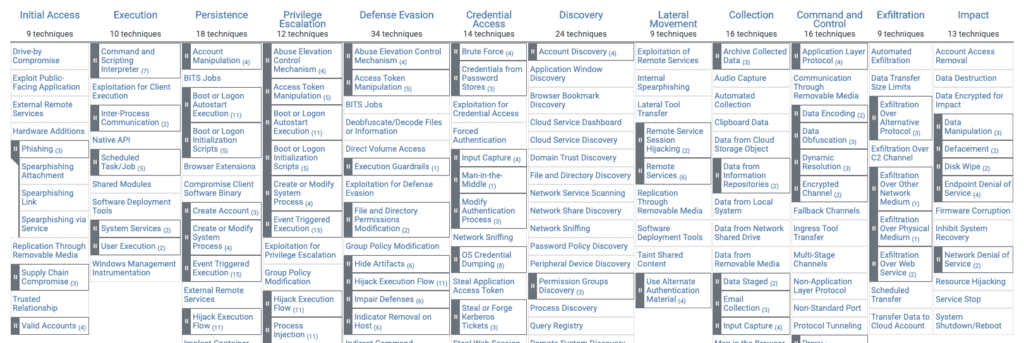
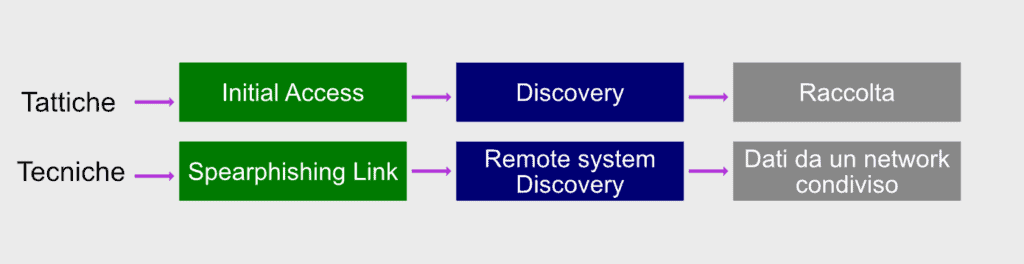
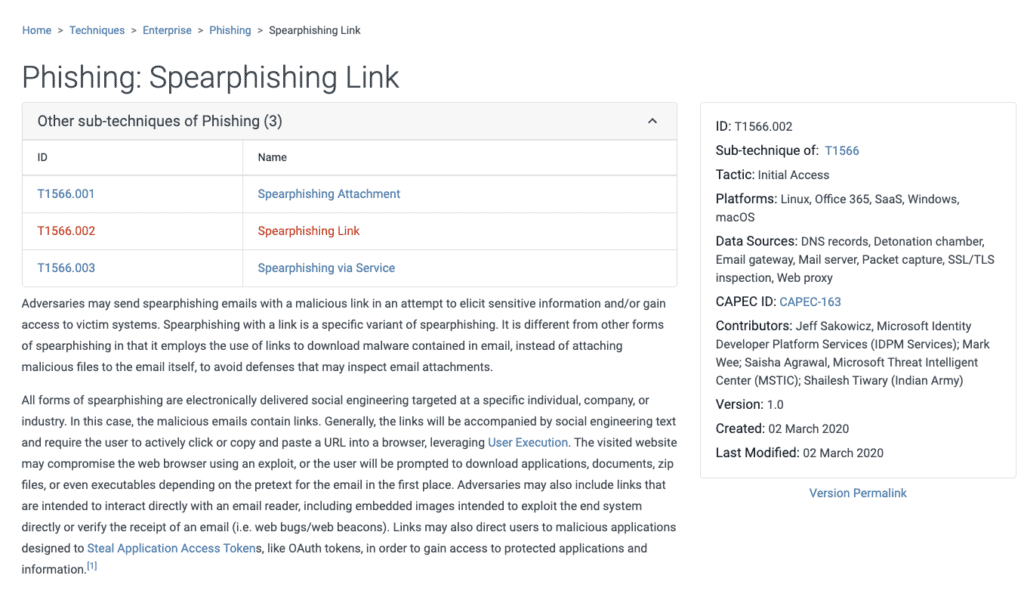
Estimated reading time: 6 minutes
When we talk about cybersecurity and find ourselves on the side of the attacked, we often limit ourselves to thinking in terms of defense, protection and containment of threats. However, the approach that works best is one in which you put yourself in the attacker’s shoes and treat your infrastructure as the target of their actions. Only in this way is it possible to address the discussion holistically and not from a single point of view. To execute this change of mentality, we refer to the various actors in the scene as teams: red team, blue team and purple team. Today we shed some light on the differences between the hacker teams involved in the action.
Definition of Teams and their purpose
The Red Teams are internal or external entities dedicated to testing the effectiveness of a security program emulating the tools and techniques of likely attackers as realistically as possible. The practice is similar to, but not identical to Penetration Testing, and involves the pursuit of one or more goals, usually performed as a campaign.
The Blue Team they refer to Internal security team that defends against both real attackers and Red Teams. Blue Teams must be distinguished from standard security teams in most organizations, as most security operations teams do not have a mindset of constant vigilance against attacks, which is the mission and outlook of a true Blue Team.
The best Blue Team members are those who can employ adversarial empathy techniques, that is, think deeply like the enemy. This mentality is usually dictated more than anything else by attacking experience.
This mentality is usually dictated more than anything else by attacking experience. They do this by integrating the defensive tactics and controls of the Blue Team with the threats and vulnerabilities found by the Red Team in a single action that maximizes both. Ideally, the Purple Team shouldn’t be a team, but rather a permanent dynamic between Red and Blue.

To further delve into the points of view, let’s take a closer look at the teams.
Red Team
Red Teams are often confused with Penetration Testers, but while they have a huge overlap in skills and functions, they are not the same thing. They have a number of attributes that separate them from other offensive security teams. The most important of these are:
1. Emulazione delle TTP(tecniche, tattiche e procedure)utilizzate dagli avversari. They use tools similar to bad actors: exploits, pivot methodologies and typical objectives of a black hat hacker.
2. Campaign-based testing that extends over an extended period of time, for example, multiple weeks or months of emulating the same attacker.
Penetration testing is when a security team uses standard tools, runs tests for only a week or two, and tries to achieve a standard set of objectives. For example, breaking into the internal network, stealing data or obtaining domain administration. A Red Team campaign uses a customized set of TTPs and objectives over an extended period of time.
Of course, you can create a Red Team campaign that uses the best known TTPs, a combination of ongoing pentesting tools, techniques and objectives, and run it as a campaign.
Blue Team
The goal here is not to protect entry, but rather to encourage curiosity and a proactive mindset. Blue Teams are a company’s proactive defenders from a cybersecurity perspective.
There are a number of defense-oriented tasks that are not considered worthy of the Blue Team. For example, a Level 1 SOC analyst who has no training or interest in offensive techniques, no curiosity about the interface he is looking at, and no creativity in following up on any potential alerts is unlikely to be a valuable member of a Blue Team.
All Blue Teams are defenders, but not all defenders are part of a Blue Team.
What constitutes a Blue Team member and differentiates it from dealing with defense is the mentality. Here’s how to make the distinction: Blue Teams have and use:
1. A proactive, non-reactive mindset
2. Deep curiosity about things that are out of the ordinary
3. Continuous improvement in detection and response
It’s not about whether someone is a self-taught Level 1 SOC analyst or a former Red Team member. It’s about curiosity and the desire to constantly improve.
Purple Team
The Purple Team is more of a cooperative mindset between attackers and defenders working on the same side. As such, it should be thought of as a function rather than a separate team.
The true purpose of a Red Team is to find ways to improve the Blue Team, so Purple Teams should not be necessary in organizations where Red Team/Blue Team interaction is healthy and functioning properly.
The best uses of the term Purple Team are when a group unfamiliar with offensive techniques wants to learn how attackers think. It could be an incident response group, a detection group, a developer group, anything. If the good guys are trying to learn from white hat hackers, this can be considered a Purple Team exercise.

Conclusions
While Red and Blue Teams have the same goal of improving an organization’s security, they are too often unwilling to share their “secrets.” Attackers sometimes don’t reveal the methods they used to infiltrate systems, while defense teams don’t say how attacks were detected and blocked.
However, sharing these “secrets” is critical to strengthening the company’s security posture. The value of the red and blue teams is null if they do not share their research and reporting data. This is where the Purple Team comes in.
Purple Team members get their Red and Blue teammates to work together and share insights into their assets, relationships and knowledge. To do this, you should focus on promoting communication and collaboration between members of the two core teams.
How to use these mentalities in the company
When you outsource enterprise security with SOCaaS and the execution of Vulnerability Assessments and Penetration Tests, the various teams are completely external. The services offered by SOD are based on best practices regarding the work of Red and Blue Teams, generating a Purple Team mentality.
With us the security of your company is in good hands. Our engineers have experience and are used to collaborating to achieve maximum results.
Contact us to find out more about how our services can help in corporate defense, we will be happy to answer any questions.
Useful links:

Estimated reading time: 5 minutes
Just like any other IT field, the cybersecurity market is driven by hype . Currently hype towards XDR, ie eXtended Detection and Response .
XDR is the latest in threat detection and response, a key element of a company’s infrastructure and data defense .
What exactly is XDR?
XDR is an alternative to traditional responsive approaches that only provide layer visibility on attacks . I refer to procedures such as detection and endpoint response (EDR), network traffic analysis (NTA) and SIEM , which we have talked about in many other articles.
The layer visibility implies that various services are adopted, stratified (layers), which each keep under control a specific entity in the infrastructure. This can be problematic. In fact, you need to make sure that layers don’t end up isolated, making it difficult, or nearly impossible to manage and view data. layer visibility provides important information, but can also lead to problems, including :
Collecting too many incomplete and contextless alerts. EDR detects only 26% of initial attack vectors and due to the high volume of security alerts, 54% of professionals security ignores warnings that should be investigated .
Complex and time-consuming investigations requiring specialist expertise . With EDR, the median time to identify a breach has increased to 197 days, and the median time to contain a breach has increased to 69 days.
Tools focused on technology rather than user or business . EDR focuses on technology gaps rather than the operational needs of users and companies. With more than 40 tools used in an average Security Operations Center (SOC), 23% of security teams spend their time maintaining and managing security tools rather than investigating . ( Source )
For already overloaded security teams, the result can be an endless stream of events , too many tools and information to switch between, longer time frames for detection and security expenses that are beyond budget and are not even fully effective .
What’s new in eXtended Detection Response
XDR implements a proactive approach to threat detection and response . It offers visibility into data across networks, clouds and endpoints, while applying analytics and automation to address today’s increasingly sophisticated threats. The benefits of the XDR approach for security teams are manifold:
Identify hidden, stealth and sophisticated threats proactively and quickly.
Track threats across any source or location within your organization. < br> Increase the productivity of people working with technology.
Get more from their security investments .
Conclude investigations in a way more efficient .
From a business perspective, XDR enables companies to detect cyber threats and stop attacks, as well as simplify and strengthen security processes. As a result, it enables companies to better serve users and accelerate digital transformation initiatives. When users, data and applications are protected, companies can focus on strategic priorities.
Why consider it for your company
The two main reasons why this approach is beneficial are: endpoints do not have visibility into threats in places like cloud services , and it may not be possible to put a < em> software agent on all company endpoints .
But there are other reasons to consider too. The addition of other data sources can provide more context in the EDR results, improving triage and investigation of alerts . Providers are moving not only to provide more and better organized data, but also by delivering analytics platforms to lighten the analytical load on operators. This translates into ease of use and reduced operating costs.
XDR can seem very attractive as a product: Tight integration of parts, highly tuned content (as the provider has total control over the events from the data sources), use of analytics and response automation.

