentials and gives them to the spammer . At this point the attacker has gained access to an account. From that moment on, the risks are much more and much more damaging.

How to defend against spammer techniques
Let’s take a few steps back. The whole chain of events that led the hacker to gain access to an important account went through spam and phishing messages.
Ethical Phishing
In some of the passages, the attack could have been avoided . The ability to recognize a suspicious message and then ignore it is the first weapon available to a user. SOD can help your business with this .
Through a ethical phishing service, we first test the resilience of users . Once any weak points have been identified, a training course ad hoc is constructed to provide adequate proactive defense tools to all employees.
SOC as a Service
Not always being aware users is enough , and a careless mistake could cost a company a lot of sensitive data. For this reason, we can also implement a service SOCaaS for the mitigation of risk and damage following an attack.
In this scenario, a system consisting of next generation SIEM and protocols UEBA implemented by an artificial intelligence, they monitor the network in search of any anomaly . Any suspicious behavior is identified and analyzed by technicians to see if it can actually become a threat or not.
If you would like more information on how SOD can help you raise your company’s cybersecurity level, don’t hesitate to contact us.
Useful links:

Estimated reading time: 6 minutes
Out of nowhere, someone replies to an email conversation dated months ago. This is a real conversation that actually happened. Maybe it’s about a meeting, a job opportunity. This email seems very relevant, but beware, it could be zombie phishing .
Indeed, something is wrong, the topic discussed has been over for months and now there is a strange error message in the body of the email. This is a sneaky tactic: revive a long dead email conversation.

Not the usual phishing
The Cofense ™ Phishing Defense Center ™ (PDC) spotted a large Zombie Phishing campaign in 2018. The scam , like almost any phishing attack, is carried out through compromised email accounts.
Scammers take over an email account and respond to long-closed conversations with a phishing link or malicious attachment (e.g. malware or a keylogger ) . Since the email subject is usually relevant to the victim, a curiosity-driven click is very likely to occur . In fact, let’s not forget that the original conversation was already present in the messages received, it is easy to think that it is a follow up or similar.
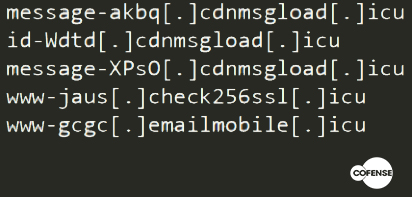
These Zombie Phishing attacks appear to use automatically generated infection URLs to evade detection. No two links are alike, and they are hidden behind “error” messages without too many frills in the body of the message. This scenario provides a pattern of apparent legitimacy for the users who are victims.
The zombies in computer science
In the computer industry, a zombie is a compromised computer connected to the network. The compromised state could be due to a hacker, virus, malware, or trojan horse .
The infected machine performs malicious tasks under a remote direction. Zombie computer botnets are often used to spread email spam and launch denial-of-service (DoS) attacks.
Types of attack
Here are some observed patterns of Zombie Phishing carrying malicious links . A distinguishing factor was the use of two distinct graphic templates containing button or link error messages.
The message reads something like “Incomplete message” or “Inability to show the whole message”. The link or button invites you to click to see the original message. Obviously the click only involves the installation of a malware or other similar events . Note that no two identical links have been identified, a sign that probably a bot was generating the addresses.
Another common factor is the use of domains with the .icu TLD. This is probably a factor that varies considerably over time. Here are some of the domains found in the first analysis of 2018:
These zombie phish attacks have been observed to use official organizational logos to add legitimacy to the fake login pages. A common practice in phishing techniques that we have already seen in other articles.
Landing pages are designed to look like a legitimate online portal, including a company logo and even a favicon. In these cases the ultimate goal is the theft of the victim’s credentials .
Furthermore, any victim who visits the malicious website is “tagged” using the host’s IP address as an identifier and, after entering the credentials, is directed to the same spam website seen by other victims. This is often done via obfuscated links using URL shorteners (such as hxxps://href[.]Li/).
If the same host tries to visit the phishing link again, the fake login page is skipped and you are forwarded directly to the spam page. This markup and URL shortener obfuscation helps attackers keep a low profile and continue their campaign unabated.
Conversation Hijacking

