Estimated reading time: 6 minutes
An advanced persistent threat (APT) is a broad term used to describe an attack campaign in which an intruder, or a group of intruders, establishes an illicit and long-term presence on a network in order to extract highly sensitive data. The targets of these assaults, which are chosen and studied with great care, typically include large corporations or government networks. The consequences of such intrusions are vast, and include:
- Theft of intellectual property (for example, trade secrets or patents)
- Compromise of sensitive information (for example, private data of employees and users)
- Sabotage of critical organizational infrastructures (for example, deletion of databases)
- Total control takeover of the site
Executing an APT assault requires more resources than a standard attack on web applications. The perpetrators are usually teams of experienced cybercriminals who have substantial financial backing. Some APT attacks are government-funded and used as weapons of cyber warfare.
Common attacks, such as Remote File Inclusion (RFI), SQL injection, and cross-site scripting (XSS), are frequently used by the perpetrators to establish a foothold in a targeted network. Then, Trojans and backdoor shells are often employed to expand that foothold and create a persistent presence within the perimeter.

Progression of Advanced Persistent Threats
A successful APT attack can be divided into three phases: 1) network infiltration, 2) expansion of the attacker’s presence, and 3) extraction of the accumulated data, all without being detected.
- Network Infiltration
As mentioned, every advanced persistent threat begins with an infiltration. Companies are typically infiltrated through the compromise of one of the following areas: web resources, network resources, or authorized human users. This is achieved either through malicious uploads or social engineering attacks. All these are threats regularly faced by large organizations.
Infiltrators may also simultaneously carry out a DDoS attack against their target. This serves both as a smokescreen to distract the network staff and as a means to weaken a security perimeter, making it easier to breach.
Once initial access is gained, attackers quickly install a backdoor malware shell that secures access to the network and allows for stealthy remote operations. Backdoors may also manifest as Trojans disguised as legitimate software.
- Expansion of Presence
After the foothold is established, attackers move to expand their presence within the network and thereby “create” the true advanced persistent threat.
This involves moving up the hierarchy of an organization, compromising staff members with access to the most sensitive data. By doing so, attackers are able to gather critical business information, including product line information, employee data, and financial records.
Depending on the ultimate goal of the attack, the accumulated data might be sold to a competing enterprise, altered to sabotage a company’s product line, or used to take down an entire organization. If sabotage is the motive, this phase is used to subtly gain control of more critical functions and manipulate them in a specific sequence to cause maximum damage.
For instance, attackers might delete entire databases within a company and then disrupt network communications to prolong the recovery process.
- Data Extraction
While an APT event is ongoing, the stolen information is typically stored in a secure location within the compromised network. Once enough data has been collected, the thieves must extract it without being detected.
Typically, white noise tactics are used to distract the security team so that the information can be moved out. This might take the form of a DDoS attack, again tying up network personnel and/or weakening the site’s defenses to facilitate extraction.

Security Measures Against Advanced Persistent Threats
Proper detection and protection against APTs require a multifaceted approach from network administrators, security providers, and individual users.
Traffic Monitoring
Monitoring incoming and outgoing traffic is considered best practice to prevent the installation of backdoors and block the extraction of stolen data. Inspecting traffic within the corporate network perimeter can also help alert security personnel to any unusual behavior that may indicate malicious activity.
A web application firewall (WAF) deployed at the network edge filters traffic to web servers, thus protecting one of your most vulnerable attack surfaces. Among other functions, a WAF can help eliminate application-level attacks, such as RFI and SQL injection attacks, commonly used during the APT infiltration phase.
Traffic monitoring services for internal traffic, such as network firewalls, are the other side of this equation. They can provide a granular view that shows how users are interacting within your network, while helping to identify internal traffic anomalies (e.g., irregular logins or unusually large data transfers). The latter could indicate an ongoing APT attack. It is also possible to monitor access to file shares or system honeypots.
Lastly, incoming traffic monitoring services might be useful for detecting and removing backdoor shells. For comprehensive monitoring services, adopting the SOCaaS from SOD might be right for you.

Additional Measures Against Advanced Persistent Threats
In addition to the best practices already mentioned for preventing an advanced persistent threat on the corporate network, it is wise to take action on multiple fronts. In numerous other articles, we have discussed how beneficial it is for the security team to have a single place to monitor every point of the network. An excellent tool for this purpose is a SOC.
Our SOCaaS offers all the functionalities of a Security Operations Center without the burden of investing in equipment and specialized personnel. Moreover, thanks to UEBA technology, not only is our SOC able to retrieve and systematically store logs, but it is also actively involved in identifying suspicious user behavior.
These features are great for increasing the responsiveness of the security team and averting even attempts of advanced persistent threats against the corporate network.
To learn how we can help your company enhance its security, do not hesitate to contact us; we will be pleased to answer any questions.
Useful links:
Link utili:

Estimated reading time: 5 minutes
Just like any other IT field, the cybersecurity market is driven by hype . Currently hype towards XDR, ie eXtended Detection and Response .
XDR is the latest in threat detection and response, a key element of a company’s infrastructure and data defense .
What exactly is XDR?
XDR is an alternative to traditional responsive approaches that only provide layer visibility on attacks . I refer to procedures such as detection and endpoint response (EDR), network traffic analysis (NTA) and SIEM , which we have talked about in many other articles.
The layer visibility implies that various services are adopted, stratified (layers), which each keep under control a specific entity in the infrastructure. This can be problematic. In fact, you need to make sure that layers don’t end up isolated, making it difficult, or nearly impossible to manage and view data. layer visibility provides important information, but can also lead to problems, including :
Collecting too many incomplete and contextless alerts. EDR detects only 26% of initial attack vectors and due to the high volume of security alerts, 54% of professionals security ignores warnings that should be investigated .
Complex and time-consuming investigations requiring specialist expertise . With EDR, the median time to identify a breach has increased to 197 days, and the median time to contain a breach has increased to 69 days.
Tools focused on technology rather than user or business . EDR focuses on technology gaps rather than the operational needs of users and companies. With more than 40 tools used in an average Security Operations Center (SOC), 23% of security teams spend their time maintaining and managing security tools rather than investigating . ( Source )
For already overloaded security teams, the result can be an endless stream of events , too many tools and information to switch between, longer time frames for detection and security expenses that are beyond budget and are not even fully effective .
What’s new in eXtended Detection Response
XDR implements a proactive approach to threat detection and response . It offers visibility into data across networks, clouds and endpoints, while applying analytics and automation to address today’s increasingly sophisticated threats. The benefits of the XDR approach for security teams are manifold:
Identify hidden, stealth and sophisticated threats proactively and quickly.
Track threats across any source or location within your organization. < br> Increase the productivity of people working with technology.
Get more from their security investments .
Conclude investigations in a way more efficient .
From a business perspective, XDR enables companies to detect cyber threats and stop attacks, as well as simplify and strengthen security processes. As a result, it enables companies to better serve users and accelerate digital transformation initiatives. When users, data and applications are protected, companies can focus on strategic priorities.
Why consider it for your company
The two main reasons why this approach is beneficial are: endpoints do not have visibility into threats in places like cloud services , and it may not be possible to put a < em> software agent on all company endpoints .
But there are other reasons to consider too. The addition of other data sources can provide more context in the EDR results, improving triage and investigation of alerts . Providers are moving not only to provide more and better organized data, but also by delivering analytics platforms to lighten the analytical load on operators. This translates into ease of use and reduced operating costs.
XDR can seem very attractive as a product: Tight integration of parts, highly tuned content (as the provider has total control over the events from the data sources), use of analytics and response automation.

What to pay attention to before adoption
Some providers are positioning their XDR as the ultimate threat detection solution . However, many vendors are unable to offer all the tools needed to get the advantage sold. Some providers offer endpoint and cloud monitoring in the package, others endpoint and network monitoring, but when looking at the comprehensive needs of most organizations, there are often missing details in the overall picture.
And if, once the company engages with a provider and notices a lack in one of the monitored sectors, what are the possible solutions? A situation of vendor lock-in from which to break free means to sever a contract and then open another one, with all the consequent costs.
XDR as an approach, not as a product
Before entering into a contract with a provider that sells a solution as final, it is always good to weigh the benefits and implications analytically.
Tight, two-way integration of multiple threat detection and response capabilities is the first distinguishing feature. But it is not necessary to buy two technology components from the same vendor to achieve good integration. Indeed, many products have the ability to integrate with some solutions from other vendors as one of their main strengths.
The XDR approach must provide a platform that allows the necessary data collection and storage , but also strong analytical skills, to orchestrate and automate response actions provided by the other parts of the solution. A cloud based Next Generation SIEM is a perfect solution.
How to move then?
The interest in XDR products is a clear signal that excessive fragmentation was leading to excessive complexity. A little consolidation is good, but it must be done while protecting flexibility and the ability to follow the best solutions.
In our opinion, a SOCaaS is an optimal solution. Provides next generation SIEM , with strong analytical capabilities. In addition, it also integrates artificial intelligence that helps in time to recognize threats through behavior analysis. A SOCaaS is the future of security operating platforms.
To find out with our services they can help you protect the data of your company and your customers, contact us, we will gladly answer all your questions.
Useful links:

Estimated reading time: 6 minutes
I dati di threat intelligence forniscono alle aziende approfondimenti rilevanti e tempestivi necessari per comprendere, prevedere, rilevare e rispondere alle minacce alla sicurezza informatica. Le soluzioni di intelligence sulle minacce raccolgono, filtrano e analizzano grandi volumi di dati grezzi relativi a fonti esistenti o emergenti di minacce. Il risultato sono feed di threat intelligence e rapporti di gestione. I data scientist e i team di sicurezza utilizzano questi feed e report per sviluppare un programma con risposte mirate agli incidenti per attacchi specifici.
Tutti, dalla prevenzione delle frodi alle operazioni di sicurezza all’analisi dei rischi, traggono vantaggio dalla threat intelligence. Il software di intelligence sulle minacce fornisce visualizzazioni interattive e in tempo reale dei dati relativi alle minacce e alle vulnerabilità.
Il vantaggio offerto agli analisti ed esperti di sicurezza è evidente e serve a identificare facilmente e rapidamente i modelli degli attori delle minacce. Comprendere la fonte e l’obiettivo degli attacchi aiuta i capi d’azienda a mettere in atto difese efficaci per mitigare i rischi e proteggersi dalle attività che potrebbero avere un impatto negativo sull’azienda.
La cyber threat intelligence può essere classificata come strategica, tattica oppure operativa. Quella Strategica riguarda le capacità e gli intenti generali degli attacchi informatici. Di conseguenza anche lo sviluppo di strategie informate associate alla lotta contro le minacce a lungo termine. Quella Tattica riguarda le tecniche e le procedure che gli aggressori potrebbero utilizzare nelle operazioni quotidiane. Infine, la threat intelligence Operativa, fornisce informazioni altamente tecniche a livello forense riguardanti una specifica campagna di attacco.

Il ciclo della threat intelligence
Le soluzioni di intelligence sulle minacce raccolgono dati grezzi sugli attori e le minacce da varie fonti. Questi dati vengono poi analizzati e filtrati per produrre feed e rapporti di gestione che contengono informazioni che possono essere utilizzate in soluzioni automatizzate di controllo della sicurezza. Lo scopo principale di questo tipo di sicurezza è quello di mantenere le organizzazioni informate sui rischi delle minacce persistenti avanzate, delle minacce zero-day e degli exploit, e su come proteggersi da esse.
Il ciclo di intelligence delle minacce informatiche consiste nelle seguenti fasi.
Pianificazione: I requisiti dei dati devono essere prima definiti.
Raccolta: Si raccolgono grandi quantità di dati grezzi da fonti interne ed esterne di threat intelligence.
Elaborazione: I dati grezzi sono filtrati, categorizzati e organizzati.
Analisi: Questo processo trasforma i dati grezzi in flussi di informazioni sulle minacce con l’uso di tecniche analitiche strutturate in tempo reale e aiuta gli analisti a individuare gli indicatori di compromissione (IOC).
Diffusione: I risultati dell’analisi vengono immediatamente condivisi con i professionisti della sicurezza informatica e gli analisti di threat intelligence.
Feedback: Se tutte le domande trovano risposta, il ciclo si conclude. Se ci sono nuovi requisiti, il ciclo ricomincia dalla fase di pianificazione.
Indicatori comuni di compromissione
Le aziende sono sempre più sotto pressione per gestire le vulnerabilità della sicurezza e il panorama delle minacce è in continua evoluzione. I feed di threat intelligence possono aiutare in questo processo identificando gli indicatori comuni di compromissione (IOC). Non solo, possono anche raccomandare i passi necessari per prevenire attacchi e infezioni. Alcuni degli indicatori di compromissione più comuni includono:
Indirizzi IP, URL e nomi di dominio: Un esempio potrebbe essere un malware che prende di mira un host interno che sta comunicando con un noto attore di minacce.
Indirizzi e-mail, oggetto delle e-mail, link e allegati: Un esempio potrebbe essere un tentativo di phishing che si basa su un utente ignaro che clicca su un link o un allegato e avvia un comando dannoso.
Chiavi di registro, nomi di file e hash di file e DLL: Un esempio potrebbe essere un attacco da un host esterno che è già stato segnalato per un comportamento nefasto o che è già infetto.

Quali strumenti per la threat intelligence
Il crescente aumento del malware e delle minacce informatiche ha portato a un’abbondanza di strumenti di threat intelligence che forniscono preziose informazioni per proteggere le aziende.
Questi strumenti si presentano sotto forma di piattaforme sia open source che proprietarie. Queste forniscono una serie di capacità di difesa contro le minacce informatiche, come l’analisi automatizzata dei rischi, la raccolta di dati privati, strumenti di ricerca rapida di threat intelligence, la segnalazione e condivisione di queste informazioni tra più utenti, avvisi curati, analisi dei rischi di vulnerabilità, monitoraggio del dark web, mitigazione automatizzata dei rischi, threat hunting e molto altro.
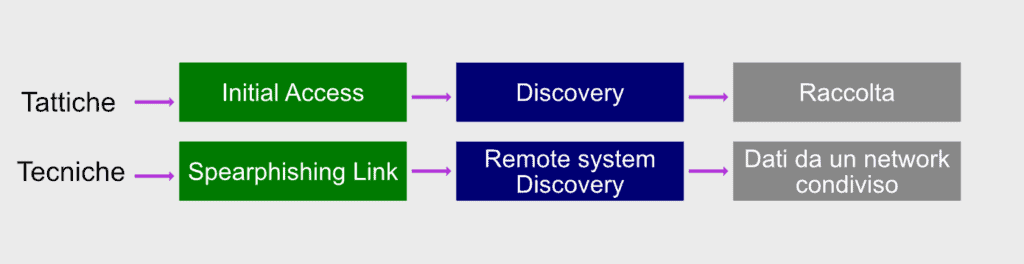
Abbiamo parlato di uno di questi strumenti in un altro articolo: il Mitre Att&ck. Questo è uno strumento molto utile per conoscere i comportamenti e le tecniche di attacco hacker. Questo grazie alle informazioni raccolte dalla threat intelligence e la conseguente condivisione. Un framework come questo è molto efficiente per creare meccanismi difensivi che consentono di mettere in sicurezza le infrastrutture aziendali.
Intelligenza artificiale e informazioni sulle minacce
Come abbiamo visto prima, la raccolta di informazioni da varie fonti non è altro che una delle fasi. Queste devono poi venire analizzate e successivamente elaborate in protocolli di controllo, per essere davvero utili per la sicurezza.
Per questo tipo di lavori di analisi, definizione di comportamenti baseline e controllo dei dati ci si affida sempre di più all’intelligenza artificiale e al deep learning. Un Next Generation SIEM, affiancato a una soluzione UEBA sono perfetti per questo tipo di protezione.
Il controllo del comportamento delle entità all’interno del perimetro effettuato dal UEBA è in grado di identificare ogni comportamento sospetto, in base alle informazioni raccolte e analizzate dal SIEM.
Conclusioni
Gli strumenti di difesa che abbiamo nominato sono il valore primario di un piano di sicurezza aziendale. Adottare soluzioni specifiche, implementare la threat intelligence e quindi una ricerca attiva degli indicatori di minacce, offre una posizione di vantaggio strategica. L’azienda può operare un passo avanti ai criminali, i quali possono far leva solo sull’effetto sorpresa contro le loro vittime. Proprio per questa situazione generale, ogni azienda dovrebbe essere nelle condizioni di non farsi cogliere alla sprovvista. Implementare soluzioni proattive è ormai necessario.
La threat intelligence è quindi un’arma da difesa dietro la quale mettere al riparo le risorse più importanti per poter lavorare in tranquillità.
Se vuoi sapere come possiamo aiutarti con i nostri servizi dedicati alla sicurezza, non esitare a contattarci, saremo lieti di rispondere a ogni domanda.
Useful links:
Cyber Threat Intelligence (CTI) – maggiore efficacia per la sicurezza IT
Progetti di Secure Online Desktop
Cos’è la Cyber Security? Definizione e proposte
Prevenire il shoulder surfing e il furto di credenziali aziendali

Estimated reading time: 13 minutes
Vishing is a particular type of phishing that uses VoIP (Voice over IP) technology to carry out attacks. Unlike traditional landline telephone services, with VoIP technology it is possible to carry out telephone conversations using the Internet connection.
Hackers often use VoIP in their vishing attacks because this allows them to spoof their caller ID with great ease. Posing as an employee of a legitimate entity, such as a bank, the police or a well-known company, Hackers try to obtain personal and financial information of their victims.
With the information obtained it is possible to access a bank account and empty it. Furthermore, it is possible to commit fraud, scams and other crimes using the identity of the victim. Identity theft is a crime that has been on the rise in recent years, which is another reason to inform yourself and stay alert.
Vishing: how to recognize the attack
Vishing attacks usually use automatic text-to-speech systems to redirect the victim to a telephone number controlled by the hacker, but this does not exclude the possibility that a hacker could engage in a real conversation with his victim. The information most commonly targeted by vishing attacks is bank account data. However, many times, hackers also try to obtain access credentials to well-known services such as Microsoft, Apple or Google.
Using social engineering, hackers carrying out vishing attacks trick their victims into extorting money. Generally, scammers attempt to create a sense of urgency or try to alter the emotional state of their victims. This is to force you to pay quickly and without thinking deeply about what is happening.