What to pay attention to before adoption
Some providers are positioning their XDR as the ultimate threat detection solution . However, many vendors are unable to offer all the tools needed to get the advantage sold. Some providers offer endpoint and cloud monitoring in the package, others endpoint and network monitoring, but when looking at the comprehensive needs of most organizations, there are often missing details in the overall picture.
And if, once the company engages with a provider and notices a lack in one of the monitored sectors, what are the possible solutions? A situation of vendor lock-in from which to break free means to sever a contract and then open another one, with all the consequent costs.
XDR as an approach, not as a product
Before entering into a contract with a provider that sells a solution as final, it is always good to weigh the benefits and implications analytically.
Tight, two-way integration of multiple threat detection and response capabilities is the first distinguishing feature. But it is not necessary to buy two technology components from the same vendor to achieve good integration. Indeed, many products have the ability to integrate with some solutions from other vendors as one of their main strengths.
The XDR approach must provide a platform that allows the necessary data collection and storage , but also strong analytical skills, to orchestrate and automate response actions provided by the other parts of the solution. A cloud based Next Generation SIEM is a perfect solution.
How to move then?
The interest in XDR products is a clear signal that excessive fragmentation was leading to excessive complexity. A little consolidation is good, but it must be done while protecting flexibility and the ability to follow the best solutions.
In our opinion, a SOCaaS is an optimal solution. Provides next generation SIEM , with strong analytical capabilities. In addition, it also integrates artificial intelligence that helps in time to recognize threats through behavior analysis. A SOCaaS is the future of security operating platforms.
To find out with our services they can help you protect the data of your company and your customers, contact us, we will gladly answer all your questions.
Useful links:

Estimated reading time: 6 minutes
I dati di threat intelligence forniscono alle aziende approfondimenti rilevanti e tempestivi necessari per comprendere, prevedere, rilevare e rispondere alle minacce alla sicurezza informatica. Le soluzioni di intelligence sulle minacce raccolgono, filtrano e analizzano grandi volumi di dati grezzi relativi a fonti esistenti o emergenti di minacce. Il risultato sono feed di threat intelligence e rapporti di gestione. I data scientist e i team di sicurezza utilizzano questi feed e report per sviluppare un programma con risposte mirate agli incidenti per attacchi specifici.
Tutti, dalla prevenzione delle frodi alle operazioni di sicurezza all’analisi dei rischi, traggono vantaggio dalla threat intelligence. Il software di intelligence sulle minacce fornisce visualizzazioni interattive e in tempo reale dei dati relativi alle minacce e alle vulnerabilità.
Il vantaggio offerto agli analisti ed esperti di sicurezza è evidente e serve a identificare facilmente e rapidamente i modelli degli attori delle minacce. Comprendere la fonte e l’obiettivo degli attacchi aiuta i capi d’azienda a mettere in atto difese efficaci per mitigare i rischi e proteggersi dalle attività che potrebbero avere un impatto negativo sull’azienda.
La cyber threat intelligence può essere classificata come strategica, tattica oppure operativa. Quella Strategica riguarda le capacità e gli intenti generali degli attacchi informatici. Di conseguenza anche lo sviluppo di strategie informate associate alla lotta contro le minacce a lungo termine. Quella Tattica riguarda le tecniche e le procedure che gli aggressori potrebbero utilizzare nelle operazioni quotidiane. Infine, la threat intelligence Operativa, fornisce informazioni altamente tecniche a livello forense riguardanti una specifica campagna di attacco.

Il ciclo della threat intelligence
Le soluzioni di intelligence sulle minacce raccolgono dati grezzi sugli attori e le minacce da varie fonti. Questi dati vengono poi analizzati e filtrati per produrre feed e rapporti di gestione che contengono informazioni che possono essere utilizzate in soluzioni automatizzate di controllo della sicurezza. Lo scopo principale di questo tipo di sicurezza è quello di mantenere le organizzazioni informate sui rischi delle minacce persistenti avanzate, delle minacce zero-day e degli exploit, e su come proteggersi da esse.
Il ciclo di intelligence delle minacce informatiche consiste nelle seguenti fasi.
Pianificazione: I requisiti dei dati devono essere prima definiti.
Raccolta: Si raccolgono grandi quantità di dati grezzi da fonti interne ed esterne di threat intelligence.
Elaborazione: I dati grezzi sono filtrati, categorizzati e organizzati.
Analisi: Questo processo trasforma i dati grezzi in flussi di informazioni sulle minacce con l’uso di tecniche analitiche strutturate in tempo reale e aiuta gli analisti a individuare gli indicatori di compromissione (IOC).
Diffusione: I risultati dell’analisi vengono immediatamente condivisi con i professionisti della sicurezza informatica e gli analisti di threat intelligence.
Feedback: Se tutte le domande trovano risposta, il ciclo si conclude. Se ci sono nuovi requisiti, il ciclo ricomincia dalla fase di pianificazione.
Indicatori comuni di compromissione
Le aziende sono sempre più sotto pressione per gestire le vulnerabilità della sicurezza e il panorama delle minacce è in continua evoluzione. I feed di threat intelligence possono aiutare in questo processo identificando gli indicatori comuni di compromissione (IOC). Non solo, possono anche raccomandare i passi necessari per prevenire attacchi e infezioni. Alcuni degli indicatori di compromissione più comuni includono:
Indirizzi IP, URL e nomi di dominio: Un esempio potrebbe essere un malware che prende di mira un host interno che sta comunicando con un noto attore di minacce.
Indirizzi e-mail, oggetto delle e-mail, link e allegati: Un esempio potrebbe essere un tentativo di phishing che si basa su un utente ignaro che clicca su un link o un allegato e avvia un comando dannoso.
Chiavi di registro, nomi di file e hash di file e DLL: Un esempio potrebbe essere un attacco da un host esterno che è già stato segnalato per un comportamento nefasto o che è già infetto.

Quali strumenti per la threat intelligence
Il crescente aumento del malware e delle minacce informatiche ha portato a un’abbondanza di strumenti di threat intelligence che forniscono preziose informazioni per proteggere le aziende.
Questi strumenti si presentano sotto forma di piattaforme sia open source che proprietarie. Queste forniscono una serie di capacità di difesa contro le minacce informatiche, come l’analisi automatizzata dei rischi, la raccolta di dati privati, strumenti di ricerca rapida di threat intelligence, la segnalazione e condivisione di queste informazioni tra più utenti, avvisi curati, analisi dei rischi di vulnerabilità, monitoraggio del dark web, mitigazione automatizzata dei rischi, threat hunting e molto altro.
Abbiamo parlato di uno di questi strumenti in un altro articolo: il Mitre Att&ck. Questo è uno strumento molto utile per conoscere i comportamenti e le tecniche di attacco hacker. Questo grazie alle informazioni raccolte dalla threat intelligence e la conseguente condivisione. Un framework come questo è molto efficiente per creare meccanismi difensivi che consentono di mettere in sicurezza le infrastrutture aziendali.
Intelligenza artificiale e informazioni sulle minacce
Come abbiamo visto prima, la raccolta di informazioni da varie fonti non è altro che una delle fasi. Queste devono poi venire analizzate e successivamente elaborate in protocolli di controllo, per essere davvero utili per la sicurezza.
Per questo tipo di lavori di analisi, definizione di comportamenti baseline e controllo dei dati ci si affida sempre di più all’intelligenza artificiale e al deep learning. Un Next Generation SIEM, affiancato a una soluzione UEBA sono perfetti per questo tipo di protezione.
Il controllo del comportamento delle entità all’interno del perimetro effettuato dal UEBA è in grado di identificare ogni comportamento sospetto, in base alle informazioni raccolte e analizzate dal SIEM.
Conclusioni
Gli strumenti di difesa che abbiamo nominato sono il valore primario di un piano di sicurezza aziendale. Adottare soluzioni specifiche, implementare la threat intelligence e quindi una ricerca attiva degli indicatori di minacce, offre una posizione di vantaggio strategica. L’azienda può operare un passo avanti ai criminali, i quali possono far leva solo sull’effetto sorpresa contro le loro vittime. Proprio per questa situazione generale, ogni azienda dovrebbe essere nelle condizioni di non farsi cogliere alla sprovvista. Implementare soluzioni proattive è ormai necessario.
La threat intelligence è quindi un’arma da difesa dietro la quale mettere al riparo le risorse più importanti per poter lavorare in tranquillità.
Se vuoi sapere come possiamo aiutarti con i nostri servizi dedicati alla sicurezza, non esitare a contattarci, saremo lieti di rispondere a ogni domanda.
Useful links:
Cyber Threat Intelligence (CTI) – maggiore efficacia per la sicurezza IT
Progetti di Secure Online Desktop
Cos’è la Cyber Security? Definizione e proposte
Prevenire il shoulder surfing e il furto di credenziali aziendali

Estimated reading time: 5 minutes
New cybersecurity threats continue to emerge every day and hackers develop new intrusion techniques to access sensitive data and breach IT systems. This is why it is necessary to collaborate with high-level experts who keep track of new developments in the field of IT security. With the birth and continuous evolution of Big Data, the concept of Data Lake and Security Data Lake has also established itself.
For a company, it is expensive to hire a team that deals exclusively with the internal security of a system, which is why many turn to professionals, using a Security Operations Center as a Service (SOCaaS) This service, offered by SOD, also includes an SDL. Let us now try to understand what it is and what their importance and convenience is.
Security Data Lake: what they are