The conversation hijacking tactic is by no means new and is now living a new life with zombie phishing . Scammers have hijacked compromised email accounts to distribute malware and phishing emails as replies to conversations that have been concluded for years now.
This technique is still popular because it makes victims much more likely to click on links and download or open files. The threshold of attention against classic phishing attacks is lowered when messages are brought into conversations already in their inbox .
A couple of years old example of this was the botnet Geodo . Basically it is insertion into existing email threads ( conversation hijacking ) to deliver malicious documents. These, in turn, download a sample of Geodo or other malware such as Ursnif , which according to Key4Biz was the most widespread in Italy in June 2020.
However, the effectiveness of this tactic can greatly depend on the content of the conversations . A reply to an automated advertising email is less likely to cause an infection than a reply to a help-desk support thread.
There have been several Geodo zombie phishing campaigns consisting of replies to automated advertising emails. This is an indication that, in some cases, campaigns consist of indiscriminate replies to all emails in a mailbox. Since the volume of these conversation hijacking is still relatively low, the small reach of these emails is probably limited by the number of ongoing conversations .
Certain account types are therefore more likely to attract the direct attention of threat actors and induce them to invest additional effort and time in developing unique phishing campaigns for those accounts.
Defense from zombie-phishing
Here are some quick tips to avoid losing your credentials in a Zombie Phishing attack:
- Beware of email subjects that may seem relevant but come from old conversations
- Beware of any error message in the body of the message
- Don’t trust attached documents just because they’re replying to a conversation
- Hover your mouse over buttons or links in suspicious messages to check for suspicious domains
It has been observed that these campaigns have gotten smarter . To combat this and other forms of phishing, employee training is key.
A properly trained workforce is what it takes to defend your organization against Zombie Phishing attacks.
SOD offers a full service in this regard . We begin by attacking the company in a controlled manner, testing any weaknesses in employee safety or behavior. Subsequently, specific training is designed to remedy the gaps and fully train the staff.
To keep defenses high, our SOCaaS includes the analysis of user behavior, logs of connected machines and the network in a to immediately identify phishing attempts.
Useful links:

Estimated reading time: 10 minutes
Social engineering is the term used for a wide range of malicious activities performed through human interactions. It uses psychological manipulation to trick users into making security mistakes or provide sensitive information. Then, with that information, the hacker is able to successfully carry out targeted attacks, such as data theft, a ransomware or a ‘ interruption of services.
Social engineering attacks usually occur in stages . The perpetrator first investigates the intended victim to gather the necessary background information , such as potential entry points and weak security protocols, required to proceed with the attack. Then, the attacker moves to gain the victim’s trust and provide incentives for subsequent actions that violate security practices, such as disclosing sensitive information or granting access to critical resources.
What makes social engineering particularly dangerous is that it relies on human error rather than vulnerabilities in software and operating systems . Mistakes made by legitimate users are much less predictable, making them more difficult to identify and thwart than a malware-based intrusion.

Note that the target of a social engineer is not necessarily a network or software . Being able to enter a building evading security, and then installing a device or stealing documents, are actions that still fall under this type of attack.
The techniques of social engineering
Social engineering attacks come in many different forms and can be carried out wherever human interaction is involved . The following are five most common methods of digital social engineering attacks.
Baiting (from “bait”)
As the name suggests, baiting attacks use a false promise (a decoy , indeed) to whet the victim’s greed or curiosity. They lure users into a trap that steals their personal information or installs malware on their systems.
The most infamous form of baiting uses physical media to disperse malware . For example, attackers leave the bait (typically infected keys) in conspicuous areas where potential victims are certain to see them (e.g. bathrooms, elevators, the parking lot of a targeted company). The decoy has a legitimate look, like a label indicating the content, like the company’s payroll. The clue that reveals what it should contain may change, of course, but has the potential to be potentially very interesting .
Victims pick up the bait out of curiosity and insert it into a work or home computer, resulting in automatic installation of malware on the system.
Lure scams don’t necessarily have to be done in the physical world. Forms of online baiting consist of enticing advertisements leading to malicious sites or encouraging users to download a malware-infected application. Here it leads to the phishing techniques, which we will see shortly.
Defense notes : to defend against these social engineering attacks, as well as paying close attention to what is connected to your computer, it does not hurt to have an efficient antivirus and anti-malware system. For the company, a new generation SIEM system and UEBA help in detect suspicious user behavior and greatly reduce the risk of malware infection.