Vishing: common attack patterns
Vishing attacks can be different from each other, although they always have common goals. A scammer who uses this type of attack could disguise his Caller ID by pretending to be an authoritative person or any known person. They may also leave pre-recorded messages containing threats in their victims’ email inboxes. Not just emails, hackers could also exploit SMS to carry out their scams, as in cases of smishing.
Scammers usually approach their victims by posing as people of authority or exploit the victim’s personal relationships. Below you will find a list of the most commonly adopted scam schemes.
Most common Vishing attacks
Debt collection agency scam
The scammer pretends to be an official of a debt collection agency. The scammer threatens legal consequences or even arrest if the victim does not pay his debts, even if the victim actually has no debt.
Romance scams
the hacker pretends to be a love interest for his victim who he meets on a dating app or site. He or she may sometimes pose as an old flame from the past who urgently needs money for some family or medical reason.
Tech support scam
The scammer poses as a tech support employee and claims there is a serious technical problem on the victim’s computer. The scammer, in this case, uses fear and a sense of urgency to gain remote control of the victim’s computer. It will then install malware passing it off as diagnostic software. Once you gain remote control of your computer, you can access files or any personal information stored on your computer.
There are real companies that live with this type of “business” in Asian countries. Furthermore, there are known creators and white-hat hackers on YouTube who intercept these scammers and try to carry out reverse (social) engineering to trap these criminals. Some of these creators have achieved remarkable results, causing some of these scammer companies to shut down.

Business and investment scams
Scammers pose as financial experts and convince victims to pay sums of money for investments. Scams centered on cryptocurrencies have been spreading a lot lately, driven by the utopia of making a lot of money in a short time.
Charity scams
Scammers pose as members of charities to convince victims to donate to their cause. These fake organizations don’t actually do any charitable work and the money donated goes directly to the scammers. It is very common for them to use photos of children or people suffering from illnesses to appeal to the human sense of compassion.
Insurance scams
Using the information they have on the cars registered to their victims, they try to offer them advantageous insurance offers. With this strategy it is possible not only to collect other personal information on one’s victims, but also to defraud them financially if the victim decides to purchase the policy proposed by the hacker.
How is it possible to defend yourself from vishing
It is often difficult for victims to recognize vishing attempts because it is not unusual for banks and other entities and organizations to request sensitive information by telephone. Vishing attacks are increasingly sophisticated and can include pre-recorded messages and other ways to increase credibility.
We at SOD suggest several ways to detect vishing attempts, below are some strategies to adopt to recognize this type of attack. The best defense against these frauds, as in the case of phishing, is to know how to identify them immediately and not to spread any personal information by telephone, especially if the request is unexpected.
You should always be careful when using poorly traceable forms of payment such as cash, gift cards and prepaid cards. Additionally, you should pay particular attention to the characteristics of the phone call, such as the tone or accent of the person making the call or the urgency of the call. These can be alarm bells that signal the possible presence of a case of vishing.
To avoid falling victim to vishing, it is advisable to never answer calls from unknown numbers. Another useful tip is to never comply with requests from a suspicious person, such as pressing buttons when asked or answering suspicious questions.
If you are not sure about a number from which calls are received, you can always do an internet search and see if the number belongs to a service we use that is perhaps contacting us with a real problem.
In many countries, social media is used to communicate with the public. Many platforms use protection systems to verify the actual authenticity of government and banking profiles, therefore you should never trust an entity without these badges.

Conclusions
The types and mechanisms of intrusion are increasingly sophisticated. Phishing, smishing and vishing attempts are now a constant in our lives, continually putting our personal data at risk. As we have seen in many situations, data is the most valuable commodity on the internet, so protecting it must be a priority!
To concretely defend ourselves, the use of professional tools is the only safe path to take. Our SOCaaS service protects against vishing but is also a complete tool that guarantees corporate security, identifying and blocking all kinds of threats.
Additionally, SOD also organizes ethical attack campaigns to test the resilience of a company’s employees. After the attacks, the data collected is used to organize training sessions geared towards the specific characteristics of the company and the resilience shown by employees.
For information on the ethical phishing services we offer or to better understand how SOCaaS could be an ideal solution for your company, do not hesitate to contact us by pressing the button below.
Useful links:

Presentare il servizio SOCaaS[EDR] di sicurezza gestito, offerto dalla Secure Online Desktop per l’identificazione, la gestione e la risposta ai Cyber Threat.
DESTINATARI
Coloro che in azienda si occupando di Cyber Security come: CISO, CSO e IT Manager.
PROGRAMMA
Di seguito il programma dell’evento:
- – Presentazione Secure Online Desktop
- – SOCaaS cosa è, a cosa serve, a chi è rivolto
- – Cynet – Who we are
- – Cynet – What do you need?
- – Cynet XDR platform
- – XDR Mobile
- – CyOps
- – How to weight the real world?
- – Cynet – MITRE framework
- – Cynet – Portfolio
- – Demo
- – Q&A
RELATORI
- – Nicolas Corona – Responsabile commerciale di Secure Online Desktop
- – Marco Lucchina – Channel Manager Italy, Spain & Portugal
DURATA
90 minuti
SPONSOR/PARTNERS
REGISTRAZIONE
Registrati gratuitamente qui: https://meet.zoho.eu/uMQfd1dvoA

Estimated reading time: 6 minutes
The growing impact of cyber threats, on private or corporate operating systems, leads more and more users to use third-party applications to protect work information. Fortunately, the implementation of new technologies improves this condition. Among the most interesting solutions, aimed at protecting corporate systems, is the SOAR technology with its benefits. What are the potential and the advantages that a company can derive from this system?

SOAR: what is it?
Before analyzing the concrete benefits that SOAR technology can guarantee, it is essential to understand what it is and what it means.
With SOAR, acronym for Security Orchestration, Automation and Response , we identify a tool capable of supporting IT security staff. SOAR model technologies allow for a triple approach : vulnerability and risk management, incident response and ultimately the automation of security operations . In their English terminology respectively: Threat and Vulnerability Management, Incident Response and Security Operations Automation .
The functioning of the SOAR-systems
Through the use of artificial intelligence and machine learning algorithms, a system with SOAR implementation is capable of correlating three sectors usually distant from each other. Specifically, a SOAR technology combines: SAO, TIP and SIRP . Respectively Security Orchestration and Automation , Threat Intelligence platform and Security Incident Response Platform .
These platforms are designed to store data and information on the behavior of viruses, hacker attacks, malware and other potential cyber threats. Companies using a SOAR system are much safer, as they can benefit from a multipurpose system, which not only aims to cure the threat, but also its potential emergence .
Difference between orchestration and automation
SOAR technology combines both automation and orchestration systems for cybersecurity, but what’s the difference? When using a system based on orchestration activities, you have an approach in which different security tools and systems are connected to optimize processes .
In the case of a system aimed at automation, we refer to the ability to automate the operations of corporate environments. Automation is based on activities, while orchestration is based on processes. By exploiting SOAR technology, it is possible to obtain the orchestration of processes for the execution of automated activities .
The benefits of SOAR
In order to have a more concrete idea of the applications of a SOAR technology and the consequent benefits, it is essential to examine its advantages in detail.
Incorporate automation and orchestration features
Using features related to machine learning and artificial intelligence, a SOAR system significantly increases corporate cybersecurity. The processes and activities examined by the automation and orchestration systems ensure the company is responsive to cyber threats without generating post-attack tickets. An example is the implementation of SIEM and UEBA in the security orchestration.
Usually a traditional system generates an alert, then the IT technicians provide for the manual resolution of the problem. With an automated system, is the software itself that detects, solves, and archives the problem. This benefit should not be underestimated if there are no IT technicians within the company context.
Centralization of threats
A standard computer system hardly has a centralized view of threats. This condition forces the system itself to intervene in a marked way after it has been compromised. Unfortunately, canonical systems have different levels of security, where everyone intervenes in specific alert conditions.
Larger companies divide the detection of threats according to the reference area, be this NOC, IT or DevOPS, this greatly limits the cybersecurity of the system.
Thanks to its automation and orchestration capabilities, SOAR technology combines the entire threat centralization phase, ensuring maximum protection even in different contexts.
Time optimization
One of the most significant benefits of using SOAR technology is time savings. When you suffer a cyber attack, be it minor or major, it requires the intervention of IT technicians. In the time lapse between the alert sent by the company and the resolution of the problem, the work activity must stop.
Thanks to a dedicated software, with SOAR implementation, it is possible to optimize the intervention times and in many cases eliminate them completely.
Playbook
Getting a playbook in as much detail as possible is essential to understanding the attacks. A SOAR system, in a completely intuitive way, allows you to chain several playbooks to face complex actions.
For example, in the event that there is an alert combined with a specific tracking system, capable of isolating the traffic of a specific suspicious IP address; the SOAR software at that time will analyze the information useful to identify the IP addresses and evaluate if there are compromised accounts.
Optimal integration with the infrastructure
One benefit that has made SOAR technology particularly useful is its integration capability. SOAR software can integrate seamlessly into any corporate infrastructure , collecting information and providing IT security in an automated way, even on non-modern systems.
Team efficiency
Minimizing interactions with the company system, for solving IT problems, allows the company to optimize working times. All the time lost for solving the technical problem can be recovered and used for other more useful work activities .
Even less skilled IT operations teams can use hardware and software without fear of threats. One of the most relevant issues in business contexts is the inefficiency of IT technicians to recognize cyber threats.
The presence of phishing in e-mail or the exchange of files between one area and another leads in many cases to cyber attacks. With a SOAR system, you can minimize these issues by helping IT assistants to focus only on their work.
Annual cost
An advantage not to be overlooked is the cost of continuous interventions for the resolution of cyber attacks. IT technicians who have to intervene after an alert produced by the system have a cost, the latter being significant if prolonged over time. SOAR technology from this point of view protects companies that do not want to spend more money on periodic interventions.

Secure Online Desktop: smart and fast solution
The potential of a SOAR system is evident, but it is important to rely on a quality service to obtain the maximum yield. We at SOD have been committed to providing IT security solutions for years .
The SOCaaS service with dedicated SOAR allows you to implement in your company software capable of automating and orchestrating in the way activities and work processes as best as possible.
This condition is particularly useful for companies that need to protect their corporate IT infrastructure. The ease of use and the enormous benefits make SOAR technology indispensable for those who want to reduce the costs of IT interventions and at the same time improve IT security.
If you have any questions about how our services can be useful for your business, do not hesitate to contact us, we will be happy to answer.
Useful links:

Estimated reading time: 6 minutes
The issue of information security is very topical in this historical period characterized by digitization. To protect themselves, businesses and individuals can use a variety of tools that can prevent an attack, but also help manage it. In this article we talk about Automated Response Integration and the automations in the SOCaaS offered by SOD .
Although the systems used are almost always based on efficient technologies, in recent years the implementation of SOCaaS services equipped with SNYPR for the analysis of Big Data is making a difference. The dedicated SOCaaS services facilitate end users in the use of security systems, basing their operation on automatic processes that protect company devices.

What is Automated Response Integration
The term Automated Response Integration identifies a specific approach to data analysis and consequent response in a cyber defense scenario. We see it today, in particular, related to our SOCaaS on which the SNYPR tool is applied, which we have already talked about in the past.
SNYPR and Automated Response Integration
In order to understand the potential of a SOCaaS service, with the implementation of SNYPR, it is appropriate to understand first what is meant by this term. When the word SNYPR is used, it identifies that examination tool capable of analyzing Big Data and simplifying its actions . A system equipped with SNYPR can examine a huge amount of data and identify the behaviors of everyone who interacts with the platform.
There is the combination of SIEM and UEBA logs, as well as an analysis dedicated to security in real time, very useful for automating the daily operations carried out in the infrastructure.
The operation of a SNYPR tool for corporate IT is based on the analysis of thousands of information collected, thanks to artificial intelligence. These analyzes are then used to prevent and intervene on cyber threats. The fact that most of these operations are automatic brings us to the field of Automated Response Integration.
Technically it differs from other platforms in the use of threat detection algorithms that have the ability to scan systems and logins performed by other devices in real time . A traditional system simply collects data, while a SOCaaS with SNYPR implementation can also detect much more harmful threats and adapt accordingly.
The strengths of Automated Response Integration with SNYPR / SOCaaS
One of the strengths of this tool is its Security Data Lake (SDL) based security system. This condition allows companies to keep a copy of the data in the SDL and submit the scan request at any time. There is no data lock, as in traditional systems, but an open system capable of sharing information with the different devices.
As it is easy to guess, it is precisely this availability of data and the possibility of in-depth analysis, which allows us to implement an Automated Response Integration strategy with our SOCaaS.
There are various system functions in the field that are noteworthy. These include: data enrichment, distributed behavioral analysis, historical investigation, scalability and data redundancy.
This coordination of services allows to have a concrete impact for IT security , a condition evident in three areas of SNYPR competence: internal threats, persistent threats and professional use.
The professional use of SNYPR: in recent years, the most important companies have equipped themselves with a SNYPR platform to protect their data storage and analysis infrastructures. The system constantly monitors the flow of information and adapts to the best conditions in the event of cyber attacks.
Automated Response Integration for automation in SOCaaS
From a technical point of view, a SNYPR system itself guarantees excellent potential, but it is with the SOCaaS implementation that it finds its maximum protection expression in IT systems.
The analysis of threats in a company system, although it is carried out in real time, requires the intervention of specialized technicians to identify the problem. With SOCaaS, identification is linked to automated actions to deal with possible threats, without the need for third-party intervention.
There is a real integration with automated response useful to prevent and eradicate possible threats . This process is essential not only to prevent business systems from being compromised, but also to protect companies and their IT departments, which can focus on other tasks.
Automated Response Integration functionality
Playbook: the tool can launch a playbook when SNYPR threats are detected. The transcript of the events is important to understand the origin of the threat.
Query: automation can manage actions or queries on end points directly from SNYPR, in order to face the cyber attack. This feature avoids the blocking of production in the most excited moments.
UEBA: As mentioned in the previous lines, an NSYPR-based tool can import UEBA alerts. The reference formats are usually CEF, which report warnings from any type of device, significantly affecting safety.
IP control : one of the strengths of this technology is the control of domains, IPs, files and URLs, ensuring maximum versatility for any type of work activity.
DNS and Whols data : The automated response is particularly useful in storing DNS and Whols data, as it is possible to check the validity of certificates and monitor unwanted access.
Vulnerability: You can schedule a network vulnerability scan. This analysis process is especially suitable for companies that send and receive a large flow of information outside the company context.

Relying on professionals
Not all SOCaaS-based services that implement SNYPR are identical to each other, some of them offer the same technology but different intervention methods. Among the most interesting solutions is our SOCaaS. For years we have been dealing with offering IT security solutions internationally and this is a guarantee of excellence, alongside our certifications and partnerships.
Our IT security service, based on Automated Response Integration, guarantees complete monitoring of corporate infrastructures, helping the company to avoid additional costs for ordinary or extraordinary maintenance of the devices.
Conclusions
The implementation of SOCaaS automated systems is now essential for companies that want to protect themselves from IT docking. Real-time analysis and notification of potential threats ensure essential peace of mind in an age increasingly exposed to digital dangers.
To find out how SOD and its services can help your company, do not hesitate to contact us, we will be happy to answer any questions.
Useful links:

Estimated reading time: 4 minutes
When we refer to artificial intelligence, we often refer to the great technologies that could control the world, with an obvious streak of science fiction. The reality is very different and is characterized by a technology with great potential, which is able to ensure countless advantages . Today we talk about how artificial intelligence can be implemented in monitoring.
The use of these technologies is unavoidably transversal to many sectors of the economy, but it is also usable in some aspects of everyday life. Some examples range from washing machines that, weighing the load of laundry, are able to choose the most advantageous washing program, to voice assistants that simplify our everyday life.
Very important in the corporate sector are the monitoring systems which were created precisely from these technologies which we will talk more about in a moment.
Thanks to the optimization of the computing capacity operated by artificial intelligence, it is possible to increase the efficiency of company equipment. Let’s see how.