Un Data Lake è un archivio che include grandi quantità di dati, strutturati e non, che non sono stati ancora elaborati per uno scopo specifico. These have a simple architecture to store data. Each item is assigned a unique identifier and then tagged with a set of metadata.
When a business question arises, data scientists can query the Data Lake in order to discover data that could answer the question. Since the Data Lakes are sources that will store sensitive company information, it is necessary to protect them with effective security measures, however the external data ecosystem that feeds the Data Lakes is very dynamic and new problems could regularly arise that undermine its security.
Users authorized to access Data Lakes, for example, could explore and enrich its resources, consequently also increasing the risk of violation. If this were to occur, the consequences could be catastrophic for a company: violation of employee privacy, regulatory information or compromise of business-critical information.
A Security Data Lake, on the other hand, is more focused on security. It offers the possibility of acquiring data from many security tools, analyzing them to extract important information, mapping the fields following a common pattern.
The data contained in an SDL
There are countless different varieties of data, in different formats, JSON, XML, PCAP and more. A Security Data Lake supports all these types of data, ensuring a more accurate and efficient analysis process. Many companies leverage Big Data to develop machine learning-based threat detection systems. An example, for this eventuality, is the UEBA system integrated with the SOCaaS offered by SOD.
A Security Data Lake allows you to easily access data, making it available, also offering the opportunity for real-time analysis.
Apache Hadoop
It is a set of Open Source programs that allows applications to work and manage an enormous amount of data. The goal is to solve problems that involve high amounts of information and computation.
Apache Hadoop includes HDFS, YARN, and MapReduce. When we talk about Hadoop, therefore, we are referring to all those tools capable of interfacing and integrating with this technology. The role of Hadoop is essential because with them it is possible to store and process data at a very low cost compared to other tools. Furthermore, it is possible to do this on a large scale. An ideal solution, therefore, for managing an SDL.

Hadoop Distributed File System (HDFS): is one of the main components of Apache Hadoop, it provides access to application data without having to worry about defining schemas in advance.
Yet Another Resource Negotiator (YARN): It is used to manage computing resources in clusters, giving the possibility of using them to program user applications. It is responsible for managing the allocation of resources throughout the Hadoop ecosystem.
MapReduce: is a tool with which processing logic can be transferred, thus helping developers write applications capable of manipulating large amounts of information in a single manageable dataset.
What advantages does Hadoop offer?
It is important to use Hadoop because with it You can leverage clusters of multiple computers to analyze large amounts of information rather than using a single large computer. The advantage, compared to relational databases and data warehouse, lies in Hadoop’s ability to manage big data in a fast and flexible way.
Other advantages
Fault tolerance: Data is replicated across a cluster, so it can be easily recovered in the event of disk or node errors or malfunctions.
Costs: Hadoop is a much cheaper solution than other systems. It provides compute and storage on affordable hardware.
Strong community support: Hadoop is currently a project supported by an active community of developers who introduce updates, improvements and ideas, making it an attractive product for many companies.
Conclusions
In this article we learned the differences between a Data Lake and a Security Data Lake, clarifying the importance of using these tools in order to guarantee the correct integrity of the IT systems present in a company.
Collecting infrastructure data is only the first step for efficient analysis and the resulting security offered by monitoring, essential for a SOCaaS. Ask us how these technologies can help you manage your company’s cyber security.
For doubts and clarifications, we are always ready to answer all your questions.
Useful links:

Estimated reading time: 4 minutes
When we refer to artificial intelligence, we often refer to the great technologies that could control the world, with an obvious streak of science fiction. The reality is very different and is characterized by a technology with great potential, which is able to ensure countless advantages . Today we talk about how artificial intelligence can be implemented in monitoring.
The use of these technologies is unavoidably transversal to many sectors of the economy, but it is also usable in some aspects of everyday life. Some examples range from washing machines that, weighing the load of laundry, are able to choose the most advantageous washing program, to voice assistants that simplify our everyday life.
Very important in the corporate sector are the monitoring systems which were created precisely from these technologies which we will talk more about in a moment.
Thanks to the optimization of the computing capacity operated by artificial intelligence, it is possible to increase the efficiency of company equipment. Let’s see how.

What is artificial intelligence and how can it innovate monitoring ?
Today, artificial intelligence is declined in many ways. Perhaps the most important is processing a large amount of data then providing answers to complex questions. At the base of artificial intelligence there is the study of algorithms that deal with performing complex mathematical operations.
Artificial intelligence is a very useful tool within a company, as it is able to carry out very sophisticated and precise processing. These operations are capable of significantly improving the operations and productivity of numerous departments of the company itself.
Applied to monitoring, for example, artificial intelligence is capable of analyzing the logs coming from the network, both in terms of performance and behavior. The big step forward in the analysis and monitoring of an infrastructure consists precisely in recognizing whether certain behaviors that emerge from the logs are risky or not.
To achieve these results it is essential to have all those features that are available through artificial intelligence .
What are the advantages of using artificial intelligence for monitoring?
Artificial intelligence is able to provide companies that choose to use it countless advantages. Not only in terms of improving the performance of information systems, but also to make more efficient and improve the security of the same, preventing attacks.
This happens thanks to the analysis of the logs both from a technical and a behavioral point of view. Technical analysis highlights any ongoing problems, while behavioral analysis can prevent or immediately identify suspicious actions.
How can our monitoring system improve business efficiency?
Our monitoring system is able to improve business efficiency through numerous technical analyzes in able to be implemented not only on the entire system, but also on individual units.
The ability to analyze data in depth also allows you to improve the management of the entire IT structure and prevent overloads or attacks. Overall, the efficiency and safety of the infrastructure are increased at the same time through artificial intelligence applied to monitoring.
But there’s more: these analysis and monitoring systems are able to integrate with extreme effectiveness in complex architectures. By being able to analyze large amounts of data and being able to deduce behaviors and actions from these, efficiency in security is ensured.
Another advantage is the fact that this monitoring system does not require specific hardware. Software agents are installed on the systems to be controlled which have the sole task of sending data in the form of a log to the control system. analyses.
These systems therefore prove to be the ideal solution to keep large and small IT architectures under control, with the aim of improving efficiency and increasing overall security. In short, an application really interesting and useful of artificial intelligence in monitoring.

What are the fields of application of this technology?
We apply artificial intelligence systems to monitoring, benefiting our customers enormously. First we can collect large amounts of data, enrich it automatically and finally analyze it. The analyzes are carried out both from a technical and a behavioral point of view.
The result is a dedicated system, our SOCaaS, which makes risk mitigation extremely efficient, particularly quick intervention in the event of an anomaly and also provides regular reports.
This service is able to bring together all the features listed in the article, and to offer it as a solution for companies that want a superior security system.
Better efficiency, safety, versatility, operability, are just some of the paradigms used to define the services we make available to our customers. Our main goal is to simplify and make your company’s IT security more efficient.
Do not hesitate to contact us if you want to know more, we will be happy to answer any questions.
Useful links:
Tempo di lettura stimato: 6 minutes
Today we are talking about the CTI update of our services. Data security is an aspect that must always be taken into consideration to prevent data from being stolen in any way.
Network problems
When you have a presence connected to the network, especially if it contains sensitive data, the potential threats to which you are exposed are manifold. The theft of your customers’ data, in fact, is only one of the potential negative situations that can arise and that could compromise the solidity of your site and the reputation of your company.
The Cyber Threat Intelligence (CTI) service, was created with the aim, not only of discovering which areas are most at risk, but also of preventing targeted attacks. Prevention represents the right solution thanks to which it is possible to avoid that the situation can become difficult to deal with and that there may be future complex problems to be solved.

CTI: preventive-threat analysis
Thanks to the CTI service we offer and our Cyber Treath Hunter , it is possible to prevent a planned attack hits. The search for vulnerable areas of the IT infrastructure represents the first process of the CTI service we propose.
This information, in fact, is that which is processed in the Dark Web , where most of the design of the attacks. The analysis of data leakage, therefore, is carried out with extreme care to understand what and how much data may have become the object of hacker attention . Consequently, we can also understand what specific attack targets or upcoming information at risk may be.
The various analyzes are carried out with care and precision, to avoid that vulnerabilities are exploited and the security of the structure jeopardized. Thanks to the analysis carried out by a team of professionals, your company will prevent attacks from hitting you and triggering economic and image problems .
The analyzes carried out by Cyber Threat Intelligence
As regards the different phases of the analyzes proposed by us, these are carried out in a particularly accurate manner. We practice a series of procedures thanks to which it is possible to identify what are the potential threats that may be present in the network.
Let’s look at these steps to understand how we go about offering a complete service to our customers.
Global-data analysis
After having hypothesized the type of threat to be avoided, then the necessary data that must be analyzed, the team of technicians in charge takes care of carrying out a series of information gathering procedures. Thanks to this we can understand if the necessary data are well protected or at risk of breach . Basically we try to think like hackers before they prepare for the attack.
The data are subjected to careful analysis and above all are adequately divided. This procedure was created to simplify the phase of studying the data themselves , thus preventing an accumulation of information that could lead to confusion during the analysis phase.
The data and the second-analysis, between fundamental and secondary information
Once the information gathering phase is complete, we move on to the initial analysis of the same. With this fundamental step it is possible to eliminate all the information deemed superfluous leaving space for those that have greater relevance in the study phase.
At this point, the data analysis phase takes place, the purpose of which is to actually understand what concrete threats to avoid can be.
During the study phase it is decided which are the different procedures to be adopted on the infrastructure to prevent attacks from being successful. Through these analyzes, we can then decide precisely how to further increase corporate data defenses.
The choice of security-measures to be adopted
Finally, there is the implementation of security practices with a specific task: to make the analysis results operational.
Here’s how, thanks to this set of procedures, the CTI service we offer is incredibly useful to avoid potential problems. We remind you that even a single attack carried out can have a significant impact in economic terms.
Prevention of future-attacks
Thanks to this set of CTI analyzes, you can, therefore, prevent future attacks. Our team is not only concerned with analyzing potential and future threats, but also those that may be based on the current situation of the IT infrastructure.
We want to underline, in fact, how constant threats are subject to rapid evolution and how important it is to always be adequately protected and prevented. With services like SOCaaS and CTI, we securely monitor the corporate network making sure it remains safe and healthy.