Scareware (from “to scare”)
Scareware consists of bombarding victims with false alarms and fake threats . Users are tricked into thinking their system is infected with malware, prompting them to install software that has no real benefit (other than the perpetrator) or is malware itself. Scareware is also called deception software ( deception software ), rogue scanner software and fraudware .
A common example of scareware is the legitimate-looking popup banner that appears in your browser as you browse the web , displaying text such as “ Your computer may be infected with spyware programs harmful “. In other cases, the popup offers to install the tool (often infected with malware) for you, or directs you to a malicious site where your computer is infected.
Scareware is also distributed via spam email which distributes bogus warnings, or offers users to buy useless / harmful services. Social engineering is often very imaginative and manages to find ever new ways to deceive. Always be alert.
Defense notes : In case you suspect that the received message is really legitimate, it is best to seek a solution actively , i.e. without using the links suggested by the message same. For example, we received a message from a service announcing that our account has been compromised. If in doubt, you can contact the support of the service directly from their site to ask for clarification. Avoid using the links suggested by the suspicious message at all costs .

Pretexting (from “to pretend”)
In this social engineering attack, an attacker gains information through a series of cleverly constructed lies . The scam is often initiated by an perpetrator who pretends to need sensitive information from a victim in order to perform a critical task.
The attacker usually begins by establishing trust with his victim by impersonating colleagues, police, bank and tax officials, or others who have a right to know authority . The hacker asks questions that are apparently necessary to confirm the victim’s identity, through which he collects important personal data.

Many types of information are collected using this technique, such as identity card numbers, personal addresses and telephone numbers, telephone records, staff vacation dates, bank records, and even security information relating to a physical facility.
Any information, however harmless it may seem, could later be used for a second attack. Even the name of a security guard hired by the company could already be enough to build trust and ask for a tear to the rule when asking for the access code to automatic doors.
Phishing (from “to fish”)
As one of the most popular types of social engineering attacks, phishing scams are email and text message campaigns that aim to create a sense of urgency , curiosity or fear in the victims . Then it prompts them to reveal sensitive information, click links to malicious websites, or open attachments that contain malware.
An example is an email sent to users of an online service notifying them of a policy violation that requires immediate action on their part, such as a mandatory password change. Includes a link to a website, nearly identical in appearance to its legitimate version, which prompts the user to enter their current credentials and new password . After submitting the form, the information is sent to the attacker.
Since identical, or nearly identical, messages are sent to all users in phishing campaigns, detecting and blocking them is much easier for mail servers that have access to threat-sharing platforms.
Defense note : While it is true that in some cases we have become accustomed to not giving weight to these kinds of messages, it is also true that social engineers have become increasingly clever. There is no need to let your guard down. Instead, it is very useful to always be wary of messages that require credentials.
These attacks leverage the fact that it’s easy to fool some users, whether out of distraction or naivety. The best defense is employee training through a ethical phishing service and subsequent targeted training.

Spear phishing (from “spear, and “to fish”)
This is a more targeted version of phishing in which an attacker chooses specific individuals or businesses . They then tailor their messages based on their victims’ characteristics, job positions, and contacts to make their attack less obvious. Spear phishing requires a lot more effort from the author and can take weeks and months to complete. They are much harder to detect and have better success rates when done skillfully.
A spear phishing scenario could involve an attacker who, impersonating an organization’s IT consultant, sends an email to one or more employees. It is worded and signed exactly as the consultant normally does, thus fooling recipients into thinking it is an authentic message. The message prompts recipients to change their password and provides them with a link that redirects them to a malicious page where the attacker now captures their credentials.