What is artificial intelligence and how can it innovate monitoring ?
Today, artificial intelligence is declined in many ways. Perhaps the most important is processing a large amount of data then providing answers to complex questions. At the base of artificial intelligence there is the study of algorithms that deal with performing complex mathematical operations.
Artificial intelligence is a very useful tool within a company, as it is able to carry out very sophisticated and precise processing. These operations are capable of significantly improving the operations and productivity of numerous departments of the company itself.
Applied to monitoring, for example, artificial intelligence is capable of analyzing the logs coming from the network, both in terms of performance and behavior. The big step forward in the analysis and monitoring of an infrastructure consists precisely in recognizing whether certain behaviors that emerge from the logs are risky or not.
To achieve these results it is essential to have all those features that are available through artificial intelligence .
What are the advantages of using artificial intelligence for monitoring?
Artificial intelligence is able to provide companies that choose to use it countless advantages. Not only in terms of improving the performance of information systems, but also to make more efficient and improve the security of the same, preventing attacks.
This happens thanks to the analysis of the logs both from a technical and a behavioral point of view. Technical analysis highlights any ongoing problems, while behavioral analysis can prevent or immediately identify suspicious actions.
How can our monitoring system improve business efficiency?
Our monitoring system is able to improve business efficiency through numerous technical analyzes in able to be implemented not only on the entire system, but also on individual units.
The ability to analyze data in depth also allows you to improve the management of the entire IT structure and prevent overloads or attacks. Overall, the efficiency and safety of the infrastructure are increased at the same time through artificial intelligence applied to monitoring.
But there’s more: these analysis and monitoring systems are able to integrate with extreme effectiveness in complex architectures. By being able to analyze large amounts of data and being able to deduce behaviors and actions from these, efficiency in security is ensured.
Another advantage is the fact that this monitoring system does not require specific hardware. Software agents are installed on the systems to be controlled which have the sole task of sending data in the form of a log to the control system. analyses.
These systems therefore prove to be the ideal solution to keep large and small IT architectures under control, with the aim of improving efficiency and increasing overall security. In short, an application really interesting and useful of artificial intelligence in monitoring.

What are the fields of application of this technology?
We apply artificial intelligence systems to monitoring, benefiting our customers enormously. First we can collect large amounts of data, enrich it automatically and finally analyze it. The analyzes are carried out both from a technical and a behavioral point of view.
The result is a dedicated system, our SOCaaS, which makes risk mitigation extremely efficient, particularly quick intervention in the event of an anomaly and also provides regular reports.
This service is able to bring together all the features listed in the article, and to offer it as a solution for companies that want a superior security system.
Better efficiency, safety, versatility, operability, are just some of the paradigms used to define the services we make available to our customers. Our main goal is to simplify and make your company’s IT security more efficient.
Do not hesitate to contact us if you want to know more, we will be happy to answer any questions.
Useful links:

Estimated reading time: 7 minutes
When we talk about log management we refer to a precise process which consists of the centralized collection of data that comes from different operating environments such as: devices, databases, applications and much more. Logs are produced by various system events , many of which are particularly important in the business environment.
So let’s see some important details regarding log management.

The importance of collection-in-log-management
The procedure for collecting log data is important to achieve various objectives at the company level. The main ones are: to verify the vulnerability; manage possible security problems; control access to data and applications; the monitoring in real time ; check for any malfunctions at the application level.
From a regulatory point of view, then, log management is very important at a company level as allows you to observe the most important principles concerning data protection . This is established by the “EU 95/46 / EC” directive. It is also required by the obligations established by the “ General Data Protection Regulation (RGPD or GDPR) “.
Hence, these features illustrate how important good log management is and how it can help companies prevent potentially invasive events before they occur.
This type of action corresponds to what, in jargon, is called “Privacy by Design”. According to this principle, it becomes necessary to execute the right strategies to avoid creating risks and problems related to violations.
The-problems-to-face-in-log-management
Log management needs the correct balance between the dynamic availability of resources and the growing number of log data . In addition, from the first step of acquiring the log data, it is appropriate to consider several elements. These often generate various complexities such as, for example: the quantity of sources to be taken into account; the number of data logs created; the multiplicity of events that give life to data log ; the types of data log ; the method of acquiring the data logs ; the compliance of the data log protection systems.
Log management needs the correct balance between the dynamic availability of resources and the growing number of log data . In addition, from the first step of acquiring the log data, it is appropriate to consider several elements. These often generate various complexities such as, for example: the quantity of sources to be taken into account; the number of data logs created; the multiplicity of events that give life to data log ; the types of data log ; the method of acquiring the data logs ; the compliance of the data log protection systems.
It is therefore advisable to plan the strategies that allow you to adopt the right solutions for your log management staff. In this way, technicians will be able to intervene while respecting the requirements already mentioned.
The characteristics of a log-management infrastructure
The infrastructure for log management is formed by the union of hardware, software and network elements that are set up so that they can communicate effectively with each other. The communications between these components are made within the same network that is used for the common activities of the company.
Nevertheless, for a company it is also important to take into account the possibility of collecting data using a different network so that any spyware attacks or other incidents will alter, intercept or delete the data.
If from the logistical and architectural point of view it is not possible, in a company, to carry out this second possibility, alternative measures should be adopted such as, for example, data encryption.
Summarizing, therefore, a log management infrastructure should ensure compliance with the following requirements: maintaining information that serves to achieve the collection objective following the principles of “minimization” and “proportionality” ; ensure that data remain unalterable throughout their life span; ensure the integrity of the data collected without making changes; keep the data for a limited period of time.
The data-aggregation at the company-level
As companies grow and reach large numbers of applications within their environment, data collection becomes an increasingly important and decisive challenge.
In addition, if we take into account the difficulty of collecting sufficient data logs to be able to remain compliant, respect for privacy standards and security issues that arise from modern threats, we easily realize how the collection becomes an increasingly complex challenge.
So, at the enterprise level, the key to creating an efficient collection system is the ability to dynamically capture data in real time from all available sources. Have a solution that allows you to put your data in a central location, such as a data lake , and facilitate filtering , transformation, classification, allows you to make the log management task easier for the company.
SOCaaS and the advanced log management system
A very advanced solution is the one offered by the SOCaaS , in particular by its component SIEM , which leverages the innovation of artificial intelligence. This allows you to analyze the data collected so as to find possible suspicious data.
In addition, a qualified technical intervention is always made available at any time of the day with precise and non-distracting tasks. The intervention allows you to verify the alarm notifications that are generated by the system so as to exclude false positives , intervening to eliminate the threat and give constant reports over time .
The ever increasing data collection and the analysis of artificial intelligence allow to make the service very convenient and complete.
The potential of the SOCaaS-system for companies
As we have just seen, it is very convenient for companies to rely on a SOC service (SOCaaS). The greatest potential is represented precisely by the innovation brought about by artificial intelligence that allows you to achieve maximum results regarding the constant and continuous analysis of data so that it has the certainty of identifying possible threats in a very short time . Thanks to this system, therefore, risks will be prevented and mitigated.
An added value, then, is not having to hire specialized technicians with specific skills in identifying and verifying threats. Those who rely on this service will also be able to receive reports on the situation and notifications in case of problems.
SOCaaS, therefore, allows you to take the right precautions against those still unknown techniques and has the ability to find the link between data concerning possible attacks with still unknown systems. This is thanks to the analysis of user behavior and infrastructure intities ( UEBA ).
In addition, the structure of the system is designed to bring about constant improvement. The synergistic work between technicians and artificial intelligence allows us to identify even unconventional breach attempts.
For companies it means improving their defenses by adapting them based on the data collected previously.
SOCaaS is perfect for those companies that want to work safely using network-based infrastructures. This is a guarantee of defense against cyber attacks .

The-advantages of choosing our SOCaaS for log-management
Choosing to rely on our SOCaaS has several benefits.
The first is to save money in both the short and long term. In fact, you will avoid buying dedicated hardware and specific software . Plus, you won’t even need to hire new employees or upgrade the skills of those who already work.
Another benefit is having the professional support of technicians who update every day to have the skills to fight new types of threats. This type of assistance is priceless and it is extremely difficult to obtain within the company staff. This is also due to the current shortage of professionals in the sector.
A further advantage is to have always updated technology available . You will not have to worry and worry about always updating the software, because these, solely responsible for the collection of data for SOCaaS, are always kept to the latest version.
Do you want to get more information to learn more about the SOCaaS functionality of SOD? Contact us to find out how we can help you keep your company’s defenses up.
Useful links:

Estimated reading time: 7 minutes
As we know, a ransomware is a malware that aims to extort money from victims . The means it uses is encryption to encrypt victim data, both local and in the cloud, and make it inaccessible.
The ransomware is therefore a real cyber blackmail : if the victim refuses to pay the requested sum, not only would he be denied access to his data, but there is also the risk that this data will be totally destroyed by hackers. There is no guarantee that unencrypted data will be returned to payment of the ransom.
The propensity or not to pay a ransom was analyzed by one 2020 study , in which it emerged that the 65% of respondents pay without hesitation. Furthermore, it appears that more than half of the sample paid when they were the victim of an attack. Cyber attacks also hit in Italy and 33% of Italians victim of ransomware stated that, despite having paid the ransom, the data in the possession of the victim have been totally or partially lost . In fact, there is no certainty that, by paying a sum of money, the decryption keys of the files will be delivered.

Ransomware: recent-news
In 2020 it was stated by Microsoft that Ransomware was a major threat . In fact, it is estimated that digital attacks of this type increased in 2020 compared to the previous year. This also happened in 2021.
Development of techniques
The development of ransomware techniques has been fairly straightforward. The first attacks weren’t as organized as the ones we see now. They were executed by single hackers and were often used to target small groups of people, if not a single user. Small sums of money were extorted from these victims, which over time increased more and more.
The use of Ransomware on a large scale dates back to the last few years: recently, in fact, they have evolved. Now the actors of these ransoms have changed, which are groups of organized cybercriminals .
It is no longer individual users that are being targeted, but large companies and their data . The decision to increase the range of ransomware was a novelty due to the fact that criminals and hackers agreed to press on the urgency of companies to recover high-importance data that cannot be lost and the greater possibility of companies to sell for more substantial redemptions .
Even the moment in which the attack occurs is no longer casual, but the result of a ruthless strategy. In fact, criminals choose holiday moments or moments when the company is weakest , moments in which it is easy for IT technicians to pay less attention to unauthorized access to databases.
Double-extortion-ransomware, one of the latest
Another novelty that has recently emerged about ransomware is the double extortion , a technique that ends up extorting a larger sum of money. This technique puts into practice a double ransom that leverages the victim’s weaknesses.
At first, blackmail is based on access to data, which is denied to the victims. When a first ransom is paid, several cybercriminal gangs ask for a second payment to prevent their data from being made public or released to competing companies .
In this way, companies not only have to pay the first ransom to regain access but will be asked for a second ransom to maintain the confidentiality of data that could still be in the hands of the criminal group.
The ransomware attacks of 2021
Ransomware attacks have skyrocketed and that’s nothing new. In recent years, this new modus operandi of double extortion has turned out to be much more profitable than simply deleting data, which however should not be ruled out as a possibility. Even if the ransom was paid, several companies said they no longer had access to the data.
In 2021, the year with the largest number of ransomware-type attacks ever recorded , there was a total loss of money of $ 6 trillion . The types of ransomware attacks have become increasingly sophisticated and designed to hit company databases at the heart and above all to evade their IT security systems, which unfortunately become obsolete very quickly.
There have been several massive attacks involving different types of companies.
Attack on the Colonial Pipeline Company
One of the most significant attacks was that of the hacker group DarkSide against the Colonial Pipeline Company, which took place in early May 2021 . The immediate damage caused by this attack was the interruption of the supply of fuel that was to arrive in the southern United States of America.
This attack was by far the heaviest of the year 2021, as the Colonial Pipeline is responsible for delivering more than half of the fuel in circulation in that area of the US. The result was devastating not only as regards the way the company reacted, but above all for the reaction of consumers : the rush to fuel . People rushed to fill as many fuel cans as possible, to avoid running out of water, with all the risks that these actions bring with them.
The IT action, which cost the company $ 4.4 million , could very well have been avoided . In fact, once the attack was over and the reports of the cybercriminals’ actions were analyzed, the lack of one of the simplest yet most effective security measures immediately became apparent: multi-factor authentication.
Without the latter, in fact, hackers faced only one barrier to break down before accessing the data , which is why the attack was so simple to carry out. The ease with which the attack hit was key in stimulating further Ransomware attacks , as it paved the way for the likelihood of high-caliber companies sinning from lack of cybersecurity just like the Colonial Pipeline. .
Attack on CNA Financial
Another recorded cyber attack was the one against CNA Financial. This was particularly impressive due to the ease with which the breach occurred against a security system that was considered to be one of the safest .
The consequences of the attack were primarily a network outage and, subsequently, the inability to regain full network operation. There were over 15,000 single victims of this attack . In fact, the attack took place remotely and hit the computers of almost all employees . The ransom demanded (and paid ) amounts to $ 40 million.
The identity of the attacker is unknown, but many details suggest Evil Corp as the perpetrator of the attack. The most obvious clue is the software used, which is called Hades, used in the past by Evil Corp.
Despite this, Evil Corp has never been sanctioned for the damage done to CNA Financial.

How to defend yourself?
As we have seen from the latest ransomware news, it is not easy to recover your data if you are a victim of this type of attack. Even if you decide to pay the ransom, you don’t necessarily get your data back. Consequently, the most effective defense is prevention, which can be done in a number of ways.
SOCaaS and UEBA to identify threats
One of the most effective ways to defend yourself is the UEBA system, integrated into the SOCaaS offered by SOD. This system is based on the analysis of users and entities . While it is easy for a hacker to obtain the login information of a corporate user, it is still difficult to behave normally without arousing suspicion. The UEBA system monitors the behaviors of each user and entity and triggers the alarm if their behaviors change. The change in habits may be legitimate, but in this way we can investigate immediately to mitigate the risk.
The UEBA system works thanks to different algorithms that monitor the habits of the users and systems involved and report any anomalies. Together with SIEM, they are fundamental components of the SOC that we offer to our customers.
Conclusions
In any case, it is advisable not to give in to ransoms for any reason. It is recommended to pay maximum attention to fraud and phishing and to install updated antivirus.
For greater high-level security for your company, do not hesitate to contact us to find out what solutions we can offer to secure your data. We will be happy to answer any questions.
Useful links:
Tempo di lettura stimato: 6 minutes
Today we are talking about the CTI update of our services. Data security is an aspect that must always be taken into consideration to prevent data from being stolen in any way.
Network problems
When you have a presence connected to the network, especially if it contains sensitive data, the potential threats to which you are exposed are manifold. The theft of your customers’ data, in fact, is only one of the potential negative situations that can arise and that could compromise the solidity of your site and the reputation of your company.
The Cyber Threat Intelligence (CTI) service, was created with the aim, not only of discovering which areas are most at risk, but also of preventing targeted attacks. Prevention represents the right solution thanks to which it is possible to avoid that the situation can become difficult to deal with and that there may be future complex problems to be solved.

CTI: preventive-threat analysis
Thanks to the CTI service we offer and our Cyber Treath Hunter , it is possible to prevent a planned attack hits. The search for vulnerable areas of the IT infrastructure represents the first process of the CTI service we propose.
This information, in fact, is that which is processed in the Dark Web , where most of the design of the attacks. The analysis of data leakage, therefore, is carried out with extreme care to understand what and how much data may have become the object of hacker attention . Consequently, we can also understand what specific attack targets or upcoming information at risk may be.
The various analyzes are carried out with care and precision, to avoid that vulnerabilities are exploited and the security of the structure jeopardized. Thanks to the analysis carried out by a team of professionals, your company will prevent attacks from hitting you and triggering economic and image problems .
The analyzes carried out by Cyber Threat Intelligence
As regards the different phases of the analyzes proposed by us, these are carried out in a particularly accurate manner. We practice a series of procedures thanks to which it is possible to identify what are the potential threats that may be present in the network.
Let’s look at these steps to understand how we go about offering a complete service to our customers.
Global-data analysis
After having hypothesized the type of threat to be avoided, then the necessary data that must be analyzed, the team of technicians in charge takes care of carrying out a series of information gathering procedures. Thanks to this we can understand if the necessary data are well protected or at risk of breach . Basically we try to think like hackers before they prepare for the attack.
The data are subjected to careful analysis and above all are adequately divided. This procedure was created to simplify the phase of studying the data themselves , thus preventing an accumulation of information that could lead to confusion during the analysis phase.
The data and the second-analysis, between fundamental and secondary information
Once the information gathering phase is complete, we move on to the initial analysis of the same. With this fundamental step it is possible to eliminate all the information deemed superfluous leaving space for those that have greater relevance in the study phase.
At this point, the data analysis phase takes place, the purpose of which is to actually understand what concrete threats to avoid can be.
During the study phase it is decided which are the different procedures to be adopted on the infrastructure to prevent attacks from being successful. Through these analyzes, we can then decide precisely how to further increase corporate data defenses.
The choice of security-measures to be adopted
Finally, there is the implementation of security practices with a specific task: to make the analysis results operational.
Here’s how, thanks to this set of procedures, the CTI service we offer is incredibly useful to avoid potential problems. We remind you that even a single attack carried out can have a significant impact in economic terms.
Prevention of future-attacks
Thanks to this set of CTI analyzes, you can, therefore, prevent future attacks. Our team is not only concerned with analyzing potential and future threats, but also those that may be based on the current situation of the IT infrastructure.
We want to underline, in fact, how constant threats are subject to rapid evolution and how important it is to always be adequately protected and prevented. With services like SOCaaS and CTI, we securely monitor the corporate network making sure it remains safe and healthy.