CTI: The importance of maximum-online-security
We therefore encourage you to consider these security risk situations as less remote than you might think. These same situations can be the cause of a series of breaches and data losses that can compromise the company.
Thanks to our SOCaaS, and especially the CTI. it is possible to avoid that the data present on the corporate network can be easily intercepted.
Understanding what the threats are, having a detailed report and above all analyzing the countermeasures that must be adopted is our task and thanks to our state-of-the-art systems we offer a complete service capable of putting the infrastructure in total safety.
Our services cover many security risk situations and we generally offer many professional solutions for companies. The SOCaaS, with system SIEM and UEBA, as well as CTI and
Keeping safety always on top is our job, if you want more information, don’t hesitate to contact us!
Useful links:
Estimated reading time: 6 minutes
Today we see one of the latest additions to our SOCaaS, the Autonomous Threat Sweeper (ATS) . A system able to support SOC in an innovative way and protect against the most innovative threats.
The Privacy Guarantor, through the provision dated May 27, 2021, has introduced some changes regarding the violation of sensitive and personal data. A particular reference was made to the numerous cases of data breach. In essence, the legislation relating to the notification system has been tightened . The legislation provides for the application of a certain procedure to be adopted in the event of a data breach.
It is not easy to stay up to date on the continuous regulations on privacy, nor to have IT threat prevention systems available such as i ransomware working in the shadows and increasingly aggressive and dangerous. For this reason, threat protection has become an issue that is no longer easily manageable through non-professional systems . Today specific IT skills are constantly updated and professionals working in the sector, especially for companies.

Context: the unstoppable growth of ransomware
As we know, the term ransomware defines a category of malware capable of encrypting the files and documents contained in the attacked computer, in some cases even on the network to which it is connected. We have seen this in various articles through known examples .
In recent years, ransomware has spread enormously, so much so that it is listed as the most dangerous cyber threat to businesses .
Among the main companies targeted are those that have a large amount of sensitive data which, if stolen, would expose the company to the distrust of their customers. The encryption of the files stored inside the devices is, therefore, resolved only following the payment of a ransom.
Unfortunately, once compromised, the system does not allow users to access the data on their devices, effectively preventing their use.
Currently, ransomware is one of the main cyber threats, so much so that it is categorized as a profitable business model. This is because of the constant improvements made to their software that make it easier for hackers to use. The result is an increasing number of attacks performed with tools that required almost no specific skills.
IT security: increased risk = increased insurance policies
In terms of computer security, the aspects to consider are different, among these, in fact, there is the one related to ransomware software. These require a greater definition of reporting requirements in the event of a data breach due to an increase in systemic risk.
This problem has led to an increase in the prices of the insurance market. As these threats, in addition to being more and more frequent, are the cause of high damage to companies, insurance companies have raised their prices. But not only that, today they also demand specific requirements from the policyholders, to demonstrate the use of adequate defense systems in the IT field.
Autonomous Threat Sweeper: the new technology integrated in SOCaaS
Preventive malware detection is the priority solution to be adopted in order to avoid the risk of being attacked by malware that can steal company data.
What is worrying, however, is not only the increase in the cost of insurance, but the greater definition of the required requirements. The requirements, that is, relating to the reports to be forwarded in the event of a data breach and the consequent increase in systemic risk .
The SOC as a Service is a service entirely dedicated to the IT security of companies, which involves data collection and enrichment aimed at proactive identification of social engineering attacks. The system includes a Security Data Lake (SDL), the event and information management (SIEM) and l ‘user behavior analysis (UEBA).
Through the Autonomous Threat Sweeper (ATS) the team is able to provide companies with 24/7 coverage through an automatic search. This, once activated, is able not only to to prevent attacks from the outside, but also to detect any malware previously installed on company devices.
This system allows you to automate the rapid detection of these threats. Once identified, it is easy to implement targeted actions in order to counter their attacks. Since cyber attacks are and will always be present in everyday business life, it is certainly important to be well equipped. Attacks will continue to grow in breadth and scale and let’s not forget the trend in the shortage of technicians . We can only bring into play systems that automate the first stages of control and detection.
The Autonomous Threat Sweeper (ATS) is currently one of the few systems capable of pre-coding the latest generation of cyber attacks . Its coverage includes corporate networks and devices.

Autonomous Threat Sweeper (ATS)
Autonomous Threat Sweeper (ATS) is a constantly updated system capable of detecting the latest generation threats. This guarantees companies that turn to us to always be protected from the latest generation IT risks to infrastructures and devices.
We have already talked about SIEM , software tools able to provide cyber security professionals with an analysis of logs and events to provide real-time threat minitoring. Here, the ATS even improves the functionality of software as complex and accurate as SIEM, making it capable of detecting low and slow threats through post-hoc.
Basically, with the ATS it will be possible to speed up the process of detecting threats in order to avoid damage that also compromises the strength of the infrastructure.
Conclusions: How to behave in case of violation
In the event that an IT breach occurs, with or without intent, involving the loss, destruction, modification or unauthorized disclosure or unauthorized access to the data processed by a company, the data controller appointed by the same must notify the violation within 72 hours.
Subsequently, investigations could take place to understand the extent of the damage and then also penalties in case of negligence. By adopting an Autonomous Threat Sweeper your business will be able to intercept threats before they can do any harm.
Preventing data breaches, ransom requests and other cyber security attacks is easy if you turn to competent people. Ask us for more details on how we can support your company with regards to cybersecurity. We will be happy to answer all your questions.
Useful links:
Webinar: SOCaaS (Security Operation Center as a Service) e NGS (Next Generation SIEM)
Pass the Ticket: how to mitigate it with a SOCaaS
Use cases of a SOCaaS for companies part 2
Use cases of a SOCaaS for companies part 1
Predictive cybersecurity with our SOCaaS

Cyberattacks are numerous and do not distinguish between companies and individuals when targeting a target. You’ve most likely heard the term “cyber threat” in the media before, but what exactly are we talking about? Other ways you may have heard this are “cyberthreat”, “cyberattack” or similar.

What is a Cyber Threat?
Today the term “cyber threat” is used predominantly in the world of information security.
A cyber threat is a malicious act conceived with the purpose of damaging systems, stealing data or any purpose that has the purpose of causing damage of any kind. Viruses, data breaches and DDoS attacks are included. Even if the threat is virtual, what is real is the attacker’s intent as well as the potential impact. While many cyberattacks are mere nuisances, some are quite serious. Some even potentially threaten human lives.
The potential impact that these kinds of attacks can have is often underestimated. Most of the time, the attacks are easily identifiable and do not pose much risk. Instead, other times it happens to come across some more sophisticated threats, difficult to identify, which represent a big problem even for many companies.
Cyber threats are a major concern for businesses. Cyberattacks can lead to power outages, government equipment failures, and breaches of state secrets. They can manipulate telephone and computer networks or, as in the case of ransomware, they can cripple entire systems by making data inaccessible.
Every day new companies and organizations set foot in the digital world with awareness of the risks associated with their technological infrastructures. In some cases, cyber threats are underestimated and this often means great economic and image damage for the company that has underestimated cyber threats and security.
The increase in IT-related risks is real, as are data security solutions. The best thing to do is to take the necessary safety measures right away.
Types of Cyber Threats
The types of cyber threats are numerous, and it must also be considered that they are constantly evolving. The intent of hackers is usually to secure an economic gain by carrying out sabotage, espionage or data theft operations. As a result, they can be expected to do everything possible to achieve their ends.
Virtually every cyber threat falls into one of the following ten types of risks. Hackers have an abundance of options to choose from in order to operate. Furthermore, computer literacy is all in all poor, so hackers often have an easy time, especially for small local realities.
The 10 most common types of computer threats
Malware
It is a type of software that executes a malicious command on a device or within a computer network, corrupting data or taking control of the system.
Phishing
Phishing is an e-mail attack that consists of tricking the recipient into revealing confidential information or inviting him to download malware by clicking on a link in the body of the message. These are real scams, which we have talked about extensively in other articles. Often they don’t even involve great IT skills on the part of the attacker, just a little social engineering.
Vishing
Vishing is a more sophisticated form of phishing in which the hacker uses VoIP technology to contact the victim, attempting to trick them. There is also a variant that instead uses text messages to attack, it is called smishing.
Man in the Middle
As the name suggests, this type of attack refers to when a hacker intervenes in a conversation posing as one of the two parties, with the aim of stealing sensitive information. What we often don’t think about is that the conversation is between two machines and therefore not immediate to monitor.
Trojan viruses
The origin of its name is inspired by the famous Trojan Horse of ancient Greece. Trojan is a type of malware that infiltrates a computer system by hiding its true nature. For example, it could impersonate known software and then release malicious code once inside the host device.
Ransomware
Ransomware is an attack that uses encryption to make information on a system inaccessible. The aim is to demand a ransom in exchange for being able to access the data again. Possibilità che a volte, in realtà, non è nemmeno assicurata.
DDoS attack
It occurs when the attacker uses many devices to overload a target, such as a website, with requests, causing it to crash or become instabilities.
Attacks on IoT devices
This is an increasingly popular attack due to the nature of the targets. Devices such as sensors or industrial plants connected to the network are vulnerable to multiple types of cyber threats. The hacker could take control of the device and then later use it in a DDoS attack. Alternatively it could steal the information present in the device itself obtaining important data to continue the attack. Given their number of frequently out-of-date operating systems, IoT devices are a very attractive target.
Malware in mobile applications
Phones and tablets are just as vulnerable to malware as any other device. È possibile inserire malware all’interno di app, nei siti web o nelle e-mail sfruttando il phishing. Once compromised, a mobile device can provide access to personal information, location data, and financial accounts.
A recent example of this type of eventuality is Pegasus software, which is used to monitor and collect data from journalists around the world. (Source: The Guardian)
Practical defense and prevention solutions
Cyber threats are always expanding and improving. Millions of them are created every year, many of them follow the aforementioned characteristics, but others are technologically more complex and more powerful.
Fortunately, however, there are also more and more highly qualified companies in the field of IT security that offer cutting-edge tools and services that help prevent, identify and promptly block all kinds of IT attacks.
Threat detection tools
Threat detection tools are an essential part of a company’s cybersecurity technology stack. Threat detection is also the first defense against any Cyber Threat.
Specific solutions, such as the use of a SOCaaS, for example, are of vital importance for safeguarding an IT infrastructure, thanks also to the integration of the SIEM engine which includes UBA and UEBA, guaranteeing complete control also over the users.
Another useful tool is definitely ACP. Acronis Cyber Protect is a solution that integrates data protection and management to safeguard your endpoints, data and systems. Its automation capabilities provide unparalleled protection, enabling businesses to increase their productivity and reduce risk.
Vulnerability Assessment & Penetration Test (VA-PT)
Services like VA & PT are field tests that test the infrastructure in a concrete context. Our teams of white hat hackers find vulnerabilities within the system to point the finger at weaknesses to fix.