How to defend against social engineering attacks
Social engineers manipulate human feelings, such as curiosity or fear, to carry out patterns and lure victims into their traps. Therefore, it is essential to be cautious whenever you feel alarmed by an email, attracted to an offer displayed on a website, or when you come across digital media wandering around. Being alert can help protect you from most social engineering attacks that happen online.
Additionally, the following tips can help you improve your vigilance in relation to social engineering attacks.
- Do not open emails and attachments from suspicious sources . If you don’t know the sender in question, you don’t need to reply to an email. Even if you know them and are suspicious of their message, cross-check and confirm the news from other sources , such as over the phone or directly from a service provider’s website. Even an email that appears to come from a trusted source may have been initiated by an attacker.
- Use multi-factor authentication . One of the most valuable pieces of information attackers look for is your user credentials . Using 2-factor authentication helps ensure the protection of your account in case of system compromise. There are free applications for all types of mobile devices that allow you to implement this type of authentication.
- Be wary of attractive offers . If an offer seems too tempting , think twice before accepting it as real. Use Google to check the topic and quickly determine if you are dealing with a legitimate offer or a trap.
- Update your antivirus / antimalware software . Make sure automatic updates are turned on. Check periodically that updates have been applied and scan your system for possible infections.
If your company has an IT department, these recommendations should be standard security measures.

Security services for companies
When you think about the data that your company holds and manages, you are never too cautious in defense. Social engineering relies on the fact that an employee hacks more easily than a computer , which is often true.
In addition to the cyber protection measures listed above, it is good that all employees are aware of the risks and potential threats.
SOD offers a series of services that go in this direction. The first and perhaps most important is ethical phishing in which we try to attack the company with phishing techniques . We find out what the weak points are and organize internal training to provide the right tools for staff.
We also have the classic Vulnerability Assessment and Penetration Test for testing cybersecurity systems. Addons are applicable to this service to cover a greater number of areas. There is a specific addon for app analysis and code review , but also one where we try to hack the company with physical attacks . We will test the physical security of the company, the ability to enter buildings, access to network controllers and more.
Finally, to keep networks under control, the SOCaaS service allows you to monitor the entire network, identify suspicious actions (with behavior analysis via artificial intelligence), unauthorized installations, breach attempts and much more.
Data security in the company is really important, contact us to find out how we can help you!
Useful links:

Estimated reading time: 7 minutes
Phishing is a type of social engineering attack often used to steal user data, including login credentials and credit card numbers . Occurs when an attacker, disguised as a trusted entity , tricks a victim into opening an email, instant message, or text message.
The recipient is then tricked into clicking on a malicious link, which can lead to malware installation , system freezing as part of an attack ransomware or the disclosure of sensitive information.
An attack can have devastating results . For individuals, this includes unauthorized purchases, fund theft or identity theft.

What is Phishing for Business?
Even more damaging, phishing is also used to gain an entry point into corporate or government networks as part of a larger attack , such as a persistent advanced threat event (APT – Advanced Persistent Threat). In the latter scenario, employees are compromised in order to bypass security perimeters , distribute malware within a closed environment, or gain privileged access to protected data.
An organization that succumbs to such an attack typically suffers severe financial losses, as well as a decline in market share, reputation and consumer confidence. Depending on the scope, a phishing attempt could escalate into a security incident that a company will have difficulty recovering from .
What a phishing attack looks like
Knowing what phishing is often isn’t enough to protect yourself . The best thing to do is work on resilience to attacks and understand how to spot them before falling victim to them.
As we mentioned earlier, the consequences can be enormous. But, if it seems simple to do when it comes to a single individual, what if there is an entire company to protect? SOD offers a service geared towards just that : train entire companies to recognize and mitigate the risk of phishing attacks.
Through a first controlled attack, we are able to understand which are the points to work on . Subsequently, training proposals for employees are organized. They are taught how to recognize threats before they become problematic. To find out more, visit the service page .
But let’s see what a generic attack looks like.
Attack example
1. A bogus email ostensibly from myuniversita.edu is being distributed en masse to as many faculty members as possible.
2. The email claims that the user’s password is about to expire . Instructions are given to go to the myuniversita.edu/rinnovo link to renew their password within 24 hours.
Various things can happen by clicking on the proposed link.
– The user is redirected to myuniversita.edurinnovo.com , a fake page that looks exactly like the real renewal page, where both the new password are requested than the existing one. The attacker, monitoring the page, hijacks the original password to – gain access to secure areas of the university network.
– The user is sent to the real password renewal page. However, while being redirected, a malicious script runs in the background to hijack the user’s session cookie. This results in a Cross Site Scripting attack, giving the author privileged access to the university network.