CTI: The importance of maximum-online-security
We therefore encourage you to consider these security risk situations as less remote than you might think. These same situations can be the cause of a series of breaches and data losses that can compromise the company.
Thanks to our SOCaaS, and especially the CTI. it is possible to avoid that the data present on the corporate network can be easily intercepted.
Understanding what the threats are, having a detailed report and above all analyzing the countermeasures that must be adopted is our task and thanks to our state-of-the-art systems we offer a complete service capable of putting the infrastructure in total safety.
Our services cover many security risk situations and we generally offer many professional solutions for companies. The SOCaaS, with system SIEM and UEBA, as well as CTI and
Keeping safety always on top is our job, if you want more information, don’t hesitate to contact us!
Useful links:
Estimated reading time: 6 minutes
Today we see one of the latest additions to our SOCaaS, the Autonomous Threat Sweeper (ATS) . A system able to support SOC in an innovative way and protect against the most innovative threats.
The Privacy Guarantor, through the provision dated May 27, 2021, has introduced some changes regarding the violation of sensitive and personal data. A particular reference was made to the numerous cases of data breach. In essence, the legislation relating to the notification system has been tightened . The legislation provides for the application of a certain procedure to be adopted in the event of a data breach.
It is not easy to stay up to date on the continuous regulations on privacy, nor to have IT threat prevention systems available such as i ransomware working in the shadows and increasingly aggressive and dangerous. For this reason, threat protection has become an issue that is no longer easily manageable through non-professional systems . Today specific IT skills are constantly updated and professionals working in the sector, especially for companies.

Context: the unstoppable growth of ransomware
As we know, the term ransomware defines a category of malware capable of encrypting the files and documents contained in the attacked computer, in some cases even on the network to which it is connected. We have seen this in various articles through known examples .
In recent years, ransomware has spread enormously, so much so that it is listed as the most dangerous cyber threat to businesses .
Among the main companies targeted are those that have a large amount of sensitive data which, if stolen, would expose the company to the distrust of their customers. The encryption of the files stored inside the devices is, therefore, resolved only following the payment of a ransom.
Unfortunately, once compromised, the system does not allow users to access the data on their devices, effectively preventing their use.
Currently, ransomware is one of the main cyber threats, so much so that it is categorized as a profitable business model. This is because of the constant improvements made to their software that make it easier for hackers to use. The result is an increasing number of attacks performed with tools that required almost no specific skills.
IT security: increased risk = increased insurance policies
In terms of computer security, the aspects to consider are different, among these, in fact, there is the one related to ransomware software. These require a greater definition of reporting requirements in the event of a data breach due to an increase in systemic risk.
This problem has led to an increase in the prices of the insurance market. As these threats, in addition to being more and more frequent, are the cause of high damage to companies, insurance companies have raised their prices. But not only that, today they also demand specific requirements from the policyholders, to demonstrate the use of adequate defense systems in the IT field.
Autonomous Threat Sweeper: the new technology integrated in SOCaaS
Preventive malware detection is the priority solution to be adopted in order to avoid the risk of being attacked by malware that can steal company data.
What is worrying, however, is not only the increase in the cost of insurance, but the greater definition of the required requirements. The requirements, that is, relating to the reports to be forwarded in the event of a data breach and the consequent increase in systemic risk .
The SOC as a Service is a service entirely dedicated to the IT security of companies, which involves data collection and enrichment aimed at proactive identification of social engineering attacks. The system includes a Security Data Lake (SDL), the event and information management (SIEM) and l ‘user behavior analysis (UEBA).
Through the Autonomous Threat Sweeper (ATS) the team is able to provide companies with 24/7 coverage through an automatic search. This, once activated, is able not only to to prevent attacks from the outside, but also to detect any malware previously installed on company devices.
This system allows you to automate the rapid detection of these threats. Once identified, it is easy to implement targeted actions in order to counter their attacks. Since cyber attacks are and will always be present in everyday business life, it is certainly important to be well equipped. Attacks will continue to grow in breadth and scale and let’s not forget the trend in the shortage of technicians . We can only bring into play systems that automate the first stages of control and detection.
The Autonomous Threat Sweeper (ATS) is currently one of the few systems capable of pre-coding the latest generation of cyber attacks . Its coverage includes corporate networks and devices.

Autonomous Threat Sweeper (ATS)
Autonomous Threat Sweeper (ATS) is a constantly updated system capable of detecting the latest generation threats. This guarantees companies that turn to us to always be protected from the latest generation IT risks to infrastructures and devices.
We have already talked about SIEM , software tools able to provide cyber security professionals with an analysis of logs and events to provide real-time threat minitoring. Here, the ATS even improves the functionality of software as complex and accurate as SIEM, making it capable of detecting low and slow threats through post-hoc.
Basically, with the ATS it will be possible to speed up the process of detecting threats in order to avoid damage that also compromises the strength of the infrastructure.
Conclusions: How to behave in case of violation
In the event that an IT breach occurs, with or without intent, involving the loss, destruction, modification or unauthorized disclosure or unauthorized access to the data processed by a company, the data controller appointed by the same must notify the violation within 72 hours.
Subsequently, investigations could take place to understand the extent of the damage and then also penalties in case of negligence. By adopting an Autonomous Threat Sweeper your business will be able to intercept threats before they can do any harm.
Preventing data breaches, ransom requests and other cyber security attacks is easy if you turn to competent people. Ask us for more details on how we can support your company with regards to cybersecurity. We will be happy to answer all your questions.
Useful links:
Webinar: SOCaaS (Security Operation Center as a Service) e NGS (Next Generation SIEM)
Pass the Ticket: how to mitigate it with a SOCaaS
Use cases of a SOCaaS for companies part 2
Use cases of a SOCaaS for companies part 1
Predictive cybersecurity with our SOCaaS

Estimated reading time: 5 minutes
Every year the number of attacks that threaten the security of devices, computer systems, servers and network infrastructures is growing steadily. This is done by taking advantage of the vulnerabilities present in these systems. Among the many types of attacks, particular attention must be paid to the pass the ticket (PTT) attack.
With a pass the ticket attack it is possible to take advantage of the Kerberos network protocol, present in all major operating systems, to access a user’s session without having his login credentials. An attack of this type can be difficult to detect and is usually able to bypass the most common system access controls.

Pass The Ticket: what it is and how it works
Kerberos
Before understanding in detail what a PTT attack is and how it works, it is advisable to clarify the Kerberos network protocol since an attack of this type uses this protocol. Kerberos is a network protocol designed by MIT in the 1980s and became a standard IETF in 1993. It is used for strong authentication between different terminals through a symmetric key encryption system, without transmitting any passwords.
The advantage of using the Kerberos protocol lies in its strong authentication system between client and server. This makes it very effective against phishing and “ man in the middle ” attacks.
Kerberos is integrated into all major operating systems belonging to well-known companies such as Microsoft, Apple, Red Hat Linux and many more.
With a pass the ticket attack it is possible to exploit Kerberos authentication to gain access to a user account. The consequences that such an event could entail are not are to be underestimated. Among the many imaginable scenarios, for example, there could be the possibility that the compromised account enjoys high administrative privileges thus guaranteeing the hacker full access to resources.
The attack
A pass the ticket attack allows you to gain privileged access to network resources without having to use any user passwords . Here’s how: In Active Directory, a Ticket Granting Ticket (TGT) serves to prove that a user is just who he says to be. Through some tools and techniques, a hacker could collect these tickets and use them to request Ticket Granting Services (TGS) in order to access resources present in other parts of the network.
A PTT attack could involve risks even if the compromised account does not have particular administrative privileges since the hacker, through the Lateral Movement, may be able to gain access to other accounts and devices.
The difference between pass the ticket and an attack pass the hash lies in the fact that the former exploits TGT tickets that have an expiration of a few hours, while the latter uses NTLM hashes that change only in case a user decides to change his password. A TGT ticket must be used within its expiration time or renewed for a longer period of time.
How to Defend and Prevent a Pass The Ticket Attack
Keeping a network and the devices connected to it safe is a very important factor. You must always have protocols and software that are able to guarantee effective protection from all kinds of threats , with up-to-date systems that keep sensitive information safe. Enterprises can take advantage of endpoint detection and response technologies. Local detection of multiple tickets used for the same session will be possible.
Account case without-privileges
In the event of a pass the ticket attack, if the compressed account from which the TGT or TGS was stolen was a low-privilege account, the mitigation could be quite simple. Just reset the user’s Active Directory password. Such an action would invalidate the TGT or TGS, preventing the hacker from generating new tickets.
Case-account with privileges
Conversely, if the PTT attack compromised a privileged account, limiting the damage is much more difficult. In these cases, companies could respond to the attack by resetting the Kerberos TGT service to to generate a new signing key, making sure to delete the compromised key.
Next you need to drill down into Kerberos logs and Active Directory information to investigate and find out which network resources have been compromised. In this way it is also possible to understand which data may have been stolen. The technology SIEM allows organizations to assimilate, analyze and analyze this data.

Protection from attack
To ensure complete protection of an infrastructure, also preventing pass the ticket attacks, it is good to use valid detection technologies such as UEBA and SIEM. In fact, it is possible to prevent Pass The Ticket attacks by analyzing the behavior of users and entities. The solution UEBA , in these cases, would ensure the quick identification of any compromised account, blocking it in order to mitigate the damage.
Some software SIEM also allow not only to analyze traditional logs but are also able to provide an accurate analysis of security , analyzing the behavior of the network and users in order to detect promptly the presence of any threats to the infrastructure.
Conclusions
We have seen what a pass the ticket attack is and how companies can adopt specific solutions to intercept the dangers and anomalies of an entire IT infrastructure. This allows us to mitigate threats more effectively.
A complete solution, as we have seen, involves constant and granular communication monitoring . The solution we propose for this purpose is a SOCaaS .
If you want to know our dedicated security services, do not hesitate to contact us. You can use the button below, we will be happy to answer any of your questions.
Useful links:

Estimated reading time: 5 minutes
In the previous article we have seen the most common use cases of a SOCaaS , explaining how it can be useful for companies to use this tool to prevent cyber attacks and also explaining which are the most common Threat Models .
In this article, however, we will take a closer look at some of the more common indicators of compromise (IOC). First we will briefly look at the malware threat models that the use of a SOCaaS can prevent and block. As it works, a SOCaaS can be very flexible and analyze a lot of data at the same time, thus providing in-depth and accurate results.

Malware Threat Models
It is important to know how to distinguish and classify the different types of malware to understand how they can infect systems and devices, the level of threat they represent and how to protect against them. We at SOD recommend adopting the use of a SOCaaS in order to be able to classify the entire range of malware or potentially unwanted objects. Malware is categorized based on the activity they perform on infected systems.
Wannacry Malware Detection
Thanks to this threat model it is possible to detect the behavior of the well-known malware Wannacry.
Wannacry malware is a ransomware that attacks the system by encrypting files of particular importance to an organization in order to make them illegible.
Early detection of ransomware is probably the most effective action you can take to defend yourself. There are also services that are able to block the action of the malware and restore any files already encrypted with those of a backup, for example Acronis Cyber Protect Cloud .
Network anomaly followed by data infiltration
Identifies successful network data aggregation attempts, followed by signs of data infiltration. Below we see some of the anomalies and how the use of a SOCaaS can identify important clues to counter threats.
During a network scan you may notice enumerations of AD accounts and privileges, count of LDAP services outside the corporate network and a suspicious number of ticket requests to Kerberos protocol . In addition, other indicators can be a spike in LDAP traffic and the enumeration of SMB services.
As regards the anomalies of the network drive , the use of a SOCaaS is able to control access to the sharepoint in order to identify an unusual number of accesses to shared elements. This also in relation to users and their level of access.
In terms of Data Aggregation and data infiltration, the quantity of bytes downloaded from the server ports and via FTP protocols are monitored, as well as an unusual quantity of bytes transmitted to the external.
Petrwrap / Goldeneye / Amalware detection
This threat model aims to detect malware Petrwrap . The use of a SOCaaS can detect network scanning activity by monitoring the number of SMBv1 activities, as well as anomalies in these activities. Attempting to reach a never-before-reached host may also be an indicator.
Another way in which these threats can be detected with the use of SOCaaS is by auditing of suspicious privileged activity. For example, it is verified that there is no escaletion of privileges, unusual access to an admin zone or even tampering with log files.
Risk indicators in general
Risk indicators are metrics used to show that the organization is subject to or has a high probability of being subject to a risk.
These indicators are used to classify the type of behavior or threat for a policy and can be used in multiple policies for different functionality based on the data source. Risk indicators can be chained with threat models to identify sophisticated attacks across multiple data sources.
In essence, these are clues or alarm bells that indicate events that a company’s security operators should pay particular attention to. The use of a SOCaaS can help identify these clues by analyzing large amounts of data and logs in a short time.
Below is a non-exhaustive list of some of the most common threat indicators that are identifiable through the use of a SOCaaS. We will divide them into different areas, for clarity.
As for accounts, obviously, blocking an account is an alarm bell, as well as an unusual number of accounts created or a disproportionate number of failed authentication. Finally, the use of a SOCaaS could indicate an IOC as a suspicious number of accounts running concurrently .
Access
The anomalies concerning the access or in any case the account include the detection of access to the anomalous administrative sherepoint but also the loading times of the anomalous applications. Applications that use an unusual amount of memory may also be indicators of compromise.
As for accounts, obviously, blocking an account is an alarm bell, as well as an unusual number of accounts created or a disproportionate number of failed authentication. Finally, the use of a SOCaaS could indicate an IOC as a suspicious number of accounts running concurrently .

Networks
Network alarm bells are, of course, the most common. Since networks are like “roads” of a corporate infrastructure, it is normal that anomalous behaviors in these are particularly relevant.
Common indicators are abnormal DNS zone transfers or failed requests to the firewall. But also an abnormal number of running hosts or ICMP connections. Traffic in general is also controlled through the use of SOCaaS, so that any suspicious data movement is analyzed or otherwise verified. Examples of this are packet movements to critical ports, RDP, SSH, or connection attempts to a DHCP server. These events often indicate abnormal attempts to connect to objects or network shares.
Through the use of a SOCaaS it is also very simple to control the behavior of the accounts that often show alarm bells in themselves . For example, an account logging into a host for the first time, creating an account, or adding privileges.
Conclusions
Relying on luck to catch threats is madness , as demonstrated by SolarWinds attack .
Create your luck with our SOCaaS solution , making sure you spot threats before incidents happen and that you are “lucky” enough to counter them.
Contact us to find out how our services can strengthen your company’s defenses, we will be happy to answer any questions.
Useful links:

Estimated reading time: 6 minutes
Cyber Threat Analytics applications monitor security logs and the network to promptly detect any malware infections (for example, attacks zero day e i ransomware), the compromise of the system, the activities of “ lateral movement ”, pass-the-hash , pass-the-ticket and other advanced intrusion techniques. The use of a SOCaaS allows to extrapolate data from sources such as firewalls, proxies, VPN, IDS, DNS, endpoints, and from all devices connected to the network with the aim of identifying harmful models such as “beaconing”, connections to generated domains digitally, actions performed by robots and all anomalous behaviors.
Our system SOCaaS is equipped with artificial intelligence that enriches and transforms events SIEM, so you identify threats across your entire IT environment, including business-critical applications.
What are the-advantages at the enterprise-level?
The use of a SOCaaS. Below is a list with only some of the advantages that the use of SOCaaS can entail rapid detection of violations, reducing the impact of these. Additionally, a SOCaaS provides comprehensive threat responses and investigations, decreases monitoring and management costs, as well as compliance costs.
The use of a SOCaaS also allows you to receive quantified and non-subjective reports on threats and risks.

SOCaaS use cases
After a general overview of the advantages that the use of SOCaaS could offer to the company, let’s see in what contexts it is normally used .
A SOCaaS consists of elements that are very suitable to be applied in case of abnormal execution of applications, as well as in the analysis of bot traffic to a malicious website.
In other cases, SOCaaS identifies unusual DNS queries, a possible remote command and control activity, analyzes the spikes in bytes to external destinations and then also checks the traffic, relating it in an application / port context.
Other scenarios in which the use of SOCaaS is ideal are the detections of exploits, sessions of unusual duration, but also connections to IPs or blacklisted domains and anomalous activity in general.
Finally, it can also detect targeted SPAM attacks and phishing attempts.
Threat Models
By analyzing threat indicators it is possible to detect correlated behaviors on multiple data sources, to also detect all those threats that usually go unnoticed. Multiple threat indicators occurring in a scheme and involving similar entities tend to present a greater risk of posing a real threat.
The Threat Models define these patterns and combine threat policies and indicators to detect related behaviors across multiple data sources, identifying threats that may go unnoticed. Below are some of the more common Threat Models that are included in the use of a SOCaaS
Lateral Movement Detection
This Threat Model detects the possible scenarios of “ lateral movement “, used by attackers to progressively spread across a network in search of key resources and data. The signs of such an attack can be varied and we can divide them into three categories: Abnormal authentication, suspicious privileges, abnormal process.
Abnormal authentication is usually detectable by some clues. For example if an account accesses a host that has never been reached before. Or if explicit credentials are used on multiple hosts, or if a suspicious authentication type / process is detected.
Concerning suspicious privileges, here are some indicators detectable with the use of a SOCaaS:
- abnormal provisioning activity
- suspicious escalation of privileges
- abnormal access to network share objects
An abnormal process is detected in this way through the use of a SOCaaS: an unusual process code, or the suspicious creation of scheduled tasks. Alternatively, suspicious changes to the registry settings may be detected.
Detection of compromised hosts
This model is employed in the use of SOCaaS to detect hosts showing signs of infection and compromise by relating host and network based anomalies to the same entity.
A possible alarm is given by anomalies in outgoing traffic . This occurs when traffic goes to random domains or known malicious hosts. In other cases, however, an abnormal number of domains contacted is another alarm bell detectable through the use of a SOCaaS.
anomalies in the endpoint are found when rare processes or suspicious use of ports or protocols by the process itself are found. One possibility is also to detect an unusual agent.
APT detection using a SOCaaS
Detection APT detects attacks on health care networks , where the attacker’s aim is usually to obtain a unauthorized access to a network with the intention of remaining undetected for an extended period.
This includes phishing attempts , detection of a network scan or circumvention of controls. In the delivery phase, however, traffic to random domains, an anomaly in DHCP traffic or traffic destined to known malicious hosts may be identified.
During an exploit , the indicators can be: the detection of activity from terminated accounts, anomalous DNS traffic, but also a suspicious authentication process. Another possible indicator identifiable with the use of SOCaaS is an anomaly in the speed of the network.
Through the use of a SOCaaS, cases of data exfiltration can also be detected. The signals in this case are l ‘Unauthorized upload of data over the network.
Detection model Phishing using SOCaaS
This model is able to detect possible phishing attempts towards users within the organization . We’ve talked about it in other articles as well, and here are some indicators of this type of attack. A wake-up call is definitely the detection of known phishing campaigns. It is also not uncommon for spear phishing attacks to be detected.
The use of a SOCaaS is also able to identify possible phishing attempts or persistent phishing campaigns, thanks to the comparison with emails from senders / domains / IP addresses known in the blacklists. As usual, beware of suspicious email attachments, but the use of a SOCaaS could automate, at least in part, the checks.
It is then possible to identify outbound traffic anomalies , for example that towards random domains, which is also a possible phishing signal. Classic traffic to malicious hosts, an abnormal number of rare domains accessed, can also be indicators.