Conclusions
We have learned what a cyber threat is and its most common types, also discovering which solutions can be adopted in order to guarantee better corporate and employee safety.
What countermeasures has your company taken to protect your safety? If you would like more information about it, you can contact us by pressing the button below. We offer ad hoc services and solutions to strengthen corporate defenses.
Useful links

Estimated reading time: 7 minutes
Phishing is a type of social engineering attack often used to steal user data, including login credentials and credit card numbers . Occurs when an attacker, disguised as a trusted entity , tricks a victim into opening an email, instant message, or text message.
The recipient is then tricked into clicking on a malicious link, which can lead to malware installation , system freezing as part of an attack ransomware or the disclosure of sensitive information.
An attack can have devastating results . For individuals, this includes unauthorized purchases, fund theft or identity theft.

What is Phishing for Business?
Even more damaging, phishing is also used to gain an entry point into corporate or government networks as part of a larger attack , such as a persistent advanced threat event (APT – Advanced Persistent Threat). In the latter scenario, employees are compromised in order to bypass security perimeters , distribute malware within a closed environment, or gain privileged access to protected data.
An organization that succumbs to such an attack typically suffers severe financial losses, as well as a decline in market share, reputation and consumer confidence. Depending on the scope, a phishing attempt could escalate into a security incident that a company will have difficulty recovering from .
What a phishing attack looks like
Knowing what phishing is often isn’t enough to protect yourself . The best thing to do is work on resilience to attacks and understand how to spot them before falling victim to them.
As we mentioned earlier, the consequences can be enormous. But, if it seems simple to do when it comes to a single individual, what if there is an entire company to protect? SOD offers a service geared towards just that : train entire companies to recognize and mitigate the risk of phishing attacks.
Through a first controlled attack, we are able to understand which are the points to work on . Subsequently, training proposals for employees are organized. They are taught how to recognize threats before they become problematic. To find out more, visit the service page .
But let’s see what a generic attack looks like.
Attack example
1. A bogus email ostensibly from myuniversita.edu is being distributed en masse to as many faculty members as possible.
2. The email claims that the user’s password is about to expire . Instructions are given to go to the myuniversita.edu/rinnovo link to renew their password within 24 hours.
Various things can happen by clicking on the proposed link.
– The user is redirected to myuniversita.edurinnovo.com , a fake page that looks exactly like the real renewal page, where both the new password are requested than the existing one. The attacker, monitoring the page, hijacks the original password to – gain access to secure areas of the university network.
– The user is sent to the real password renewal page. However, while being redirected, a malicious script runs in the background to hijack the user’s session cookie. This results in a Cross Site Scripting attack, giving the author privileged access to the university network.

Logic of an attack
Email phishing is a big game . An attacker who sends thousands of fraudulent messages can obtain significant information and sums of money, even if only a small percentage of recipients fall into the scam .
Hackers go to great lengths to design messages for a phishing attack by mimicking real emails from a disguised organization. Using the same phrasing, the same typefaces, the same logos and the same signatures, the messages appear legitimate .
Also, another thing to watch out for is that attackers usually try to push users into action by creating a sense of urgency. For example, as shown above, an email could threaten account expiration and put the recipient in urgency . Applying this pressure leads the user to be less diligent and more prone to error.
Finally, the links within the messages resemble their legitimate counterparts, but typically have a misspelled domain name or extra subdomains. In the above example, the URL myuniverist.edu/rinnovo has been changed to myuniversita.edurinnovo.com . The similarities between the two addresses give the impression of a secure connection , making the recipient less aware that an attack is in progress.
What is spear phishing

Spear phishing targets a specific person or company , as opposed to casual users. It’s a more in-depth version of phishing that requires special knowledge of an organization, including its power structure.
An attack could take place like this:
– A hacker searches for employee names within an organization’s marketing department and gains access to the latest project invoices.
– Posing as the director of marketing , The attacker sends an email to a project manager in the department using a subject that says: Updated invoice for Q3 campaigns . The included text, style, and logo duplicate the organization’s standard email template.
– A link in the email redirects to a password-protected internal document, which is actually a forged version of a stolen invoice .
– The marketing director is required to login to view the document. The attacker steals his credentials , gaining full access to sensitive areas within the organization’s network.
By providing the attacker with valid login credentials, spear phishing is an effective way to carry out the first phase of a ransomware attack.
What is whale phishing
whale phishing , or whaling , is a form of spear phishing that targets very big fish: CEOs or other high-value targets . Many of these scams target members of a company’s board of directors, who are considered particularly vulnerable. Indeed, they have great authority within the company, but because they are not full-time employees, they often use personal email addresses for business-related correspondence , which does not have the protections offered by email business.
whale phishing , or whaling , is a form of spear phishing that targets very big fish: CEOs or other high-value targets . Many of these scams target members of a company’s board of directors, who are considered particularly vulnerable. Indeed, they have great authority within the company, but because they are not full-time employees, they often use personal email addresses for business-related correspondence , which does not have the protections offered by email business.
How to defend yourself
Protecting against a phishing attack requires action by both users and businesses.
For users, vigilance is the key . A forged message often contains subtle errors that expose its true nature. These can include misspellings or changes to domain names , as seen in the example of the preceding URL. Users should be wondering why they are receiving a certain email .

For businesses, a number of measures can be taken to mitigate both phishing and spear phishing attacks:
Two-factor authentication (2FA) is the most effective method of thwarting phishing attacks, as adds an extra layer of verification when accessing sensitive applications . 2FA is based on users having two things: something they know , like a password and username, and something they have with them , like their smartphone . Even when employees are compromised, 2FA prevents the use of their compromised credentials, as these alone are not enough to get in .
In addition to the use of 2FA, companies should apply strict password management policies . For example, employees should be required to change their passwords frequently and not be allowed to reuse a password for multiple applications .
Finally, educational campaigns can also help decrease the threat of phishing attacks by enforcing safe practices , such as not clicking on external links to emails. In this regard, I would like to mention the ethical phishing service of SOD , which has the very intent of testing the company and organizing targeted training to mitigate the risks .
It’s not enough to know what phishing is, you also need to know how to recognize it.
Useful links:

Estimated reading time: 5 minutes
A Zero-Day attack (also known as 0-day) exploits a software vulnerability unknown to security officers and the software vendor. Hackers can exploit the weakness, as long as it is not mitigated, through Zero-Day exploit or, indeed, attack.
The term “zero-day” originally referred to the number of days after the software was released. A “zero-day” software, therefore, meant a program obtained by forcing a developer’s computer before release. The term was then applied to the vulnerabilities that this practice allows to exploit. Once the vendor becomes aware of the vulnerability, they usually patch or recommend solutions to mitigate it.
Software vulnerabilities
Software often has vulnerabilities. These are unintentional flaws, or code problems that could hypothetically be exploited.For example, there may be a flaw that allows a cybercriminal to access otherwise secure data. Programmers are often on the lookout for these vulnerabilities and when they discover them, they analyze them, produce a patch to fix them, then distribute that patch in a new version of the software.
However, this is a time-consuming process. When the flaw becomes known, hackers around the world can start trying to exploit it.
Zero-Day Attack
If a hacker manages to exploit the vulnerability before the developers find a solution, this exploit then becomes known as a Zero-Day attack.
Zero-day vulnerabilities can take almost any form, because they can manifest themselves as any type of vulnerability in software. For example, they can take the form of missing data encryption, SQL injection, buffer overflows, missing permissions, bugs, or problems with password security.
This makes these vulnerabilities difficult to find before they are exploited in zero-day attacks. This, in some ways, is good news: it also means that hackers will have a hard time finding them. But also that it is difficult to defend against these vulnerabilities effectively.
How to protect yourself
We have seen how difficult it is to protect yourself from the possibility of a zero-day attack, because it can take many forms. Almost any type of security vulnerability could be exploited as a zero-day if a patch is not produced in time. Also, many software developers intentionally try not to disclose the vulnerability publicly in the hope that they can distribute a patch before any hacker discovers the vulnerability.
There are a few strategies that can help you defend your business against zero day attacks:
Stay informed on Zero-Day attacks
Zero-day exploits aren’t always advertised, but occasionally we hear about a vulnerability that could potentially be exploited. If you stay tuned to the news and pay attention to releases from your software vendors, you may have time to put security measures in place or respond to a threat before it is exploited. A good way to do this is to follow your suppliers’ newsletters. At the bottom of this page you will find the form to subscribe to the SOD one.
Keep your systems up to date
Developers are constantly working to keep their software up to date and secure to prevent the possibility of exploits.When a vulnerability is discovered, it is only a matter of time before they produce a patch. However, it is up to you and your team to make sure your software platforms are always up to date. The best approach in this case is to enable automatic updates, so that the software is updated routinely, and without the need for manual intervention.
Use additional security measures
Make sure you’re using security solutions that protect you from a zero-day attack. SOD offers a solution that includes a set of tools that allow you to raise your defenses significantly. SOCaaS is a real security operations center for your company. Using state-of-the-art tools such as SIEM and UEBA and thanks to granular control over the monitored network, every attack attempt is identified in the shortest possible time.
Each type of data produced by the interconnected systems in the infrastructure is collected, normalized and analyzed for anomalies. This means that not only are you checking for known indicators of compromise (IOC), but suspicious operations and behavior of facility users are also monitored. In this way, it is also possible to identify attack attempts that are normally very difficult to detect, such as those involving Zero-Day Attacks, but not only. In fact, through the SOCaaS service, it is possible to identify compromised accounts, the violation of protected data, lateral movement attacks, phishing, etc.
The security of a company’s IT system is a very important topic that we care a lot about. The compromise or loss of sensitive data can cost a lot from both an economic and a reputational point of view. Do not neglect this important aspect for the safety of your business, contact us to tell us about your situation, we will be happy to show you how we can help you.
Useful links:
Vulnerability Assessment and Penetration test
Protecting a site in WordPress: security package
Long-term search: what’s new in the SOCaaS service
Contact us