Logic of an attack
Email phishing is a big game . An attacker who sends thousands of fraudulent messages can obtain significant information and sums of money, even if only a small percentage of recipients fall into the scam .
Hackers go to great lengths to design messages for a phishing attack by mimicking real emails from a disguised organization. Using the same phrasing, the same typefaces, the same logos and the same signatures, the messages appear legitimate .
Also, another thing to watch out for is that attackers usually try to push users into action by creating a sense of urgency. For example, as shown above, an email could threaten account expiration and put the recipient in urgency . Applying this pressure leads the user to be less diligent and more prone to error.
Finally, the links within the messages resemble their legitimate counterparts, but typically have a misspelled domain name or extra subdomains. In the above example, the URL myuniverist.edu/rinnovo has been changed to myuniversita.edurinnovo.com . The similarities between the two addresses give the impression of a secure connection , making the recipient less aware that an attack is in progress.
What is spear phishing

Spear phishing targets a specific person or company , as opposed to casual users. It’s a more in-depth version of phishing that requires special knowledge of an organization, including its power structure.
An attack could take place like this:
– A hacker searches for employee names within an organization’s marketing department and gains access to the latest project invoices.
– Posing as the director of marketing , The attacker sends an email to a project manager in the department using a subject that says: Updated invoice for Q3 campaigns . The included text, style, and logo duplicate the organization’s standard email template.
– A link in the email redirects to a password-protected internal document, which is actually a forged version of a stolen invoice .
– The marketing director is required to login to view the document. The attacker steals his credentials , gaining full access to sensitive areas within the organization’s network.
By providing the attacker with valid login credentials, spear phishing is an effective way to carry out the first phase of a ransomware attack.
What is whale phishing
whale phishing , or whaling , is a form of spear phishing that targets very big fish: CEOs or other high-value targets . Many of these scams target members of a company’s board of directors, who are considered particularly vulnerable. Indeed, they have great authority within the company, but because they are not full-time employees, they often use personal email addresses for business-related correspondence , which does not have the protections offered by email business.
whale phishing , or whaling , is a form of spear phishing that targets very big fish: CEOs or other high-value targets . Many of these scams target members of a company’s board of directors, who are considered particularly vulnerable. Indeed, they have great authority within the company, but because they are not full-time employees, they often use personal email addresses for business-related correspondence , which does not have the protections offered by email business.
How to defend yourself
Protecting against a phishing attack requires action by both users and businesses.
For users, vigilance is the key . A forged message often contains subtle errors that expose its true nature. These can include misspellings or changes to domain names , as seen in the example of the preceding URL. Users should be wondering why they are receiving a certain email .

For businesses, a number of measures can be taken to mitigate both phishing and spear phishing attacks:
Two-factor authentication (2FA) is the most effective method of thwarting phishing attacks, as adds an extra layer of verification when accessing sensitive applications . 2FA is based on users having two things: something they know , like a password and username, and something they have with them , like their smartphone . Even when employees are compromised, 2FA prevents the use of their compromised credentials, as these alone are not enough to get in .
In addition to the use of 2FA, companies should apply strict password management policies . For example, employees should be required to change their passwords frequently and not be allowed to reuse a password for multiple applications .
Finally, educational campaigns can also help decrease the threat of phishing attacks by enforcing safe practices , such as not clicking on external links to emails. In this regard, I would like to mention the ethical phishing service of SOD , which has the very intent of testing the company and organizing targeted training to mitigate the risks .
It’s not enough to know what phishing is, you also need to know how to recognize it.
Useful links:

Estimated reading time: 8 minutes
Looking to up the ante and earn more money with the ransomware , i Cybercriminals are increasingly using a tactic known as double extortion ransomware . Not only do they encrypt data and demand a ransom from the victim to regain access. They also threaten to upload them online if their conditions are not met.
Let’s take a step back, ransomware is one of the most common types of malware. It targets a company every 14 seconds and it cost $ 11.5 billion in 2019 alone . Typically, hackers who carry out these attacks break into a system to steal data and delete it if the victim doesn’t pay a ransom.