Host / Account Enumeration on LDAP
Usually used to identify potential assets or account enumerations on the network by malicious entities.
Running suspicious processes
- Abnormal process / MD5 detected
- Use of possible sets of AD (Active Directory) enumeration tools
- Detected use of malicious tools and utilities
Network scanning
- Possible AD accounts / enumeration privileges
- LDAP or SMB service count
- Abnormal number of Kerberos service ticket requests
- Port scanning
Authentication anomalies
- Accounts accessing a host for the first time
- Using never-before-seen accounts on the network
- Abnormal number of failed authentication requests
Reconnaissance followed by potential exploitation
This threat model aims to identify successful network reconnaissance attempts, followed by indicators of exploitation.
External scanning
- Scanning ports from external hosts
- Enumerating hosts from external hosts
Network scanning
- Possible count of AD accounts / privileges
- Enumeration of LDAP services
- Unsolved number of Kerberos service ticket requests
- Spikes in traffic LDAP
- Enumeration of SMB services
Anomalies in processes
- Detection of abnormal processes or MD5
- Suspicious creation of scheduled tasks
- Suspicious changes to registry settings detected
Conclusions
We have seen what are the major SOCaaS use cases, taking a look at some of the most common threat models that it includes in its protection system. For information on malware threat patterns and threat identifiers visit this article.
Using a SOCaaS is a solid and highly valuable business solution, ask us what it can do for your business, we will be happy to answer any questions.
Useful links:

Tempo di lettura stimato: 7 minutes
Quando parliamo di “left of boom” o “right of boom” ci riferiamo ad un concetto che all’apparenza può sembrare superficiale. Invece, è un potente strumento che offre la possibilità di analizzare i conflitti di sicurezza sia da un punto di vista offensivo che da uno difensivo. In una ipotetica linea temporale di un attacco, ciò che si trova alla sua sinistra (left of boom) si riferisce a quello che accade prima. Analogamente, ciò che sta alla destra, è quello che avviene dopo.
Nel linguaggio comune molto spesso anziché “boom” si utilizza il termine “bang”, ma il significato resta comunque invariato. Si tratta, in sostanza, dell’evento stesso intorno al quale si analizza il periodo precedente e successivo.
Quindi, “left of boom” è l’insieme di eventi che si verificano prima dell’attacco. “Right of boom”, invece, è l’insieme di eventi che seguono il “boom”. Questa è la differenza sostanziale tra i due termini. Se le azioni difensive riescono a rilevare gli eventi nel periodo “left of boom”, è possibile trovare e adottare soluzioni per prevedere quando accadrà il “boom”.
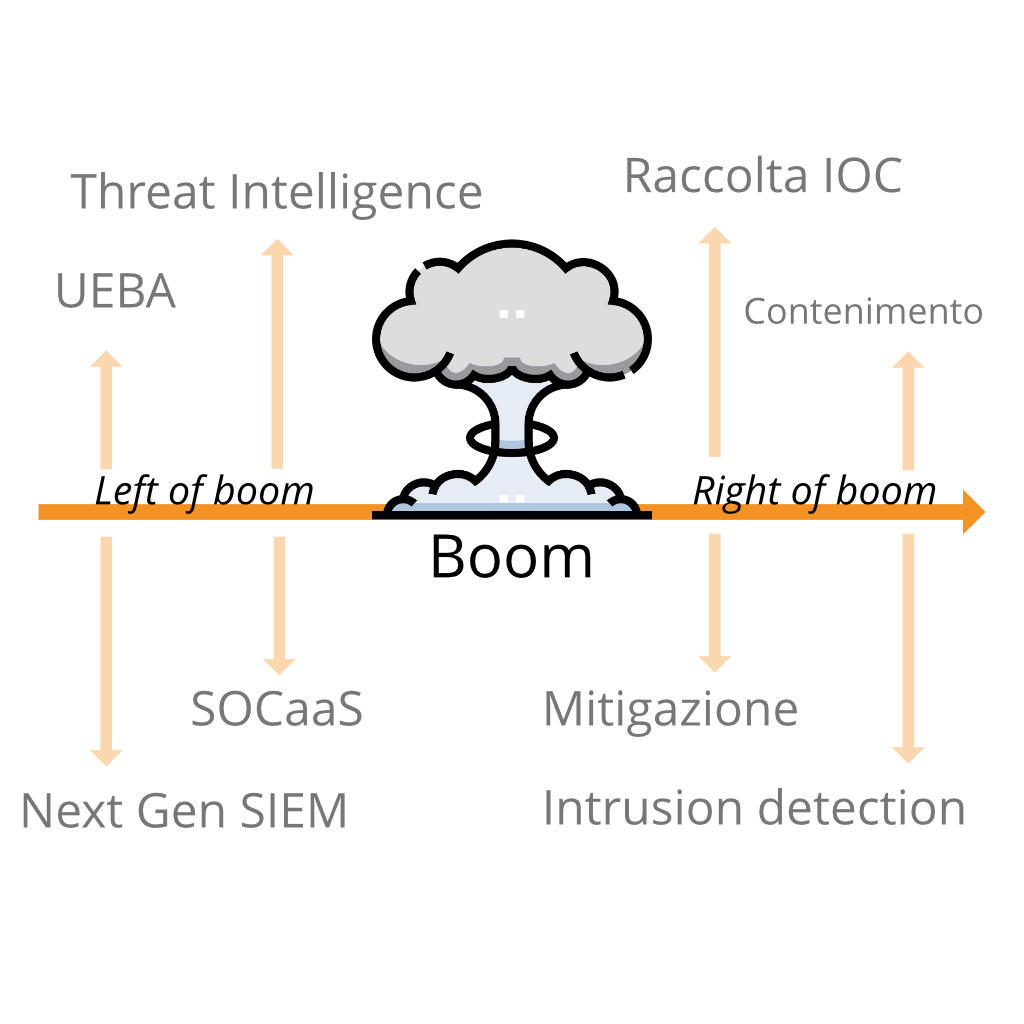
Per una persona inesperta nell’ambito della sicurezza informatica, questi concetti riguardanti la linea temporale di un attacco informatico potrebbero non essere nemmeno presi in considerazione, per questo motivo molte aziende preferiscono avvalersi di un SOCaaS.
Left of Boom
Un buon penetration tester riesce a rilevare alcuni eventi di tipo “left of boom”, ma spesso si tralascia la raccolta di informazioni sulle minacce. Certe volte non è in grado di distinguere tra loro concetti come “ingegneria della sicurezza, scoperta e risoluzione delle vulnerabilità” da un “controllo di prevenzione automatizzato”.
Non esiste in realtà un vero strumento valido di prevenzione, più che altro i controlli di sicurezza sono controlli di rilevamento. Alcuni di questi controlli integrano dei meccanismi di risposta automatizzati che impediscono il susseguirsi di spiacevoli eventi.
Un’applicazione web che previene attacchi di tipo XSS o SQLI è davvero utile per rilevare input non validi e risponde scartando il contenuto prima che l’iniezione possa verificarsi.
Un firewall progettato per bloccare le porte rileva semplicemente il traffico indesiderato in relazione al protocollo usato per la connessione e al numero della porta verso la quale si desidera accedere, interrompendo e reimpostando la richiesta di connessione.
Questi esempi si legano bene al concetto di “right of boom”. I controlli di prevenzione rilevano il “boom”, l’evento, e rispondono immediatamente arginando i possibili danni. “Left of boom” e “right of boom” sono così vicini nella linea temporale che sono difficilmente distinguibili, fino a quando non si esegue un’analisi accurata degli eventi.
Questo è uno dei motivi per cui i professionisti, nell’ambito della sicurezza informatica, amano i controlli di prevenzione. Lavorano rapidamente per correggere gli errori prima che gli hacker riescano a raggiungere i loro obbiettivi, limitando i danni.
Un SOCaaS in questi casi è una delle soluzioni migliori da adottare per proteggere l’integrità di un sistema informatico.
Right of Boom
Generalmente minore è la distanza tra “right of boom” e il tempo di risposta ad una minaccia, minori sono le conseguenze provocate da un eventuale attacco informatico. Ovviamente questa è solo una considerazione logica, non vale come regola assoluta.
Per alcune violazioni, la linea temporale tra l’evento e l’eliminazione completa della minaccia è discutibile, poiché il rilevamento è avvenuto dopo che l’hacker ha raggiunto il suo obbiettivo. Se gli hacker riescono ad infiltrarsi nel sistema ma vengono fermati in tempo, non arrecando nessun danno all’infrastruttura. In questo secondo caso, quindi, non c’è il “boom” di cui stiamo parlando.
Un esempio di right of boom
Per spiegare meglio il concetto di “right of boom” potremmo prendere come esempio un comune “malware”. I malware generalmente vengono sviluppati per attaccare in massa molti dispositivi, senza tanta discrezione. Con “right of boom” ci riferiamo a quel periodo di tempo che è passato da quando è avvenuta l’infezione da parte del malware.
Se hai letto gli altri articoli pubblicati da noi avrai appreso come gli hacker utilizzano queste tipologie di infezioni allo scopo di raccogliere informazioni sensibili, che vengono rivendute ad un terzo soggetto. Se il “right of boom” è più breve del tempo che l’hacker impiega per vendere queste informazioni, il danno può essere contenuto.
I migliori sistemi di sicurezza riescono ad accorciare il tempo “right of boom” riuscendo a raccogliere informazioni sugli attaccanti nel “left of boom”. Ci si può riuscire implementando delle contromisure in base al modello di minaccia. Questi strumenti permettono di scansionare intere infrastrutture, osservando i nuovi indicatori di minaccia giorni o addirittura settimane prima che gli attacchi si distribuiscano.
Come abbiamo visto anche in altri articoli, non sempre gli attacchi si svolgono in breve tempo. È, anzi, più probabile che gli hacker coinvolti agiscano in un primo, lento, periodo solo per raccogliere le informazioni necessario per sferrare l’attacco. Nel periodo “right of boom”, tornano utili strumenti come la cyber threat intelligence e un team di threat hunting.

Perché sono importanti i concetti “Right e Left of boom”
Se ci mettessimo nell’ottica dell’hacker, il concetto di “right of boom” e di “left of boom” può aiutare a decidere quale schema d’azione sia meglio intraprendere.
Supponiamo il caso in cui un hacker abbia a disposizione due metodi per potersi introdurre in un sistema informatico. Se uno dei due metodi potrebbe venire rilevato nel periodo “left of boom”, invece l’altro nel “right of boom”, è ovvio che l’hacker preferirà il secondo. Infatti, questo garantirebbe maggiori probabilità di successo dell’attacco.
Analogamente, tra due metodi che possono essere rilevati “right of boom” si sceglie quello che ha più possibilità di venir scoperto in ritardo. Più tempo passa dal boom alla rilevazione, maggiori sono le probabilità di successo. Questo tipo di ragionamento è importante per determinare quale tattica ha una linea temporale più ampia.
Ragionare in quest’ottica non è affatto semplice, richiede delle conoscenze avanzate da parte dell’esperto di sicurezza. Richiede inoltre il dover prendere in considerazione tutte quelle ipotesi che potrebbero potenzialmente determinare il successo dell’hacker.
Velocità
Un hacker è in grado di riuscire a prevedere se, utilizzando determinate tattiche, riuscirebbe a raggiungere l’obbiettivo più velocemente rispetto all’esperto che cerca di rilevare gli attacchi. Il “boom” è il primo contatto, nell’insieme delle tattiche d’intrusione utilizzate per accedere illegalmente ad un sistema informatico. Le rimanenti tattiche si collocano prima e dopo di esso.
Velocità e furtività solitamente si annullano a vicenda. Infatti, molto spesso si può essere più veloci sacrificando parte della furtività.
Velocità e furtività non vanno molto d’accordo quando parliamo di attacchi informatici. Essere furtivi, evitando di lasciare tracce, richiede più attenzione e quindi inevitabilmente anche più tempo. Tuttavia se lo scopo di un hacker non è un singolo obbiettivo ma una serie di più obbiettivi, l’essere veloci può rivelarsi efficace.
Per difendersi dagli attacchi, è possibile raccogliere gli indicatori di compromissione (IOC) per rimediare alle vulnerabilità presenti e per introdurre nuovi controlli di rilevamento, rendendo più sicuro il sistema informatico.
Conclusioni
È importante conoscere il concetto di linea temporale degli attacchi e abbiamo visto come i concetti di “left of boom” e “right of boom” influenzino i meccanismi di risposta alle minacce di intrusione.
I concetti che abbiamo visto in questo articolo, nonostante non aggiungano niente di concreto alle tecniche di difesa o di attacco di un sistema, offrono un punto di vista. Nella continua lotta tra hacker e operatori di sicurezza, avere una strategia vincente significa non solo disporre di strumenti efficienti, ma anche pianificare in modo dettagliato ogni dettaglio, prima e dopo gli attacchi.
Per sapere come un SOCaaS può aiutarti a monitorare l’infrastruttura aziendale e cogliere gli indizi “left of boom”, non esitare a contattarci, sapremo rispondere a ogni domanda e ti offriremo una soluzione per la tua azienda.
Useful links:

Estimated reading time: 4 minutes
Today, facing an attack in a corporate SOC is very similar to being under attack without knowing which direction the blow is coming from. The threat intelligence can keep you informed of security issues. However, in many cases, this information is only provided when you are already under attack, and is rarely very useful except in retrospect. It would take a different approach to data analysis, and that’s exactly what we propose with predictive cybersecurity .
In cybersecurity, threat intelligence is still relied upon as a fundamental defensive tool. Unfortunately, threat intelligence only covers a subset of threats that have already been found, while attackers constantly innovate . This means that new malware executables, phishing domains and attack strategies are created all the time.
Threat intelligence has a strong value for reactive incident response. It helps when pivoting through an investigation, identifying intent or other useful data, and providing additional investigative assistance. But it has limited value for detection, as threat actors avoid reusing their attack infrastructure from one target to another.
If the clues you see are different from those known from previous attacks, what can you do to move forward with effective detection? A legitimate question, for which predictive cybersecurity perhaps has an answer.
… what if you could know what is going to hit?
SOCaaS: predictive cybersecurity
Eyes on opponents rather than past attacks
The SOCaaS solution offered by SOD brings predictive cybersecurity capabilities to cybersecurity. The solution maps adversaries , instead of threats, and analyzes their actions to predict the behavior and the tools used in their attacks.
The analytical engine translates behavioral patterns into profiles of adversary attack infrastructures , which indicate as ( trojan, phishing or other forms of attack ) and where ( branches, customers, partners, peers, industry and geographies ) < strong> attackers are planning to target your company .
This provides a preemptive attack map, which identifies opponents based on their attack phase and current position within the extended business landscape . But not only that, in fact, information about the opponent, typical attack patterns and possible countermeasures that can be taken in advance are also identified. This way you can cancel the threat before it materializes .

Predictive cybersecurity: understand what’s going to happen first
Our SOCaaS provides predictive detection capabilities against internal and external threats with the combination of user, entity and adversary behavior analysis. Our Next-Gen SIEM uses an analytics-driven approach to threat detection. SOC provides visibility in the crucial early stages of an attack. That is when cyber actors are targeting, planning and preparing the infrastructure for an attack.
With this level of predictive visibility, the team can prevent attacks and systematically contain those in progress. Predictive cybersecurity allows defenders to tune their systems against the attack infrastructure. In fact, it is possible to build blacklists that include the IP addresses and the host names of the instances used for the attack . Other measures include fortifying corporate systems against the specific malware that is used to target them, rendering the attack powerless when it occurs.
Opponent Behavior Analysis extends the capabilities of Next-Gen SIEM by continuously providing updated analysis of opponent information and behavior . This encompasses the entire attack infrastructure for dynamic and proactive threat protection.
SOCaaS automatically translates the pre-attack behavior of opponents into actions or countermeasures that can be taken against phishing, compromise of corporate email, ransomware, fraud and many other common threats.
Common use-cases
Threat-chaining
Correlate breaches from the same adversary / campaign into a cohesive threat, even if different pieces of attack infrastructure are used for each event.
Prevention and preventive defense
Preemptively blocking an opponent’s entire attack infrastructure, such as newly created phishing domains, for preemptive defense.
Strengthen vulnerable resources
Focus and secure the most vulnerable parts of your infrastructure based on information that identifies which areas are possible targets.