A common definition of data exfiltration is the theft, removal, or unauthorized movement of any data from a device. Data exfiltration typically involves a cybercriminal stealing data from personal or corporate devices, such as computers and cell phones, through various cyberattack methods.
Failure to control information security can lead to data loss which can cause financial and reputational damage to an organization.
How does a data exfiltration happen?
Data exfiltration occurs in two ways, through attacks from outsiders and through threats from within. Both are major risks, and organizations need to ensure their data is protected by detecting and preventing data exfiltration at all times.
An attack from outside the organization occurs when an individual infiltrates a network to steal corporate data or user credentials. This is typically the result of a cybercriminal injecting malware into a device connected to a corporate network.
Some malware strands are designed to spread across an organization’s network and infiltrate others, seeking sensitive data in an attempt to extract. Other types of malware remain dormant on a network to avoid being detected by organizations’ security systems until data is subversively extracted or information is gradually collected over a period of time.
Attacks can result from malicious insiders stealing your organization’s data and sending documents to your personal email address. Typically the data is then sold to cyber criminals. They can also be caused by inattentive employee behavior that sees corporate data fall into the hands of bad actors.
Types of Data Exfiltration
Data exfiltration occurs in various ways and through multiple attack methods, mostly on the Internet or on a corporate network.
The techniques cybercriminals use to extract data from organizations’ networks and systems are becoming increasingly sophisticated. These include: anonymous connections to servers, Domain Name System (DNS) attacks, Hypertext Transfer Protocol (HTTP) tunneling, Direct Internet Protocol (IP) addresses, fileless attacks, and remote code execution.
Let’s see in detail some attack techniques to know what we are talking about specifically.
1. Social engineering and phishing attacks
Social engineering attacks and phishing attacks are popular network attack vectors. They are used to trick victims into downloading malware and entering their account credentials.
Phishing attacks consist of emails designed to appear legitimate and often appear to come from trusted senders. They usually contain an attachment that injects malware into the device. Other types contain a link to a website that appears legitimate but is forged to steal the login credentials entered. Some attackers even launch targeted phishing attacks to steal data from a specific user. Often the targets are the executives of a company or known individuals.
To defend against these types of attacks, it’s best to recognize them immediately and trash the emails. In a company it is possible to help the process through an ad hoc training course, based on data collected internally by the company through a controlled test. SOD also offers this service, if you are interested, you will find more information on the page of the service itself.
2. Outgoing email
Cybercriminals check e-mails to retrieve any data coming out of organizations’ e-mail systems. The recovered data can be calendars, databases, images and planning documents. These provide sensitive information of value or information that is useful for recovering valuable data.
3. Download to unsafe devices
This method of data exfiltration is a common form of accidental insider threat. The attacker accesses sensitive corporate information on his trusted device, then transfers the data to an insecure device. The insecure device could be an external drive or smartphone that is not protected by corporate security solutions or policies, which puts it at risk of data exfiltration.
Smartphones are also susceptible to data exfiltration. Android devices are vulnerable to the installation of malware that take control of the phone to download applications without the user’s consent.
4. Upload to external devices
This type of data exfiltration typically comes from bad guys. The internal attacker can extract data by downloading the information from a secure device, then uploading it to an external (insecure) device. This external device could be a laptop, smartphone, tablet or USB stick.
5. Human error and unsafe behavior on the network
The cloud provides users and businesses with a multitude of benefits, but together there are significant risks of data exfiltration. For example, when an authorized user accesses cloud services in an insecure way, it allows an attacker an access route from which he can retrieve data and take it off the secure network. Human error also plays a role in data mining, because appropriate protection may no longer be in place.
How to spot a data exfiltration attack
Depending on the type of attack method used, detecting data exfiltration can be a difficult task. Cybercriminals using more difficult-to-detect techniques can be mistaken for normal network traffic. This means that they can lurk in networks unnoticed for months and even years. Data exfiltration is often only discovered when the damage has already been caused.
To detect the presence of at-risk users, organizations must use tools that automatically discover malicious or unusual traffic in real time.
One tool with this capability is SOC (also offered as a service: SOCaaS) which implements an intrusion monitoring system, as well as an automatic system that verifies user behavior. When the SOC detects a possible threat, it sends an alert to the organization’s IT and security teams who can take action and investigate the situation.
SOC works by searching for and detecting anomalies that deviate from regular network activity. They then issue an alert or report so administrators and security teams can review the case.
In addition to detecting automatic threats, organizations can also construct the entire sequence of an event as it occurred, including mapping to a known kill chain or attack framework.
Using a SOCaaS, for a company that manages sensitive data, is an advantage from many points of view. Being offered as a service, the company will not have to invest in setting up a specialized IT department for its SOC, will not have to hire additional personnel and will be able to count on security systems that are always updated with qualified and always available operators.
For more information, do not hesitate to contact us.
Useful links:
Test your business with ethical phishing attacks
UEBA: Behavior Analysis Explained


A legitimate question that often arises is whether the Penetration Test is necessary for compliance with the ISO 27001 standard. To fully understand the answer, it is necessary to clarify what is meant by these terms and to understand the relationship between all the components of the certification.
ISO 27001 standard
A technical standard, also incorrectly called a standard, is a document that describes the specifications that a certain object / body / entity must comply with in order to be certified. In general, a standard describes the requirements of materials, products, services, activities, processes, terminology, methodologies and other aspects concerning the subject of the standard. In very simple words, norms are rules that regulate almost everything by offering constructive and methodological standards.
The ISO 27001 standard (ISO / IEC 27001: 2013) is the international standard that describes the best practices for an ISMS, Information Security Management System. Although following the standard is not mandatory, it is necessary to obtain a certification to guarantee logical, physical and organizational security.
Obtaining an ISO 27001 certification demonstrates that your company is following information security best practices and provides independent and qualified control. Safety is guaranteed to be in line with the international standard and company objectives.
Of great importance for the ISO 27001 standard is Annex A “Control objective and controls”, which contains the 133 controls that the company concerned must comply with.
Vulnerability Assessment and Penetration Test
When performing a Vulnerability Assessment on the network and computer systems, the aim is to identify all technical vulnerabilities present in operating systems and software. Some examples of vulnerabilities can be SQL Injection, XSS, CSRF, weak passwords, etc. The vulnerability detection indicates that there is a recognized security risk due to a problem of some kind. It does not say whether or not it is possible to exploit the vulnerability. To find out, it is necessary to carry out a Penetration Test (or pentest).
To explain the above, imagine that you have a web application that is vulnerable to SQL Injection which could allow an attacker to perform operations on the database. A VA identifies this vulnerability, ie it may be possible to access the database. Following the vulnerability assessment, if a pentest is performed and the vulnerability can be exploited, the risk would be demonstrated.
To comply with control A.12.6.1 of Annex A of the ISO 27001 standard, it is necessary to prevent the exploitation of technical vulnerabilities. However, the decision on how to proceed is up to you. Is it therefore necessary to perform a Pentest? Not necessarily.
After the vulnerability analysis, we could fix and fix the weaknesses and eliminate the risk before performing a pentest. Therefore, for the purposes of compliance with the ISO 27001 standard, the required result can be obtained simply by performing the vulnerability assessment and solving the potential problems that have arisen.
Having said that, we strongly recommend that you carry out a complete Penetration Test to be really sure of compliance with the standard. It can help you prioritize problems and tell you how vulnerable your systems are.
Contact professionals
Esistono sul mercato diverse soluzioni per svolgere pentest. Sono software che possono agevolare il lavoro e facilitare il test, ma se azionati da personale inesperto, possono anche creare dei problemi. e’ possibile che la rete ne risulti rallentata e i computer sensibilmente meno reattivi, fino anche a possibili crash di uno o piu’ dei sistemi coinvolti.
Puntando alla certificazione per lo standard ISO 27001, e’ meglio non fare gli eroi e assicurarsi davvero che i controlli siano rispettati. Richiedere l’intervento di professionisti del settore, serve proprio a minimizzare i rischi e assicurarsi che il processo sia svolto in modo impeccabile.
SOD offre un servizio di verifica delle vulnerabilita’ e pentest affidandosi ad hacker etici professionisti. Dopo un primo colloquio, le varie fasi del processo sono eseguite per verificare e testare le potenziali minacce. E’ possibile anche richiedere che la verifica delle vulnerabilita’ sia svolta con regolarita’ per verificare la sicurezza dei sistemi.
Richiedi informazioni specifiche, oppure visita la pagina dedicata. Per ulteriori informazioni sulle nostre certificazioni, e’ possibile visitare l’apposita pagina.
There are several solutions on the market to perform pentest. They are software that can facilitate the work and facilitate the test, but if operated by inexperienced personnel, they can also create problems. it is possible that the network will be slowed down and the computers noticeably less reactive, up to possible crashes of one or more of the systems involved.
Aiming for ISO 27001 certification, it’s best not to be heroes and really make sure the controls are respected. Requesting the intervention of professionals in the sector serves precisely to minimize risks and make sure that the process is carried out flawlessly.
SOD offers a vulnerability verification and pentest service relying on professional ethical hackers. After an initial interview, the various stages of the process are carried out to verify and test potential threats. It is also possible to request that the verification of vulnerabilities be carried out regularly to verify the security of the systems.
Request specific information, or visit the dedicated page. For more information on our certifications, you can visit the appropriate page.
[btnsx id=”2931″]
Useful links:
Security: pentest and verification of vulnerabilities