Why do hackers prefer double-extortion ransomware?
The rise of double extortion ransomware proves that cybercriminals are constantly expanding their arsenal. Paolo Passeri, director of cyber intelligence at the software firm Netskope , says these attacks they have become popular because they are the easiest way for hackers to make money.
Passeri Says: “With double extortion ransomware attacks, even if a backup is available, attackers can put more pressure on the victim to pay the ransom . The increased pressure comes from the potentially serious consequences of a data leak, for example economic and reputational damage. Groups like REvil are even more creative: they don’t just leak data, they monetize it by auctioning it on the dark web and putting even more pressure on their victims. “
When conducting a double extortion ransomware attack, hackers start spending more time on the overall strategy . Sparrows warns that scammers are no longer taking an opportunistic approach. Instead, they are carefully selecting their target and method of attack to increase the ransom money they make . He explains: “ the threat actors select their victims, choosing organizations whose businesses could be affected by a data leak “.
The spear phishing is the primary means of distributing double extortion ransomware, but cybercriminals are also by exploiting vulnerabilities in on-premises devices such as VPN concentrators. “In the past few months, nearly all major VPN technologies have suffered severe vulnerabilities that have been exploited for similar attacks,” says Passeri.
“This is unfortunate given the current situation with forced telework where these remote access technologies play a crucial role in ensuring business continuity during Covid-19. These systems are directly exposed to the Internet, so threat actors can scan them and then exploit any vulnerabilities discovered “.
Risks of Doxing : diffusion of private data
Double extortion ransomware provides more opportunities for cybercriminals, allowing them to extort victims twice. They can ask for a first payment to decrypt the files and a second payment not to make them public.
This technique, also known as doxing , is been used by an increasing number of ransomware groups over the past year. The consequences of doxing are more severe for the victim, so they often come down to demands. This means more money in the pockets of cybercriminals to fund new strains of ransomware and support other criminal activities.
Improvements in malware and financial incentives for hackers have led to the growth of double extortion ransomware attacks. In the past, ransomware encrypted files and hackers stole data, but it was rare to do both.
We now have bots that can scan the web for unprotected data, steal it, encrypt it or delete it, and leave a ransom note for the owner, all in one automated attack. The hacker can then collect a ransom for the data and sell the data to other criminals, playing double-crosses with minimal effort .

An aggressive-tactic
There has been an influx of double extortion ransomware attacks in the past year. Hackers gained traction in late 2019 when high-profile groups like Maze began exploiting aggressively this tactic.
In these particularly aggressive cases, the hacker would extract a copy of the data before encrypting it . This way the attacker not only prevents the victim from accessing her data, but also keeps a copy of the data for himself.
To claim responsibility and put pressure on the victim during the negotiation process, the attacker often released small chunks of data online. If the deals are blocked or failed, the attacker publishes all the stolen data or sells it to third parties . This creates a significant violation against the victim.
What to do
To defend against these attacks, there are several steps companies should take . For example, keeping systems updated to ensure that known vulnerabilities are resolved. It is also imperative that organizations have a layered security approach that includes the use of data loss prevention tools . An example is the service offered by SOD Acronis Cyber Protect Cloud . The system can stop the extraction or encryption of the data which initiates these double extortion attacks.
But what can organizations do if they can’t successfully mitigate one of these attacks?
Organizations should try to include a last line of defense that isolates and stops illegitimate encryption immediately . This mitigates the risk when traditional prevention-based security has been compromised or bypassed. Robust backup processes, including air-gap backups, should also be considered to make it more difficult for criminals to encrypt or disable critical data stores.
Consequences
If an organization falls victim to a double extortion ransomware attack, there are often dire consequences. Criminal groups are increasingly blatant, even dystopian names like Maze, Netwalker and REvil, are an indication of this inclination. Their pride leads them to display exfiltrated data as online trophies and even sponsor clandestine hacking contests to display their malware. In a kind of cyber show-off . < / p>
For the victims, the consequences can be devastating. Travelex, a currency exchange service, went into receivership with the loss of 1,300 jobs in the UK following a ransomware attack . During the heist, the cyber gang REvil asked the company to pay $ 6 million in 48 hours. The company has faced the threat of publishing credit card information, national insurance numbers and birth dates of its customers.
It is clearly critical that companies do everything they can to identify and stop these attacks before they cause more damage. Preventing these attacks proactively is much better than mitigating their effects, with all the financial costs and reputational damage they entail .
Most attackers gain access through human error . For this, together with technical measures such as internal data access management and back-up, staff training and supervision are key elements in an organization’s defenses .
Victims essentially have two choices, both of which are costly: if they refuse to pay, they face a catastrophic data breach with exposure to painful regulatory fines and civil demands; if they pay the ransom, they still have no guarantee that the data will be returned.