The information provided by SOCaaS is used to add more context to existing threats, as well as provide information on attacks that have not yet been implemented or are in the early stages, such as reconnaissance. This allows for direct action against evolving threats and a more robust defense.
Conclusions
Relying on luck to catch threats is madness, as the recent SolarWinds attack . Make your fortune with SOD’s SOCaaS solution, making sure you see threats before they happen and are “lucky” enough to counter them.
Useful links:

Estimated reading time: 8 minutes
The term shoulder surfing might conjure up images of a little surfer on his shirt collar, but the reality is much more mundane. shoulder surfing is a criminal practice in which thieves steal your personal data by spying on you while using a laptop, ATM, public terminal or other electronic device among other people . This social engineering technique is a security risk that can cause disaster, especially if the stolen credentials are corporate.
The practice long predates smartphones and laptops and dates back to when criminals spied on pay phone users as they entered their calling card numbers to make calls . Many years have passed, but the technique has not been lost. Thieves have evolved to observe their victims typing their ATM PINs, paying at self-service petrol pumps, or even making a purchase in a store.
A similar technique for ATM theft involves a card cloning device superimposed on the card insertion hole and a micro camera to spy on the code. The micro camera performs an act of shoulder surfing . Card cloning is essential because without a physical device the pin is useless, but in the case of account credentials on the network, all you need is user and password.

When does Shoulder Surfing take place?
shoulder surfing can happen whenever you share personal information in a public place. This includes not only ATMs, coffee shops and POS devices in general, but virtually any place where you use a laptop, tablet or smartphone to enter personal data.
Long-time shoulder surfers did not usually loom behind their victims to scrutinize information. Instead, they stood at a safe distance and interpreted finger movements as people typed numbers on the keyboard . Similarly, today’s social engineers often escape attention as they quietly observe others in public places such as airport lounges and shopping malls, bars and restaurants, on trains or subways, or wherever there are people, to tell the truth.
Indeed, today’s most sophisticated criminals are watching from further away, hidden from view. They could use binoculars, micro cameras, or the camera of their phone or tablet to scan your screen or keyboard. Not only that, they may eavesdrop as you read credit card numbers on the phone or provide other sensitive information. Criminals could also take pictures, make a video or audio record of the information and then interpret it later.
Whatever the methodology, it is clear that technology has not only helped us to be more connected and be able to afford to pay for a frappuccino with our mobile phone, but it has also exposed us to security risks. When it comes to sensitive data, especially if there is a corporate account involved that could access other people’s sensitive data, you should never let your guard down , consequences could be very serious .
As shoulder surfing commonly happens
Before suggesting some methods to prevent shoulder surfing to be put into practice immediately, let’s take a closer look at how credential theft could happen with this technique.
At the bar or in the cafeteria
You’re in a busy restaurant bar waiting for a friend. To pass the time, you connect to Instagram. Unfortunately, you don’t notice that the person stuck in line next to you is looking at your password, which happens to be the same one you use for your email and bank account.
At the ATM
You’re taking cash at an ATM. You feel safe because the man after you in line is at least 10 feet away and is even looking at his phone. In fact, he is recording your finger movements on his phone and will later decrypt them to get your PIN number.
To the airport
Your flight is delayed, so grab your laptop and kill your time by reading a couple of work emails to keep up to date. Log in to the company website to read your mail and enter your username and password. You are so calm that you don’t see the woman a few places away as she stares at the screen while you enter data.

What are the consequences of shoulder surfing?
Using your credit card information to make fraudulent purchases is just one example of the damage you could suffer if you fall victim to shoulder surfing . The more personal information a criminal captures about you, the more serious the consequences can be for your bank account and financial health.
A serious case of shoulder surfing can expose you to identity theft . A criminal could use your personal information, such as your social security number, to open new bank accounts, apply for loans, rent apartments, or apply for a job under your name. An identity thief could get their hands on your tax refund, use your name to get medical treatment, or even apply for government benefits in your name. They could also commit a crime and provide your personal information when questioned by the police, leaving you with a dirty record or arrest warrant.
Of course, if you suspect this has happened, you’ll need to go to the police immediately, block your checking accounts and notify the bank. If fraudulent actions have already been carried out in your name, you may need to prove that you are not involved.
Things get dangerous if the stolen data is from a corporate account. In fact, with the use of valid credentials, anyone could enter the company’s system and perform all kinds of actions, such as collecting additional data, placing malware, running a ransomware , steal customer data and then sell it online.
How to defend yourself from shoulder surfing
Two levels of protection can be identified, the first is proactive and is aimed at preventing credentials from being exposed to malicious people, the second is active and provides software to detect attempts to use stolen credentials.

Defend yourself proactively
If you really can’t avoid entering sensitive data on your laptop, tablet or smartphone in a public place, you should follow the countermeasures listed below.
Tip 1: Before entering any sensitive data, find a safe place . Make sure you sit with your back to the wall. This is the best way to protect yourself from prying eyes. Avoid public transport, the central armchairs of a waiting room and places where there is a lot of people coming and going.
Tip 2: Use a privacy filter. This hardware device is a simple polarized translucent sheet that is placed over the screen. It will make your screen look black to anyone looking at it from any unnatural angle . This will make it much more difficult for unauthorized people to see your information.
Tip 3: Two-factor authentication requires a user to prove their identity using two different authentication components that are independent of each other. Since this type of authentication only passes when both factors are used correctly in combination, the security measure is particularly effective. For example, this method is often used a lot in online banking. There are many services that allow you to use your mobile phone as a second authentication factor . This is done through special apps.
Tip 4: Another solution is to use a password manager . By doing so, you no longer have to enter each password individually on your computer. The password manager will do this for you after you enter your master password . This prevents unauthorized people from using your keyboard to determine the real password, provided that you properly protect your master password .
Actively defend yourself with a SOC and behavior analysis
Now let’s imagine that the corporate account credentials have been stolen. At this point only a behavior control system can trigger an alarm and therefore block the user before there is any damage.
In fact, using correct credentials, a normal traditional SIEM would not trigger any alarms. For an older generation SIEM, access would be legitimate, because the credentials are correct. The attacker would have free undisturbed access to the system and could continue with his attack plan.
With SOD’s SOCaaS service, however, abnormal access would trigger an alarm. The SOC provided is equipped with a Next Generation SIEM and a system UEBA control behavior . This means that any deviation from the user’s usual behavior would be reported.
In the case of credential theft, as happens with shoulder surfing, the access made by the attacker would therefore trigger an alarm because something is wrong . For example, the login could take place at anomalous times, in another country / IP, from a different operating system, etc.
Conclusions
shoulder surfing is a social engineering technique that focuses on user carelessness while entering sensitive data into a system. In the event that a user’s corporate credentials are stolen, the only really efficient thing is to have a system that analyzes user behavior and reports whenever suspicious actions are detected.
If you want to know in detail how a SOC and UEBA system can help your company defend against social engineering attacks, do not hesitate to contact us, we will be happy to answer any questions.
Useful links:
Estimated reading time: 6 minutes
The cost of cybercrime has now outstripped the ability to keep up. Gartner, a multinational security and analytics company in the field of technology, predicted that world spending on cybersecurity will be 16 times lower than damage caused. To address this challenge, organizations are now turning to machine learning and artificial intelligence for cybersecurity, trying to fill in the gaps.
The vast majority of malware targets known vulnerabilities, but botnets often go unnoticed within the victim organizations for around 12 days. The problem in many cases is the scarcity of resources a arrangement.
The attack surface has expanded in recent years with the adoption of IoT devices and the spread of BYOD (Bring Your Own Device) work environments. This, combined with the increasing sophistication of the attacks and increasing the security skills gap, has overwhelmed many teams.
In response, service providers MSSP are increasingly implementing a machine learning system in their cybersecurity solutions. This is certainly an interesting field and many security chiefs are looking for a permanent solution in the fight against cybercriminals. But the question is whether the machine learning offered by artificial intelligence can add new value to the realm of security.
Threat detection and prevention
Most companies are operating with a standard security kit. Their rooms are filled with devices that claim they can detect and prevent the latest threats through signature-based detection, predefined policies or custom configurations. Sensors in this category include firewall , DLP ( Data Loss Prevention ), IPS ( Intrusion Prevention System ) and WCF ( Web Content Filter ) . An alarming consideration, as these sensors continue to be adopted in large numbers, many of them may not be configured correctly .
Furthermore, many of these devices operate in complete isolation , unable to share or correlate information or respond to threats with any kind of coordinated strategy. Consequently, controlling these devices also requires an extra layer of sensors , along with additional members of the security team. Of course, more sensors and more data require more people and given the current security skills shortage, this strategy is unsustainable in the long run.
Through a complete system such as a SOC , however, this does not happen. The collection, correlation and analysis take place in a coordinated way in a SOAR (Security Orchestration, Automation and Response) designed to be a unique workflow. Part of these tasks is done by artificial intelligence and machine learning mess and in the service of cybersecurity . The aim is to analyze user behavior and identify anomalies, as well as learn from past analyzes.
Machine learning for cybersecurity
Machine Learning (ML) is a subset of AI (Artificial Intelligence). AI and ML can enhance our human capabilities by allowing us to dig through large datasets and locate patterns behavior or signals that would be nearly impossible for humans to find. This force multiplier allows technicians at their disposal to identify unusual behaviors. Then the behavioral analysis with UEBA (User Entity Behavior Analytics) tools for safety will do the rest. Mundane and repetitive tasks can also be automated with machine learning, allowing scarce cybersecurity staff resources to focus on higher-value tasks.
UEBA and security
Machine learning and artificial intelligence are based on so-called “big data”. Their efficiency and accuracy improve with the amount of data passed to them . The important thing, however, is to collect the right data. This is where UEBA security systems come in. . The combination of accurate and essential behavioral data with machine learning is the strength of this cybersecurity system. This combination allows you to accurately monitor users, providing deep visibility into what they do on a regular basis .
Once a behavior routine has been established, when a user takes actions that the system considers abnormal , a notification is generated. The operations team is thus notified of any action outside the routines defined . If the detected activity is legitimate, analysts can simply label the activity as part of the routine . Machine learning integrates that data into subsequent data analysis for corporate cybersecurity . The crucial step is normalizing behavior , which ensures that that precise action will no longer generate notifications.
Obviously, in the early stages of system installation, the notifications will be numerous . As AI reduces these false positives by “learning”, whenever moves away from normal behavior, l and notifications become more urgent for safety.

The benefits of combining UEBA, machine learning and security
The use of machine learning together with user behavior data provides a level of proactivity to cybersecurity that is not possible when relying on traditional sign-based detection and prevention systems . This is because you are able to detect subtle changes in behavior that are difficult to detect with traditional systems. It is simply not possible to configure a system with every single permutation of rules to detect all attacks.
Detecting low-level reconnaissance activities using UEBA and machine learning is far more likely to trigger your spider senses than other methods. This provides a huge advantage, making it much more difficult for attackers to evade control by flying under any rules-based radar.
The added value
The advantages of using a UEBA security solution built on a machine learning platform for cybersecurity are many. Because their ability to manage network activity routines is refined, not only they can detect abnormal changes in behavior, but this information can become part of a proactive process , identifying and preventing certain behaviors before they occur.
But perhaps most importantly, machine learning is entering the scene at a very sensitive time for cybersecurity. The number of analysts needed to sift through the data by hand and identify threats is exceeding the number of professionals available. Removing the man from a task for which he is not particularly suitable , is free to focus on areas where it can add value, such as further developing cybersecurity protocols.
So, does machine learning add value to cybersecurity? We really believe so.
Costs and proposed solutions
In terms of costs in general, with a UEBA system maintenance is reduced and does not require the hiring of new professionals, especially if you consider the use of the service in SaaS solution.
We at SOD offer the machine learning and UEBA system, together with a SIEM Next Gen in an ideal solution for those who do not want to invest in the installation of dedicated hardware . Our SOC as a Service is designed to optimize your investment and maximize the return in terms of quality of security procedures.
To find out more, visit the service page or contact us to find out how this solution can be useful for your business. We will answer all your doubts.
Useful links:
Useful links:
UEBA: Behavior Analysis Explained
Acronis Active Protection: defense against ransomware
mproving Staff Workflow with Cloud Technology
Estimated reading time: 6 minutes
Despite some seasonal declines, ransomware is still a serious security threat, especially for those who underestimate it . It is often thought that to protect yourself from ransomware it is enough to have a backup copy of your data. This point of view does not take into consideration various aspects. One of them is the relationship between ransomware and NAS ( Network Access Storage ), where you often store a backup copy of the server, thinking it is enough.
Ransomware attacks are capable of rendering entire disks unusable by encrypting the file system . Network disks are at risk, which can also be encrypted, reducing the effectiveness of a backup stored on a NAS.

Definition of Ransomware
Ransomware, as we have seen in other articles, is a form of malware that encrypts the victim’s files. The attacker then demands a ransom from the victim to restore access to data against payment .
Users are shown instructions on how to pay a fee to obtain the decryption key. Costs can range from a few hundred euros to thousands, payable to cybercriminals in Bitcoin.
Once the malware gets executed, it’s almost always too late. In fact, often the victim does not notice until the ransom demand is made or when the entire disk has been completely encrypted.
How ransomware works
There are several ways that ransomware can take to access a server. One of the most common delivery systems is phishing . Some attachments arrive at the victim’s computer in an e-mail message, masked from a harmless file.
Once executed, these software masquerading as harmless files can take control of the victim’s computer, especially if they have social engineering tools built in which trick users into allowing administrative access . Tracing back to the server isn’t as complicated as it might seem.
Some other more aggressive forms of ransomware, such as NotPetya , exploit security holes to infect computers without the need to trick users.
There are several things malware could do once it has taken over the victim’s computer, but by far the most common action is to encrypt some or all of the files it has access to. If you want to get into the technical, here’s more information on how encryption takes place.
The most important thing to know is that at the end of the process, files cannot be decrypted without a mathematical key known only to the attacker . The victim is presented with a ransom note and explained that without a payment, the files will remain inaccessible.
Regardless of the requests and how the ransomware is unleashed in the first place, the thing to note is that there is no data that can be saved. So, if your customers’ data is on a server, they can be involved in such an attack.
If the ransomware encrypts file systems and not just individual files, the problems could multiply.

Ransomware, NAS and backups
One of the ways to mitigate the risk is to have a backup available with which to restore the data without having to surrender to payment. The best practices for management backups do not want there to be backups on the same machine, so it is possible that they are kept on network disks, always accessible from servers. But in fact those disks are part of the machine, as they are accessible.
These disks, called NAS (Network Access Storage), are great solutions for managing files on a network, but they can become as useless as the server in the event of a ransomware attack. If the attack encrypts the file systems, it is possible that finding the remote folders on the NAS encrypts those as well, rendering the backup unusable.
The targets of a ransomware
There are several ways attackers choose which organizations they target with ransomware attacks. Sometimes it’s a matter of opportunity – for example, attackers might target universities because they tend to have smaller security teams and a disparate user base that share many files, making it easier to penetrate their defenses.
On the other hand, some organizations are tempting targets because they seem more likely to pay a ransom quickly. For example, government agencies or medical facilities often need immediate access to their files. .
Law firms and other organizations with sensitive data may be willing to pay to keep news of a compromise hidden , and these organizations are often particularly sensitive to a data exfiltration threat.
However, it has been noted that some ransomware is capable of spreading itself on the network . In fact, no one is completely safe, especially if the data stored on the servers is sensitive.

Ransomware and NAS: how to manage backups
As we have seen, ransomware is no small threat to the data stored on corporate servers. Now let’s see what precautions you can take to protect your data and servers.
Do not use NAS for backups
Se il ransomware arriva a un NAS, quasi certamente lo cifrerà rendendo il backup inaccessibile. Evitare questo problema è facile: usare il cloud!
The server provider should offer the ability to store machine backups on the cloud . This means that the backups are not always reachable by the server and therefore the software is unable to encrypt them.
This is the standard of our VPS service . In case of compromise, in fact, it is sufficient to restore the virtual machine to an earlier state through one of the backups stored in the cloud .
Alternatively, you can backup on premise , ie locally, physically in the company. Using the Acronis Backup service you can perform a backup on an external disk not connected to the network.
Another solution, hybrid of the previous ones, is to create a backup through Acronis and store it in the cloud and not locally. You maintain the advantage of having a remote backup that is not connected to the server constantly.
Preventing attacks
Finally, it is correct to mention that there is another solution, the precautionary solution. With the use of our service SOC and thanks to the use of latest generation analysis systems, it is possible to immediately identify a malware or an attack ransowmare and block it before it does damage.
Whether it is adopting best practices for backup and storing them remotely, or adopting a SOC to protect this aspect and many others in the field of IT security , SOD is available to discuss the situation and find a solution tailored to the needs of your company.
Contact us to ask for information, we will be happy to answer any questions.
Useful links:
Useful links:

Estimated reading time: 6 minutes
As the cybersecurity threat landscape becomes increasingly sophisticated, service providers, such as SOD, need to take additional precautions to protect their customers’ networks. An information management system and monitoring SIEM is an excellent choice in this respect.
This system, in fact, helps mitigate cybersecurity threats from two different angles, all from a single interface . The SIEM monitoring system collects information from multiple sources: network data, threat information feeds, compliance regulations, firewalls, etc. Next, uses that data to power features designed to help IT administrators respond to threat events in real time.