During a cyber attack, hackers have only one goal in mind. This goal could be accessing a developer’s machine and stealing a project’s source code, analyzing emails from a particular executive, or extracting customer data from a server. All they have to do is log into the machine or system that contains the data they want, right? Not exactly. Actually, it’s a little more complicated than that. To achieve their goal, hackers are likely to break into a low-level web server, email account, or employee device, to name a few. From that node, they will move sideways (hence the name network lateral movement) to achieve their goal.
In fact, when attackers compromise a resource on a network, that device is almost never their final destination. In addition, the initial compromise rarely causes serious damage and may go unnoticed. Only if the security teams are able to detect a lateral movement before the attackers reach their intended goal, it is possible to prevent the data breach.
In this article, we will look at some of the more common types of network lateral movement and identify ways in which we can detect the attack and defend ourselves.
Understanding the network lateral movement
Lateral movement occurs when an attacker takes possession of a resource within a network and then extends its reach from that device to others within the same network. Let’s see it with an outline to help us understand better.
The perimeter of the infrastructure to be penetrated is represented with a horizontal line. The upper half represents what is outside the net, while what is below the line represents what is inside. In order for an attacker to enter the network, it must move vertically, ie from the outside to the inside (also called North-South traffic). But once a foothold has been established, it is possible to move sideways or horizontally, ie within the same network (called East-West traffic) to reach the final goal of the attack.
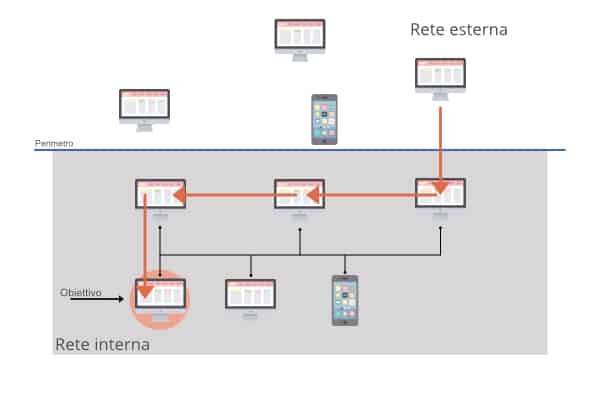
Possible path of a lateral movement. The arrow indicates the network nodes that are involved in the attack.
Approaches to the Lateral Movement
Overall, there are two common methods by which a hacker applies the lateral movement.
First approach: The attacker performs an internal scan to find out what other machines are on the network. In particular, it scans open ports that are listening and machines that suffer from vulnerabilities. At that point, the attacker can abuse these weaknesses to move sideways to another resource.
The second approach to the lateral movement exploits stolen credentials, and is the more common of the two. In this type of attack, the hacker could use an email phishing technique to infect a machine that interfaces with a particular server. Then he can use his login to recover passwords via a keylogger or other similar tools. At this point, he can use whatever credentials he was able to obtain to impersonate the user who was the victim of the phishing and log in to another machine. Once you have established access to that computer, you can repeat the tactic looking for additional credentials and / or privileges to exploit. In this way, the attacker can make their way and create remote connections to the target device.
In both cases it is difficult to identify the attack, because it does not occur through software or application malfunctions.
How to defend yourself
A lateral movement often manifests itself through anomalous network activity. For example, it is suspicious that a machine, which normally communicates with a few others, starts scanning the entire network. The same is true if that machine tries to connect to open ports, to interact with services and credentials with which it normally has no contact, or to use a username that has never been used before.
The list of alarm bells goes on and on. The key thing to understand is that a lateral movement involves machines doing something out of their routine, without proper authorization from IT.
This is what gives organizations the ability to detect this type of attack. Implementing log file monitoring is a first step in defense. Ideally, the data should be constantly analyzed for anomalies and possible breaches.
Defense issues
These defenses are not infallible. Security teams that simply rely on log files limit the scope of their defensive position, for example, due to log files collected only from particular applications. You might decide to monitor a certain service for credential theft, but attackers might not use that particular service to perform a lateral movement. This means that any malicious actions that do not use the monitored services will not be detected promptly.
In addition to this, hackers know the types of protocols that security personnel tend to monitor, making their task even more complex. Attackers can use this knowledge to model their attack campaigns in order to have a better chance of going unnoticed. It is one of the reasons why the MITER ATT & CK database was created to collect known techniques and raise the defenses.
The advantage of a SOCaaS
It is not enough for organizations to seek lateral movement using log files or an EDR tool. It is necessary to turn attention to the network as a whole. In this way it is possible to see all network traffic, establish a baseline of normal network activity for each user and device, and then monitor any unusual actions that could be indicative of attacks. It is known as anomaly detection, and is more comprehensive and often easier than examining each log file for out-of-the-ordinary events.
The problem with anomaly detection is that many of these irregularities are benign, and a lot of time is spent analyzing them. What is needed to separate harmful lateral movement from benign network anomalies is an understanding of the aspect of harmful behavior.
This is where a complete system that uses both behavioral analysis tools and professional security technicians comes into play.
The SOCaaS offered by SOD includes a Security Data Lake (SDL) for data collection and various tools for data analysis. One of these is the UEBA, particularly suitable for the detection of social threats, as it analyzes user behavior through AI using their actions as a source of data.
With these and other tools that make up the SOC, you can actively reduce the risk of attacks on your corporate data. If you are interested in learning more about SOD SOCaaS, I invite you to visit the dedicated page or contact us directly.
[btnsx id=”2931″]
Useful links:
Is SOCaaS useful for your business
Computer Network Security: PT vs. VA
Cyber Security: Pentest and verification of vulnerabilities

Mitre Att&ck is a global knowledge base of adversary tactics and techniques based on real observations of cyber attacks. These are displayed in arrays organized by attack tactics, from initial system access and data theft to machine control. There are arrays for common desktop platforms (Linux, macOS and Windows) and for mobile ones.
What is MITRE ATT&CK ™ and what does it mean?
ATT&CK stands for “adversarial tactics, techniques, and common knowledge” and that is: tactics, adversary techniques and common knowledge. Let’s try to go deeper.
Tactics and techniques are a modern way of thinking about cyber attacks. Rather than looking at the results of an attack – an indicator of compromise (IoC) – security analysts should look at the tactics and techniques that indicate an attack is in progress. Tactics represent the goal you want to achieve, while techniques represent how an opponent plans to achieve it.
Common knowledge is the documented use of tactics and techniques used by opponents. Essentially, common knowledge is the documentation of the procedures used by the attacker. Those familiar with cybersecurity may be familiar with the term “tactics, techniques and procedures” or TTP. This same concept has been used by ATT&CK ™, replacing the term procedure with common knowledge.
Who is MITRE and what is the goal of ATT&CK ™?
MITRE is a US government funded research organization based in Bedford, MA, and McLean, VA. The company was spun off from MIT in 1958 and was involved in a number of top secret commercial projects for various agencies. These included the development of the FAA’s air traffic control system and the AWACS radar system. MITRE has a substantial cybersecurity practice funded by the National Institute of Standards and Technology (NIST).
A curiosity: the word Mitre means nothing. Apparently one of the first members, James McCormack, wanted a name that meant nothing but was evocative. Some mistakenly think it means Massachusetts Institute of Technology Research and Engineering.
ATT&CK’s goal is to create a comprehensive list of known opponent tactics and techniques used during a cyber attack. Open to governmental, educational and commercial organizations, it should be able to gather a wide, and hopefully comprehensive, range of attack phases and sequences. MITRE ATT&CK aims to create a standard taxonomy to make communications between organizations more specific.
How is the ATT&CK ™ matrix used?
The matrix visually organizes all known tactics and techniques in an easy to understand format. Attack tactics are shown above, and individual techniques are listed below in each column. An attack sequence would involve at least one technique per tactic, and a complete attack sequence would be constructed by moving from left (Initial Access) to right (Command and Control). It is possible to use more techniques for a single tactic. For example, an attacker might try both a Spearphishing Attachment and a Spearphishing Link as initial login tactics.
Here is an example of a matrix:
In this matrix there are all the phases of an attack sequence. It is organized so that the tactics are ordered from right to left according to the attack sequence. Under each tactic the corresponding techniques, some of which contain sub-techniques. The two techniques mentioned above are actually sub-techniques of phishing which are part of the first step in the sequence (first column on the left).
Example
It is not necessary for an attacker to use all eleven tactics at the top of the matrix. Rather, the attacker will use the minimum number of tactics to achieve his goal, as it is more efficient and provides less chance of discovery. In this attack (illustrated in the diagram below), the adversary performs initial access to the CEO’s administrative assistant credentials using a Spearphishing link delivered in an email. Once in possession of the administrator’s credentials, the attacker searches for a Remote System Discovery of the Discovery phase.
Let’s say they’re looking for sensitive data in a Dropbox folder that the admin also has access to, so there’s no need to increase privileges. The collection, which is the last stage, is done by downloading the files from Dropbox to the attacker’s machine.
Note that if you are using behavior analysis, a security analyst could detect the attack in progress by identifying abnormal user behavior.
And that’s exactly what a SOC should do, here, roughly, how the attack could be mitigated: suppose the administrator clicked a link that no one in the company has ever clicked before, then the administrator logged in a particular Dropbox folder at an unusual time. During the final phase of the attack, the attacker’s computer entered the Dropbox folder for the first time. With behavioral analysis, these activities would be flagged as suspicious user behavior.
To consult ATT&CK
To consult this resource just visit his site and you will find yourself in front of the matrix of which I published a screenshot a little while ago. Suppose we want to consult the Spearphishing Link technique. By clicking on it, the corresponding page will open containing in-depth information about it, such as a description of the technique, what sub-techniques exist, examples of procedures that include it and suggestions for risk mitigation.
Basically all the information necessary to know and defend oneself appropriately from each technique is available.
Conclusions
The advantages of a resource like MITRE ATT&CK are truly remarkable. Cyber security teams have a valuable ally at their disposal, to which they can add dedicated tools for its consultation.
While it is almost certain that attackers are adapting as defenders deploy new skills, it is also true that ATT&CK provides a way to describe the new techniques they develop.
[btnsx id=”2931″]
Useful links:
Security: Pentest and verification of vulnerabilities
What is a Network Lateral Movement and how to defend yourself
Is SOCaaS useful for your business?
Computer network security: PT vs. VA