Handle double-extortion ransomware
While getting hit by ransomware can deal a severe blow to any business, companies should be cautious when asked to pay a ransom. Doing so could involve even greater risks . There is no certainty that these hackers will not ask for more money without releasing the data anyway.
It is important for companies to secure their networks and conduct mock test < / a> to mitigate the ransomware threat . Such simulated attacks will help spot vulnerabilities within the organization without the risk of facing serious financial problems and having to answer very difficult questions from customers.
Implementing strong resilience measures is the best way to prevent double extortion ransomware. Ransomware is often a secondary infection. Threat actors seek to exploit known vulnerabilities, particularly in relation to remote access protocols and applications that are critical for working from home.
Critical to mitigating this is ensuring that vulnerabilities are patched in a timely manner and that network data logs are monitored for any unusual activity or data exfiltration. < / strong> There is therefore a potential window of opportunity to remedy any primary infection (which precedes the ransomware) and thus prevent the ransom note process from developing.
Education
Organizations need to educate staff about the risks of double extortion ransomware and how it is executed . Individual users can also be of great help by being aware of the potential of unsafe attachments. They should also be cautious about clicking any email links received in any communication , particularly with the recent resurgence of Emotet , a known malware.
There are two defense strategies for dealing with double extortion ransomware. First, robust backups, to make sure you don’t your hands tied if hackers gain control of your data. Then, encryption, to make sure that if an attacker threatens to expose your data, it’s protected too.
These approaches should then be incorporated into a broader strategy: careful monitoring of the network that could allow attackers to be cut off, and promoting employee IT education not to fall victim to phishing attacks which are often the main cause of a ransomware incident.
The threat of double extortion ransomware is undeniable, with cybercriminals carefully targeting and creating these attacks in an attempt to increase the size of ransom.
Organizations often feel they have no choice but to pay the ransom to avoid the leak of sensitive data. But it’s actually a Russian roulette game and the stolen information can still find its way online. Therefore the focus must be on prevention and risk mitigation .