Advantages of SIEM monitoring
In contrast to individual security control systems such as asset management or network intrusion detection, SIEM allows you to dig deeper into security vulnerabilities by unifying information from various systems – even very and offering unprecedented visibility into events occurring in the system.
SIEM is not a threat detection system in and of itself, but enhances the security tools already in use by providing real-time insights to work from . In particular, SOD uses a Next Gen SIEM in a SOAR ( Security Orchestration, Automation and Response ) which also includes advanced behavioral analysis tools ( UEBA ).
If you put high-quality log files into a SIEM tool, you receive high-quality insights into network security . This information can help improve network security protocols.
Unfortunately, many administrators treat SIEM implementation as a solution to be set up and then forgotten. To experience the full benefits of managing information and security events , you need to implement a set of best practices to optimize your solution, starting with security logging.
The logs of a SIEM
How does security monitoring fit into SIEM implementation best practices ? If you look at the SIEM in its main components, it is a log management system .
All the information that a SIEM tool collects is in the form of logs, or records of events occurring within an organization’s IT infrastructure and network.
Examples of logs collected by SIEM include, but are not limited to: Firewalls, routers, wireless access points, vulnerability reports, partner information, antivirus and antimalware.
However, as SIEM tools have a very broad reach and constantly collect log data from all parts of the system, can be a bit complicated and impractical to implement . SIEM best practices help avoid pain points along the line of operation. This way you use SIEM as effectively as possible right from the start.

Best practice
1. Start calmly
The most common mistake made in implementing SIEM monitoring is trying to do too much too soon . Before you even start looking for a SIEM solution, in fact, it is best to define the scope of your SIEM implementation and think about what you want SIEM to do for your network and infrastructure.
We start by isolating the objectives , taking stock of existing security protocols and brainstorming how these protocols fit into the future SIEM implementation. You can also segment anything you want to monitor into groups and define how you want to monitor them. This helps ensure that you have a clear plan for logging.
Once an initial planning has taken place, the SIEM system does not yet have to be implemented across the entire IT infrastructure. It is better to proceed piecemeal.
You should then test the SIEM monitoring solution on a small section of the system to see how it works. Only then are key security vulnerabilities identified that should be addressed immediately and proceed with implementation in subsequent segments.
Setting up SIEM monitoring step by step, rather than running everything right away, will help ensure that logging works in harmony with the rest of the IT section .
2. Think about the requirements
SIEM monitoring can help the company demonstrate compliance with security regulations and audits, but only by knowing what these standards are in advance . Before committing to a SIEM system, you create a list of HIPAA, GDPR, HITECH and any other IT regulations that you need to comply with. The list is then used to compare the required regulations with the solutions that are put into practice.
Not only does this narrow down the list of standards, it will force you to consider how much log data you actually need. Keeping the correct amount to be compliant, also aligns with best practices of SIEM logging and monitoring .
Obviously, the solutions and protocols to follow are not the same for everyone and need to be adapted according to the position of the individual company. For this particular aspect, SOD can help your company both in gathering the information necessary to identify which standards to follow, and in the standards verification once implemented.
3. Fix the correlations
SIEM correlation streamlines its implementation, allowing you to configure the system according to the specific needs of their customers. SIEM works by collecting data from multiple sources and then filtering, analyzing and correlating it to determine if it deserves to be reported as a security alert.
For this it is essential to correlate the rules and set alarm thresholds based on the type of data and their origin . It is important to remember, in fact, that SIEM is designed to find connections between events that would not otherwise be related to each other.
Setting up a SIEM monitoring system is a delicate but fundamental operation to improve the security system for a particular company.
4. Collect data efficiently
Through a SIEM monitoring system it is possible to collect such an amount of data that it could become complicated to manage. It becomes important to choose in a balanced way which data to use in order to optimize the right amount without losing the advantage of having the entire system under control .
Among the data that it is better not to leave out are: Successful permissions and failed attempts, changes to user privileges, application errors and performance problems, opt-in and in general all the actions made by users with administrative privileges.
The following are excluded: information whose collection is illegal, banking information or credit card data, encryption keys, passwords and personal data .
5. Have a plan in case of a detected threat
Choosing the right SIEM solution and employing logging best practices is only part of the job. You need to have an action plan in case of cyber threat .
For the company that relies on a MSSP as SOD, this means making sure that monitoring is only the first part of the service provided. Ideally, SIEM monitoring is the first piece of a well-designed SOAR that puts in place professional operators, alert notifications and a recovery plan in accordance with the type of data put at risk .
In this respect, the SOC as a Service we offer covers most of the eventualities.

Conclusions
Monitoring is a fundamental part of the corporate security system and a SIEM is one of the ways to put it into practice. However, we must not stop at the collection of information, we must know how to treat, enrich and analyze it.
SOD offers comprehensive services that implement SIEM monitoring systems. The implementation obviously implies a “calibration” of the systems and of the correlations between the data in order to always offer the most suitable solution.
If you would like more information about our products, do not hesitate to contact us, we will be happy to answer your questions.
Useful links:
Useful links:
Next Generation SIEM: where are we?

Estimated reading time: 5 minutes
Cyber Threat Hunting is a proactive security search across networks, endpoints and datasets to hunt down malicious, suspicious or risky activities that have escaped detection by existing tools.
Definition
There is a distinction between malware detection and cyber threat hunting . Threat detection is a passive approach to monitoring data and systems to identify potential security problems. However, it is a necessity and can help a threat hunter . Instead, proactive threat hunting tactics have evolved to use new threat intelligence on previously collected data to identify and classify potential risks before the attack .
Security personnel cannot afford to believe that their security system is impenetrable. Must always remain vigilant for the next threat or vulnerability . Rather than sitting around and waiting for threats to strike, cyber threat hunting develops hypotheses based on knowing the behaviors of threat actors and validating those hypotheses through active research in the environment .
With threat hunting, an expert doesn’t start with an alarm or indicators of compromise (IOC), but with deeper reasoning. In many cases the threat hunter’s efforts create and concretize the alarm or the IOC.
This aggressively assumes that a breach has occurred or will occur at the company. Security officers hunt down threats in their environment rather than rely on automatisms.

Threat hunting practice
For companies that are ready to take a more proactive approach to cybersecurity , which tries to stop attacks before they get too deep, adding threat hunting protocols to their security program is the next logical step.
After consolidating endpoint security and incident response strategies to mitigate the now unavoidable known malware attacks, companies can begin to take the offensive . This means digging deep and finding what hasn’t been detected yet. This is precisely the purpose of cyber threat hunting.
As mentioned earlier, threat hunting is an aggressive tactic that starts from the premise of the “assumption of violation”. Attackers are already inside an organization’s network and are secretly monitoring and moving into it.
This may sound far-fetched, but in reality, attackers can be inside a network for days, weeks, and even months . In the meantime, they prepare and execute attacks as advanced persistent threats, with no automatic defense detecting their presence . Cyber threat hunting stops these attacks by looking for covert indicators of compromise (IOCs) so they can be mitigated before the attacks reach their goals.

The key elements of a threat hunting
The goal of the threat hunt is to monitor daily activities and traffic across the network and investigate possible anomalies to find any undiscovered malicious activity that could lead to a complete breach . To achieve this level of proactive detection, threat hunting incorporates four equally important components.
1. Methodology
To be successful in hunt for threats, companies must commit to a proactive, full-time approach that is continuous and evolving. Instead, a responsive, ad hoc implementation, “ when we have time “, will be self-defeating and will only lead to minimal results.
2. Technology
Most companies already have comprehensive endpoint security solutions with automatic detection. Threat hunting works in addition to these and adds advanced technologies . The aim is to find anomalies, unusual patterns, and other traces of attackers that shouldn’t be in systems and files.
The new cloud-native endpoint protection (EPP) platforms that leverage big data analytics can capture and analyze large volumes of non-data filtered on endpoints, while behavioral analytics and artificial intelligence can provide broad, high-speed visibility into malicious behaviors that seem normal at first.
3. Highly qualified and dedicated staff
The threat hunters are a race of their own. These experts know how to use the security technology deployed by companies. In addition, also combine the aspiration to go on the offensive with intuitive problem-solving skills to uncover and mitigate hidden threats.
4. Threat intelligence
Having access to evidence-based global intelligence from experts from around the world (e.g. Miter Att & amp; ck ) further improves and accelerates hunting for existing threats. Hunters are aided by information such as attack classifications for identifying malware and threat groups , as well as advanced threat indicators.

The abilities of a threat hunter
The Threat Hunting Report from Crowd Research Partners confirms the importance of certain capabilities for threat hunting. When asked to rank the most important skill, the survey found that:
69% chose threat intelligence
57% chose behavior analysis
56% chose automatic detection
54% chose machine learning and automated analysis

The profile of a threat hunter
Threat hunters look for attackers who manage to break through vulnerabilities that a company might not even know exist . These attackers spend a considerable amount of time planning and performing the reconnaissance, acting only when they know they can successfully penetrate the network without warning. They also inject and build malware that has not yet been recognized or use techniques that do not rely on malware at all, to provide a persistent base from which to attack.
What does it take to outsmart even the smartest attackers?
A cyber threat hunter is relentless and can find even the smallest trace of what attackers have left behind. In general, threat hunters use their skills to undo the small changes that occur when attackers make their moves within a system or file.
The best threat hunters rely on their instincts to sniff out the stealth moves of the most dangerous attacker.
Are you a threat hunter? Contact us!
SOD is looking for a SOC / ICT analyst to add to the team. If you think you’re the right person, visit this page to view the detailed job posting.
Useful links:
Cyber Threat Intelligence (CTI) – greater effectiveness for IT security
Long-term search: what’s new in the SOCaaS service

Estimated reading time: 6 minutes
Cyber Security is the practice of defending computers, servers, mobile devices, electronic systems, networks and data from malicious attacks. It is also known as Information Technology Security and Electronic Information Security . The term applies in a wide variety of contexts, from business to mobile computing and can be divided into a few common categories.
We can divide cyber security into several areas of interest which I list briefly below. In almost every situation listed, SOD has a dedicated service.
Cyber Security areas of interest
network security is the practice of protecting a computer network from intruders, whether it is targeted attacks or generic malware .
application security focuses on keeping software and devices free from threats. A hacked application may be providing access to data that it was designed to protect. Robust security begins in the design phase , well before a program or device is deployed. This is why analyzing the code of an app is essential before it is released.
operational security includes processes and decisions in the management and protection of resources and data. The permissions that users have when accessing a network and the procedures that determine how and where data can be stored or shared all fall within this scope.
Disaster recovery and business continuity define how an organization is able to respond to a cyber security incident or any other event that causes data loss . Disaster recovery policies dictate how the organization restores its operations and information to return to the same operational capacity as before the event. business continuity is the plan the organization resorts to as it tries to operate without certain resources.

The human part of cyber security
End User Education addresses the most unpredictable factor in cybersecurity: people . Anyone can accidentally introduce a virus into an otherwise secure system by not following security best practices. For example, teaching users to delete suspicious email attachments and not insert unidentified USB drives is vital to the security of any organization .
In this area, particular importance should be given to scams, phishing and in general social engineering, which relies on the element usually more weak computer system: the operator.
The scope of cyber threats
The global cyber threat continues to evolve at a rapid pace, with a increasing number of data breaches every year . A report from RiskBased Security revealed that 7.9 billion documents were exposed to data breaches in the first nine months of 2019. This figure is more than double (112%) of the number of documents exposed in the same period the previous year.
I medical services , retailers and government agencies have experienced the most breaches , with malicious criminals responsible for most accidents. Some of these industries are more attractive to cybercriminals because they collect financial and medical data, but all companies using networks can be targeted for their customers’ data, corporate espionage, or to attack customers .
What governments do
With the scale of the cyber threat set to continue to grow, the International Data Corporation predicts global spending on cyber security solutions will reach a record $ 133.7 billion by 2022 . Governments around the world have responded to the growing cyber threat with guidance to help organizations implement effective cybersecurity practices.
In the United States, the National Institute of Standards and Technology (NIST) has created a cyber security framework , to combat the proliferation of malware code and aid early detection. The framework recommends continuous, real-time monitoring of all electronic assets .
The importance of system monitoring is resumed in the “ 10 steps to cybersecurity “, a guide provided by the UK government’s National Cyber Security Center . In Australia, the Australian Cyber Security Center (ACSC) regularly publishes guidance on how organizations can counter the latest cybersecurity threats.
In Italy we have the national framework for cyber security which provides tutorials, guides and European standards on cyber security .
MSSP and cyber security services
A Managed Security Service Provider (MSSP) provides monitoring and management in outsourcing for security devices and systems. In practice it takes care of all cyber security measures for the company requesting the services.
SOD is an MSSP and the services offered include protection and monitoring of various sectors of the corporate IT department.
Our verification services include vulnerability and penetration testing , as well as the analysis of safety procedures . With the SOC as a Service service we provide the potential of a Security Operation Center , relieving the company of installation and management costs. The SOC adopts latest generation technologies such as SIEM Next Gen and UEBA , which introduce analysis by an AI for motoring logs and users .
SOD uses security operations centers to provide 24/7 services designed to reduce the number of operational personnel that a company must manage, while still guaranteeing levels of cyber security excellent.
But defense fronts don’t stop at software and machines, must also include the most unpredictable element: the end user . That’s why our offer for companies also includes people-oriented services, as we will see shortly.

End user protection
End user protection is a crucial aspect of cyber security . After all, it is often the end user who accidentally loads a malware or other form of malware on their device .
As suggested earlier, the security protocols set up by SOD analyze software in real time. Through behavioral analysis systems we can monitor both the behavior of a software and the user . In the case of an attack based on lateral movement , for example, abnormal accesses and requests by a user can be indicators of an attack in progress.
But we don’t stop there, we can test the company against techniques of social engineering , phishing and physical tampering. Thanks to the ethical hacking services and consequent report, we are able to identify the company’s weak points and suggest effective strategies to mitigate the risks. In the case of phishing, we also organize ad hoc training based on the weaknesses highlighted in the report.
Through the physical security service, in addition to the IT vulnerability testing services, we put ourselves in the play the bad guys and try to carry out physical attacks . For example, we try to enter corporate buildings that should be protected, we try to reach network infrastructures and install potentially harmful hardware, etc.
Thanks to a team of ethical hackers and trained and trained operators, we test every aspect of cyber security before a risk becomes a problem .
If you want more information about our services or have any questions, don’t hesitate to contact us.
Useful links:

Estimated reading time: 9 minutes
Spam seems to reach every single email account we use , no matter how careful we are or what the address provider is. How do spammers get all of our email addresses? Can we do something to hide our email address from common spammer techniques?
Unfortunately, there’s not much you can do to stop spammers from bombarding you with emails. There are some tips that will help protect you, but spammers will probably find your email address anyway .
The problem is not so much the unwanted advertisement message, but rather what it means that you received a message. How did you react? Did you delete it? Did you click on any links? Have you flagged it as spam? Any action could bring useful information to attackers without you noticing.
Let’s face it more clearly and start with a question: where do spammers find our e-mails?
Spammer techniques for retrieving e-mail addresses
Nobody gives their email to a website and expects it to end up in the hands of a scammer. Yet it’s not uncommon for someone to find their inbox full of unsolicited spam emails.
Stolen databases
The simplest of the techniques spammers use to collect large lists of active email addresses is through stolen account databases. These password thefts happen with frightening regularity. Companies like Adobe, LinkedIn, eHarmony, Gawker, Last.fm, Yahoo !, Snapchat and Sony have all been compromised in recent years .
Leaked databases are normally considered a security threat because they often display account names and passwords. However, generally show email addresses as well. Spammers can download these leaked databases and add the millions of email addresses to their lists . Spammers know that most of these email addresses should be active , so these databases are excellent for them.
This is probably how most spammers are finding email addresses to send spam. There really isn’t much you can do to protect yourself from a spammer who gets your address this way.
A site like Have I been pwned? can tell you if the information of your account may have been spread .
You can protect yourself from password theft by using different ones, unfortunately, you must always use the same email address everywhere , it would be unthinkable to have an address for each service used.
Link in mail messages
If you receive spam emails, you should avoid clicking on the links in the email . If you find an “Unsubscribe” link in an email from a legitimate company, it’s probably safe to click it. A real company doesn’t want to spam and potentially run into anti-spam laws, so they will simply remove you from their list.
However, if you see an “Unsubscribe” link (or, even worse, a “Buy Now!” link) in an email that looks very unprofessional and scam, the spammer will not necessarily remove you from his lists .
This is where things get more complex. They will notice your click and their systems will identify your email address as active . They know you’re there, and you may see larger amounts of spam after clicking the link.
The same goes for uploading images in spam emails. Do not click the “Upload images” button, or spammers will know that you have opened the email . Even if you don’t see an image in the message, there may be a small tracking pixel that allows the spammer to identify you if you upload the asset.
This is why most email clients don’t automatically upload images.