In today’s article, we’ll explain what a Security Operations Center (SOC) is and help determine if a SOC-as-a-Service (SOCaaS) solution is right for your business. Just because you have to manage cybersecurity doesn’t mean your business has to deal with cybersecurity. In fact, your core business could be pretty much anything else.
Proper management of IT security, however, is essential to allow your company to grow and to obtain the certifications for data processing required by law. Having the right cybersecurity skills available at the right time is critical to your success, but you have no idea when that time will be.
Choosing the right technology, people and processes to build a modern security operations section is one of the biggest challenges for IT security managers.
What is a SOCaaS and what it can do for you
Before understanding what the management challenges are, it is good to understand what a SOC is. It performs the following functions:
Plan, configure and maintain your security infrastructure.
With a SOC it is possible to configure the technology stack (endpoint, SaaS applications, cloud infrastructure, network, etc.) to identify the relevant activity and eliminate unnecessary data. Monitor data sources to ensure the ecosystem is always connected.
Detect and respond
In addition, it is possible to monitor the incoming alarm activity. Investigate alarms to determine if it is a true security issue or a false alarm. If something is a real security threat, you can evaluate the magnitude of the situation and take response actions.
Threat hunting
The activity of a certain event can be examined to determine if there are any signs of impairment that may have eluded the automated controls. The most common scenario is to review the history of an IP address or file that has been determined to be malicious.
Storage of log files
Another possibility is to securely collect and archive log files, for up to seven years, for compliance with regulations. The team will need to provide this critical data for forensic analysis in the event of a security situation.
Measure performance indicators
Obviously it is possible to monitor the KPIs (performance indicators). In detail it is possible to measure and report the KPIs to demonstrate to the executive team how the SOC is working.
The challenges of implementing your own SOC
Finding, training and retaining cybersecurity professionals is expensive
The skills needed to manage IT security tasks are in high demand. Unfortunately, the shortage is bound to get worse before it gets better. According to the International Certification Organization (ISC), the number of vacant positions worldwide was over 4 million professionals in 2019, up from nearly three million the previous year.
Training personnel with a broad IT background in cybersecurity skills is an option, but retaining these people is expensive. Their replacement, when eventually taken elsewhere, starts a cycle that usually ends up being more expensive than expected, especially compared to SOCaaS.
Also, people who work well in this industry usually want to explore new topics and take on new challenges. You will need to find other related projects or roles to rotate SOC staff to keep them engaged. This also helps build their skills, so they are ready to respond and act promptly when needed.
Cyber security is a team sport
It is important to have a diverse set of skills and a team that works well as a team. Security threats evolve rapidly, proper investigation and responses require people who understand endpoints, networks, cloud applications, and more. Often you end up being a SOC manager, a sysadmin and a threat hunter, depending on the day and what happens in your environment.
This means that you will need a team that is constantly learning, so that you have the right skills when you need them. People who do well in this industry thrive in a team environment where they can learn and challenge each other. For this, you need a workflow that regularly brings together several SOC analysts.
Think of it this way: you wouldn’t put a football team on the pitch that didn’t train together. Your SOC team collides with an opponent who plays as a team every day. To be successful, you need professionals who have a lot of playing experience to build their skills both in the single position and as a team.
A team of SOC analysts who do not do regular training will not be ready when hit by a well-trained opponent. It is difficult to get this experience in a small organization.
A SOCaaS is the immediate answer to this need. The team that will take care of your IT security is trained and stimulated every day by ever new challenges, having to deal with different infrastructures every day.
24/7 coverage is a necessity
Letting an opponent be free to bait for hours, days or weeks makes it infinitely more difficult to contain and remove threats. The adversary knows they have limited time to do as much damage as possible, as in the case of ransomware, or to overshadow ports, as in the case of data extrusion.
You will have the best chance of recovery if you can investigate and respond within minutes. A solution that provides 24 × 7 coverage is therefore essential.
In computer security there are no “working hours” for one particular reason: an attack could come from anywhere on the globe, consequently you cannot rely on conventional hours. This is the result of the spread of the network as an instrument of worldwide connection, we can only deal with it adequately. A SOCaaS relieves the company using it from keeping a division open 24/7.
Managing suppliers and integrating tools is quite expensive
Cyber security is complex and technology evolves rapidly. There will be more and more technologies that need to work together, which requires maintaining the skills to implement, update and configure each component and train your staff on new versions and features. If you have your own SOC, you also need to manage these supplier relationships, licensing, and training.
The bottom line is that building the skills you need requires a lot of low-level tasks and extensive daily work. For organizations that can support it, the effort makes sense. For most organizations, the task is best left to a partner who can provide this service, allowing you to get all the benefits of a high-end SOC without the expense and distraction of building it yourself.
Conclusions
If budget is not an issue and you have enough staff to focus on building and maintaining a 24 × 7 SOC, then it may make sense to go this route. If you are constrained on one of these two fronts, then SOCaaS will be the best approach.
In summary, SOCaaS allows you to:
1. Spend time managing security, not technology and vendors
2. Have a predictable expense. No surprise budget requests
3. Obtain security information from other organizations
4. Manage alarms more efficiently and with more predictable results
5. Be agile and keep up with the IT needs of your evolving organization
6. Stay abreast of today’s security tool innovations.
If your company wants to know more about Secure Online Desktop SOCaaS solutions, contact us for a non-binding consultation. We will show you all the advantages and clear up any doubts regarding this solution.
[btnsx id=”2931″]
Useful links:
Computer network security: PT vs. VA
Cyber Security: Pentest and verification of vulnerabilities

The security of computer networks is of vital importance for a company. With technologies increasingly relying on remote services, it is good to ensure that security is guaranteed. To do this, two tools are used: Vulnerability Assessment and Penetration Test. But what is the difference between them? The answer to this question is not as obvious as one might think.
The short answer is: a Pentest (PT) may be a form of vulnerability assessment (VA), but a vulnerability assessment is definitely not a Pentest. Let’s try to better understand how they work and their purposes.
Verification of the security of computer networks: Vulnerability Assessment
A vulnerability assessment is the process of running automated tools against defined IP addresses to identify vulnerabilities in the environment in which one operates. Vulnerabilities typically include unprotected or misconfigured systems. The tools used to perform vulnerability scans are specific software that automates the process. Obviously these software are practically useless without an operator who knows how to use them correctly.
These tools provide an easy way to scan for vulnerabilities and there are both open source and proprietary ones. The main advantage of the open-source ones is that, with great probability, they are the same ones used by hackers, they are unlikely to pay an expensive subscription, when they can download open source applications for free.
In practice, a VA allows you to:
identify and classify security holes in the computer network
understand the cyber threats to which the company is exposed
recommend corrective measures to eliminate the weaknesses found
The purpose of a Vulnerability Assessment is to identify known vulnerabilities so that they can be corrected. Scans are typically done at least quarterly, although many experts recommend monthly scans.
How to perform a VA
Il processo di esecuzione si divide in due fasi e non prevede lo sfruttamento delle debolezze riscontrate. Questo ulteriore passaggio e’ invece previsto nel Penetration Test.
- Fase 1: prima analisi
- durante questa fase vengono raccolte tutte le informazioni disponibili sull’obiettivo per determinare quali potrebbero essere i punti deboli e le falle nel sistema di sicurezza delle reti informatiche
- Fase 2: seconda analisi
- in questa fase, tramite l’uso delle informazioni ricavate, vengono messe alla prova i possibili problemi. In questa fase le vulnerabilita’ sono testate per capire se siano effettivi problemi come supposto precedentemente.
Data l’incredibile velocita’ in cui le tecnologie e le tecniche informatiche si evolvono, e’ possibile che un sistema si mostri sicuro questo mese, ma abbia invece delle criticita’ da risolvere il mese successivo. Per questo e’ consigliato ripetere regolarmente e con frequenza i controlli di sicurezza sulle reti informatiche aziendali.
The execution process is divided into two phases and does not involve exploiting the weaknesses found. This further step is instead foreseen in the Penetration Test.
Phase 1: first analysis
during this phase, all the information available on the objective is collected to determine what could be the weak points and gaps in the security system of computer networks
Phase 2: second analysis
in this phase, through the use of the information obtained, possible problems are put to the test. In this phase the vulnerabilities are tested to understand if they are actual problems as previously assumed.
Given the incredible speed at which computer technologies and techniques evolve, it is possible that a system will prove secure this month, but instead have some problems to solve the following month. For this reason, it is advisable to repeat the security checks on company computer networks regularly and frequently.
Results
At the end of the process of verifying the vulnerabilities of a system, the final reports contain all the results collected. Typically these enclose all relevant information, including:
the list of vulnerabilities found
an in-depth description of the vulnerabilities
countermeasures to be adopted to reduce risks
Verification of vulnerabilities is a fundamental procedure for the company, but it does not guarantee the security of computer networks. For the correct maintenance of the security of your systems, it is also essential to use another tool: the Penetration Test.
Penetration test
The Pentest, or penetration test, is aimed at verifying how the vulnerabilities of a system can be exploited to gain access and move within it. One of the initial steps performed by a pentester is scanning the network to find IP addresses, device type, operating systems and possible system vulnerabilities. But unlike the Vulnerability Assessment, the Pentest doesn’t stop there.
Of crucial importance for a tester is the exploit of identified vulnerabilities in order to gain control of the network or to take possession of sensitive data. The tester uses configurable automated tools to perform exploits against computer network systems. The peculiar part, however, occurs when the tester performs manual exploit attempts, just like a hacker would.
Classification
Penetration tests are classified in two ways: gray box or black box.
Gray box tests are performed with full knowledge of the target company’s IT department. Information is shared with the tester, such as network diagrams, IP addresses, and system configurations. The approach of this method is the verification of the safety of the present technology.
A black box test, on the other hand, represents more properly the action of a hacker who tries to gain unauthorized access to a system. The IT department knows nothing about the test being performed and the tester is not provided with information about the target environment. The black box method evaluates both the underlying technology and the people and processes involved to identify and block an attack as it would happen in the real world.
Phases of the Pentest
Phase 1: Analysis
The system is analyzed, studying its strengths and weaknesses. All preliminary information is collected. This, of course, does not happen if it is a gray box pentest.
Phase 2: Scan
The entire infrastructure is scanned to find the weak points to focus on.
Phase 3: Planning
Thanks to the information gathered, we plan with which tools and techniques to use to hit the system. The possibilities are many and they are both purely technological and social engineering techniques.
Phase 4: actual attack
In this phase the testers try to exploit the identified vulnerabilities to gain full control of the targeted system.
Report
At the end of the Penetration Test, a report is also compiled that details the entire process carried out and includes:
evaluation of the impact of a real attack on the company
solutions to solve problems and secure computer network systems
A Penetration Test that is not successful is a sign that the system under examination is safe * and the data inside it does not risk anything. However, this does not mean that the company will be protected forever from any attack: precisely because the strategies of hackers constantly evolve, it is important to carry out Penetration Tests regularly.
(*) It should be noted, however, that although a good Penetration Test follows guidelines or structuring methodologies (i.e. OWASP) it remains a test with a strong subjective impact of the Penetration Tester and of the team that performed it, therefore it cannot be excluded that by repeating the tests carried out by a different group of Penetration Tester we have no new results. Furthermore, as is well known to our readers, in the field of Cyber Security the concept of “safe” in absolute terms is inadequate.
How to do
Although Vulnerability Assessments and Penetration Tests have different objectives, both should be performed regularly to verify the overall security of the information system.
Vulnerability assessment should be done often to identify and fix known vulnerabilities. The Pentest should be carried out at least once a year and certainly after significant changes in the IT environment, to identify possible exploitable vulnerabilities that may allow unauthorized access to the system. Both of the services described in this article are available through SOD, even on a recursive basis to ensure test effectiveness. contact us to find out more.
[btnsx id=”2931″]
Useful links:
Security: pentest and verification of vulnerabilities
Vulnerability Assessment & Penetration Test
Customers
Twitter FEED
Recent activity
-
SecureOnlineDesktop
Estimated reading time: 6 minutes L'impatto crescente delle minacce informatiche, su sistemi operativi privati op… https://t.co/FimxTS4o9G
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The growing impact of cyber threats, on private or corporate operating systems… https://t.co/y6G6RYA9n1
-
SecureOnlineDesktop
Tempo di lettura stimato: 6 minuti Today we are talking about the CTI update of our services. Data security is… https://t.co/YAZkn7iFqa
-
SecureOnlineDesktop
Estimated reading time: 6 minutes Il tema della sicurezza delle informazioni è di grande attualità in questo peri… https://t.co/tfve5Kzr09
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The issue of information security is very topical in this historical period ch… https://t.co/TP8gvdRcrF
Newsletter
{subscription_form_1}© 2024 Cyberfero s.r.l. All Rights Reserved. Sede Legale: via Statuto 3 - 42121 Reggio Emilia (RE) – PEC [email protected] Cod. fiscale e P.IVA 03058120357 – R.E.A. 356650 Informativa Privacy - Certificazioni ISO