A common definition of data exfiltration is the theft, removal, or unauthorized movement of any data from a device. Data exfiltration typically involves a cybercriminal stealing data from personal or corporate devices, such as computers and cell phones, through various cyberattack methods.
Failure to control information security can lead to data loss which can cause financial and reputational damage to an organization.
How does a data exfiltration happen?
Data exfiltration occurs in two ways, through attacks from outsiders and through threats from within. Both are major risks, and organizations need to ensure their data is protected by detecting and preventing data exfiltration at all times.
An attack from outside the organization occurs when an individual infiltrates a network to steal corporate data or user credentials. This is typically the result of a cybercriminal injecting malware into a device connected to a corporate network.
Some malware strands are designed to spread across an organization’s network and infiltrate others, seeking sensitive data in an attempt to extract. Other types of malware remain dormant on a network to avoid being detected by organizations’ security systems until data is subversively extracted or information is gradually collected over a period of time.
Attacks can result from malicious insiders stealing your organization’s data and sending documents to your personal email address. Typically the data is then sold to cyber criminals. They can also be caused by inattentive employee behavior that sees corporate data fall into the hands of bad actors.
Types of Data Exfiltration
Data exfiltration occurs in various ways and through multiple attack methods, mostly on the Internet or on a corporate network.
The techniques cybercriminals use to extract data from organizations’ networks and systems are becoming increasingly sophisticated. These include: anonymous connections to servers, Domain Name System (DNS) attacks, Hypertext Transfer Protocol (HTTP) tunneling, Direct Internet Protocol (IP) addresses, fileless attacks, and remote code execution.
Let’s see in detail some attack techniques to know what we are talking about specifically.
1. Social engineering and phishing attacks
Social engineering attacks and phishing attacks are popular network attack vectors. They are used to trick victims into downloading malware and entering their account credentials.
Phishing attacks consist of emails designed to appear legitimate and often appear to come from trusted senders. They usually contain an attachment that injects malware into the device. Other types contain a link to a website that appears legitimate but is forged to steal the login credentials entered. Some attackers even launch targeted phishing attacks to steal data from a specific user. Often the targets are the executives of a company or known individuals.
To defend against these types of attacks, it’s best to recognize them immediately and trash the emails. In a company it is possible to help the process through an ad hoc training course, based on data collected internally by the company through a controlled test. SOD also offers this service, if you are interested, you will find more information on the page of the service itself.
2. Outgoing email
Cybercriminals check e-mails to retrieve any data coming out of organizations’ e-mail systems. The recovered data can be calendars, databases, images and planning documents. These provide sensitive information of value or information that is useful for recovering valuable data.
3. Download to unsafe devices
This method of data exfiltration is a common form of accidental insider threat. The attacker accesses sensitive corporate information on his trusted device, then transfers the data to an insecure device. The insecure device could be an external drive or smartphone that is not protected by corporate security solutions or policies, which puts it at risk of data exfiltration.
Smartphones are also susceptible to data exfiltration. Android devices are vulnerable to the installation of malware that take control of the phone to download applications without the user’s consent.
4. Upload to external devices
This type of data exfiltration typically comes from bad guys. The internal attacker can extract data by downloading the information from a secure device, then uploading it to an external (insecure) device. This external device could be a laptop, smartphone, tablet or USB stick.
5. Human error and unsafe behavior on the network
The cloud provides users and businesses with a multitude of benefits, but together there are significant risks of data exfiltration. For example, when an authorized user accesses cloud services in an insecure way, it allows an attacker an access route from which he can retrieve data and take it off the secure network. Human error also plays a role in data mining, because appropriate protection may no longer be in place.
How to spot a data exfiltration attack
Depending on the type of attack method used, detecting data exfiltration can be a difficult task. Cybercriminals using more difficult-to-detect techniques can be mistaken for normal network traffic. This means that they can lurk in networks unnoticed for months and even years. Data exfiltration is often only discovered when the damage has already been caused.
To detect the presence of at-risk users, organizations must use tools that automatically discover malicious or unusual traffic in real time.
One tool with this capability is SOC (also offered as a service: SOCaaS) which implements an intrusion monitoring system, as well as an automatic system that verifies user behavior. When the SOC detects a possible threat, it sends an alert to the organization’s IT and security teams who can take action and investigate the situation.
SOC works by searching for and detecting anomalies that deviate from regular network activity. They then issue an alert or report so administrators and security teams can review the case.
In addition to detecting automatic threats, organizations can also construct the entire sequence of an event as it occurred, including mapping to a known kill chain or attack framework.
Using a SOCaaS, for a company that manages sensitive data, is an advantage from many points of view. Being offered as a service, the company will not have to invest in setting up a specialized IT department for its SOC, will not have to hire additional personnel and will be able to count on security systems that are always updated with qualified and always available operators.
For more information, do not hesitate to contact us.
Useful links:
Test your business with ethical phishing attacks
Customers
Twitter FEED
Recent activity
-
SecureOnlineDesktop
Estimated reading time: 6 minutes L'impatto crescente delle minacce informatiche, su sistemi operativi privati op… https://t.co/FimxTS4o9G
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The growing impact of cyber threats, on private or corporate operating systems… https://t.co/y6G6RYA9n1
-
SecureOnlineDesktop
Tempo di lettura stimato: 6 minuti Today we are talking about the CTI update of our services. Data security is… https://t.co/YAZkn7iFqa
-
SecureOnlineDesktop
Estimated reading time: 6 minutes Il tema della sicurezza delle informazioni è di grande attualità in questo peri… https://t.co/tfve5Kzr09
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The issue of information security is very topical in this historical period ch… https://t.co/TP8gvdRcrF
Newsletter
{subscription_form_1}© 2024 Cyberfero s.r.l. All Rights Reserved. Sede Legale: via Statuto 3 - 42121 Reggio Emilia (RE) – PEC [email protected] Cod. fiscale e P.IVA 03058120357 – R.E.A. 356650 Informativa Privacy - Certificazioni ISO