E-mail scraping, search for unencrypted e-mails on the net
Another spammer technique to retrieve addresses from the network is to scrape them ( scraping ) from the unencrypted data on the network. There are software out there that read files on the net and find those that contain e-mails and save them. A bit like Google’s crawlers do when they crawl a site, but with malicious intent.
You may have seen a comment where someone leaves their address to be contacted. The bot that scans the network will save similar addresses.
The spammer adds this address to his spam lists et voilà , spam is served . This is why eBay provides a temporary email address where you can be reached rather than including your real email address. This technique is probably less common now that spammers have huge leaked account databases to work with.
Spammers can also try to acquire valid email addresses by browsing other places that are publicly available, such as whois records for a domain . These records show an email address associated with the person or organization that registered the domain name.

Purchase of email addresses
Another spammer technique, definitely for lazy hackers, is to buy addresses from databases that provide them.
Unscrupulous people sell email lists to spammers for a low price. These addresses were often distributed on CD in the past , and may still be, but the leaked account databases have probably eliminated some interest in this market.
Spammers can also simply exchange their mailing lists with each other, making sure other bad guys get their hands on your address once it happens the first time.
Please be aware that this technique is not entirely illegal. When we subscribe to a service, we often have the possibility to provide our e-mail address to third parties for advertising purposes. Some users accept without reflection and without verifying whether it is an obligation to subscribe to the service or not. .
I personally happened to be contacted by a person who, with no intent to spam, but to make up the number, had bought my address from a contact resale agency, divided by areas of interest. If he had been a spammer, he could have used a similar service.
How to protect your address
Spammers can also obtain email addresses in other ways but the methods listed above are some of the most common.
There isn’t much you can do to prevent your email address from being leaked and receiving spam.
- – you can avoid putting your e-mail address on the web in plain text form
- – never click on a link
- – don’t upload a image in a suspicious email.
However, your address will almost certainly end up in the hands of a spammer at some point.
Actually, you don’t have to worry so much about whether the address is in circulation, but about how the address is used, especially if it is active.
Spammer techniques of using addresses
Once a scammer obtains your email address, it is very likely that they will use it to take advantage in any way possible . The better he is, the greater the risks.
Many will send you spam emails, with the hope of collecting private information such as credit card numbers . They will try to trick you into believing that you have won something, or that they have a profitable item for sale. Hackers may also use your email to steal your identity and send messages to your contacts . Remember the techniques of Zombie Phishing ?
Other scammers will use your personal information to try to access your other accounts . Most people reuse the same passwords for different accounts, which means that hackers who have access to one account can easily infiltrate the others.
This is why using the same passwords around the web is highly discouraged and not secure at all.
Create botnets
One of the reasons why you should never actively interact with spam messages is that interactions send hackers an important piece of information: the address is active, someone uses it on their device.
An active address, once discovered, is a perfect target for more specific attacks than phishing , and since all addresses are at risk, even corporate ones, from phishing you can easily get to a double extortion ransomware .
In the latter case, the threat of a DDoS attack may already come from mentioned zombie phishing technique, and it could all have started with some spam message.
The computers that will basically send requests to the server to perform the DDoS attack could themselves be part of a botnet created as a result of techniques used by spammers .

Phenomenology of an attack
As a first spammer technique, company addresses are retrieved . This can be done through scraping or database buying on the dark web. Next, to check which addresses are active , a couple of spam campaigns are sent. Nothing harmful, fake newsletters with an obvious Unsubscribe message, or a tracking pixel.
Note: A tracking pixel is usually a very small transparent image that is uploaded from a remote server. Just check how many times it has been downloaded and by whom to understand which addresses are active and which are not .
As a result, the contact database will have shrunk to a list of active addresses , in which users have been inattentive enough to click on a link from a suspicious email.
Finally, to these selected addresses, is sent a real phishing message containing malware or a request to intervene on a seemingly legitimate web page . For example, the request to reset your credentials via the attached link.
The unsuspecting user, thinking he is doing a safe thing, follows the link, enters the credentials and gives them to the spammer . At this point the attacker has gained access to an account. From that moment on, the risks are much more and much more damaging.

How to defend against spammer techniques
Let’s take a few steps back. The whole chain of events that led the hacker to gain access to an important account went through spam and phishing messages.
Ethical Phishing
In some of the passages, the attack could have been avoided . The ability to recognize a suspicious message and then ignore it is the first weapon available to a user. SOD can help your business with this .
Through a ethical phishing service, we first test the resilience of users . Once any weak points have been identified, a training course ad hoc is constructed to provide adequate proactive defense tools to all employees.
SOC as a Service
Not always being aware users is enough , and a careless mistake could cost a company a lot of sensitive data. For this reason, we can also implement a service SOCaaS for the mitigation of risk and damage following an attack.
In this scenario, a system consisting of next generation SIEM and protocols UEBA implemented by an artificial intelligence, they monitor the network in search of any anomaly . Any suspicious behavior is identified and analyzed by technicians to see if it can actually become a threat or not.
If you would like more information on how SOD can help you raise your company’s cybersecurity level, don’t hesitate to contact us.
Useful links:

Estimated reading time: 6 minutes
Out of nowhere, someone replies to an email conversation dated months ago. This is a real conversation that actually happened. Maybe it’s about a meeting, a job opportunity. This email seems very relevant, but beware, it could be zombie phishing .
Indeed, something is wrong, the topic discussed has been over for months and now there is a strange error message in the body of the email. This is a sneaky tactic: revive a long dead email conversation.

Not the usual phishing
The Cofense ™ Phishing Defense Center ™ (PDC) spotted a large Zombie Phishing campaign in 2018. The scam , like almost any phishing attack, is carried out through compromised email accounts.
Scammers take over an email account and respond to long-closed conversations with a phishing link or malicious attachment (e.g. malware or a keylogger ) . Since the email subject is usually relevant to the victim, a curiosity-driven click is very likely to occur . In fact, let’s not forget that the original conversation was already present in the messages received, it is easy to think that it is a follow up or similar.
These Zombie Phishing attacks appear to use automatically generated infection URLs to evade detection. No two links are alike, and they are hidden behind “error” messages without too many frills in the body of the message. This scenario provides a pattern of apparent legitimacy for the users who are victims.
The zombies in computer science
In the computer industry, a zombie is a compromised computer connected to the network. The compromised state could be due to a hacker, virus, malware, or trojan horse .
The infected machine performs malicious tasks under a remote direction. Zombie computer botnets are often used to spread email spam and launch denial-of-service (DoS) attacks.
Types of attack
Here are some observed patterns of Zombie Phishing carrying malicious links . A distinguishing factor was the use of two distinct graphic templates containing button or link error messages.
The message reads something like “Incomplete message” or “Inability to show the whole message”. The link or button invites you to click to see the original message. Obviously the click only involves the installation of a malware or other similar events . Note that no two identical links have been identified, a sign that probably a bot was generating the addresses.
Another common factor is the use of domains with the .icu TLD. This is probably a factor that varies considerably over time. Here are some of the domains found in the first analysis of 2018:
These zombie phish attacks have been observed to use official organizational logos to add legitimacy to the fake login pages. A common practice in phishing techniques that we have already seen in other articles.
Landing pages are designed to look like a legitimate online portal, including a company logo and even a favicon. In these cases the ultimate goal is the theft of the victim’s credentials .
Furthermore, any victim who visits the malicious website is “tagged” using the host’s IP address as an identifier and, after entering the credentials, is directed to the same spam website seen by other victims. This is often done via obfuscated links using URL shorteners (such as hxxps://href[.]Li/).
If the same host tries to visit the phishing link again, the fake login page is skipped and you are forwarded directly to the spam page. This markup and URL shortener obfuscation helps attackers keep a low profile and continue their campaign unabated.
Conversation Hijacking

The conversation hijacking tactic is by no means new and is now living a new life with zombie phishing . Scammers have hijacked compromised email accounts to distribute malware and phishing emails as replies to conversations that have been concluded for years now.
This technique is still popular because it makes victims much more likely to click on links and download or open files. The threshold of attention against classic phishing attacks is lowered when messages are brought into conversations already in their inbox .
A couple of years old example of this was the botnet Geodo . Basically it is insertion into existing email threads ( conversation hijacking ) to deliver malicious documents. These, in turn, download a sample of Geodo or other malware such as Ursnif , which according to Key4Biz was the most widespread in Italy in June 2020.
However, the effectiveness of this tactic can greatly depend on the content of the conversations . A reply to an automated advertising email is less likely to cause an infection than a reply to a help-desk support thread.
There have been several Geodo zombie phishing campaigns consisting of replies to automated advertising emails. This is an indication that, in some cases, campaigns consist of indiscriminate replies to all emails in a mailbox. Since the volume of these conversation hijacking is still relatively low, the small reach of these emails is probably limited by the number of ongoing conversations .
Certain account types are therefore more likely to attract the direct attention of threat actors and induce them to invest additional effort and time in developing unique phishing campaigns for those accounts.
Defense from zombie-phishing
Here are some quick tips to avoid losing your credentials in a Zombie Phishing attack:
- Beware of email subjects that may seem relevant but come from old conversations
- Beware of any error message in the body of the message
- Don’t trust attached documents just because they’re replying to a conversation
- Hover your mouse over buttons or links in suspicious messages to check for suspicious domains
It has been observed that these campaigns have gotten smarter . To combat this and other forms of phishing, employee training is key.
A properly trained workforce is what it takes to defend your organization against Zombie Phishing attacks.
SOD offers a full service in this regard . We begin by attacking the company in a controlled manner, testing any weaknesses in employee safety or behavior. Subsequently, specific training is designed to remedy the gaps and fully train the staff.
To keep defenses high, our SOCaaS includes the analysis of user behavior, logs of connected machines and the network in a to immediately identify phishing attempts.
Useful links:

Estimated reading time: 10 minutes
Social engineering is the term used for a wide range of malicious activities performed through human interactions. It uses psychological manipulation to trick users into making security mistakes or provide sensitive information. Then, with that information, the hacker is able to successfully carry out targeted attacks, such as data theft, a ransomware or a ‘ interruption of services.
Social engineering attacks usually occur in stages . The perpetrator first investigates the intended victim to gather the necessary background information , such as potential entry points and weak security protocols, required to proceed with the attack. Then, the attacker moves to gain the victim’s trust and provide incentives for subsequent actions that violate security practices, such as disclosing sensitive information or granting access to critical resources.
What makes social engineering particularly dangerous is that it relies on human error rather than vulnerabilities in software and operating systems . Mistakes made by legitimate users are much less predictable, making them more difficult to identify and thwart than a malware-based intrusion.

Note that the target of a social engineer is not necessarily a network or software . Being able to enter a building evading security, and then installing a device or stealing documents, are actions that still fall under this type of attack.
The techniques of social engineering
Social engineering attacks come in many different forms and can be carried out wherever human interaction is involved . The following are five most common methods of digital social engineering attacks.
Baiting (from “bait”)
As the name suggests, baiting attacks use a false promise (a decoy , indeed) to whet the victim’s greed or curiosity. They lure users into a trap that steals their personal information or installs malware on their systems.
The most infamous form of baiting uses physical media to disperse malware . For example, attackers leave the bait (typically infected keys) in conspicuous areas where potential victims are certain to see them (e.g. bathrooms, elevators, the parking lot of a targeted company). The decoy has a legitimate look, like a label indicating the content, like the company’s payroll. The clue that reveals what it should contain may change, of course, but has the potential to be potentially very interesting .
Victims pick up the bait out of curiosity and insert it into a work or home computer, resulting in automatic installation of malware on the system.
Lure scams don’t necessarily have to be done in the physical world. Forms of online baiting consist of enticing advertisements leading to malicious sites or encouraging users to download a malware-infected application. Here it leads to the phishing techniques, which we will see shortly.
Defense notes : to defend against these social engineering attacks, as well as paying close attention to what is connected to your computer, it does not hurt to have an efficient antivirus and anti-malware system. For the company, a new generation SIEM system and UEBA help in detect suspicious user behavior and greatly reduce the risk of malware infection.

Scareware (from “to scare”)
Scareware consists of bombarding victims with false alarms and fake threats . Users are tricked into thinking their system is infected with malware, prompting them to install software that has no real benefit (other than the perpetrator) or is malware itself. Scareware is also called deception software ( deception software ), rogue scanner software and fraudware .
A common example of scareware is the legitimate-looking popup banner that appears in your browser as you browse the web , displaying text such as “ Your computer may be infected with spyware programs harmful “. In other cases, the popup offers to install the tool (often infected with malware) for you, or directs you to a malicious site where your computer is infected.
Scareware is also distributed via spam email which distributes bogus warnings, or offers users to buy useless / harmful services. Social engineering is often very imaginative and manages to find ever new ways to deceive. Always be alert.
Defense notes : In case you suspect that the received message is really legitimate, it is best to seek a solution actively , i.e. without using the links suggested by the message same. For example, we received a message from a service announcing that our account has been compromised. If in doubt, you can contact the support of the service directly from their site to ask for clarification. Avoid using the links suggested by the suspicious message at all costs .

Pretexting (from “to pretend”)
In this social engineering attack, an attacker gains information through a series of cleverly constructed lies . The scam is often initiated by an perpetrator who pretends to need sensitive information from a victim in order to perform a critical task.
The attacker usually begins by establishing trust with his victim by impersonating colleagues, police, bank and tax officials, or others who have a right to know authority . The hacker asks questions that are apparently necessary to confirm the victim’s identity, through which he collects important personal data.

Many types of information are collected using this technique, such as identity card numbers, personal addresses and telephone numbers, telephone records, staff vacation dates, bank records, and even security information relating to a physical facility.
Any information, however harmless it may seem, could later be used for a second attack. Even the name of a security guard hired by the company could already be enough to build trust and ask for a tear to the rule when asking for the access code to automatic doors.
Phishing (from “to fish”)
As one of the most popular types of social engineering attacks, phishing scams are email and text message campaigns that aim to create a sense of urgency , curiosity or fear in the victims . Then it prompts them to reveal sensitive information, click links to malicious websites, or open attachments that contain malware.
An example is an email sent to users of an online service notifying them of a policy violation that requires immediate action on their part, such as a mandatory password change. Includes a link to a website, nearly identical in appearance to its legitimate version, which prompts the user to enter their current credentials and new password . After submitting the form, the information is sent to the attacker.
Since identical, or nearly identical, messages are sent to all users in phishing campaigns, detecting and blocking them is much easier for mail servers that have access to threat-sharing platforms.
Defense note : While it is true that in some cases we have become accustomed to not giving weight to these kinds of messages, it is also true that social engineers have become increasingly clever. There is no need to let your guard down. Instead, it is very useful to always be wary of messages that require credentials.
These attacks leverage the fact that it’s easy to fool some users, whether out of distraction or naivety. The best defense is employee training through a ethical phishing service and subsequent targeted training.

Spear phishing (from “spear, and “to fish”)
This is a more targeted version of phishing in which an attacker chooses specific individuals or businesses . They then tailor their messages based on their victims’ characteristics, job positions, and contacts to make their attack less obvious. Spear phishing requires a lot more effort from the author and can take weeks and months to complete. They are much harder to detect and have better success rates when done skillfully.
A spear phishing scenario could involve an attacker who, impersonating an organization’s IT consultant, sends an email to one or more employees. It is worded and signed exactly as the consultant normally does, thus fooling recipients into thinking it is an authentic message. The message prompts recipients to change their password and provides them with a link that redirects them to a malicious page where the attacker now captures their credentials.

How to defend against social engineering attacks
Social engineers manipulate human feelings, such as curiosity or fear, to carry out patterns and lure victims into their traps. Therefore, it is essential to be cautious whenever you feel alarmed by an email, attracted to an offer displayed on a website, or when you come across digital media wandering around. Being alert can help protect you from most social engineering attacks that happen online.
Additionally, the following tips can help you improve your vigilance in relation to social engineering attacks.
- Do not open emails and attachments from suspicious sources . If you don’t know the sender in question, you don’t need to reply to an email. Even if you know them and are suspicious of their message, cross-check and confirm the news from other sources , such as over the phone or directly from a service provider’s website. Even an email that appears to come from a trusted source may have been initiated by an attacker.
- Use multi-factor authentication . One of the most valuable pieces of information attackers look for is your user credentials . Using 2-factor authentication helps ensure the protection of your account in case of system compromise. There are free applications for all types of mobile devices that allow you to implement this type of authentication.
- Be wary of attractive offers . If an offer seems too tempting , think twice before accepting it as real. Use Google to check the topic and quickly determine if you are dealing with a legitimate offer or a trap.
- Update your antivirus / antimalware software . Make sure automatic updates are turned on. Check periodically that updates have been applied and scan your system for possible infections.
If your company has an IT department, these recommendations should be standard security measures.

Security services for companies
When you think about the data that your company holds and manages, you are never too cautious in defense. Social engineering relies on the fact that an employee hacks more easily than a computer , which is often true.
In addition to the cyber protection measures listed above, it is good that all employees are aware of the risks and potential threats.
SOD offers a series of services that go in this direction. The first and perhaps most important is ethical phishing in which we try to attack the company with phishing techniques . We find out what the weak points are and organize internal training to provide the right tools for staff.
We also have the classic Vulnerability Assessment and Penetration Test for testing cybersecurity systems. Addons are applicable to this service to cover a greater number of areas. There is a specific addon for app analysis and code review , but also one where we try to hack the company with physical attacks . We will test the physical security of the company, the ability to enter buildings, access to network controllers and more.
Finally, to keep networks under control, the SOCaaS service allows you to monitor the entire network, identify suspicious actions (with behavior analysis via artificial intelligence), unauthorized installations, breach attempts and much more.
Data security in the company is really important, contact us to find out how we can help you!
Useful links:

Estimated reading time: 5 minutes
A Zero-Day attack (also known as 0-day) exploits a software vulnerability unknown to security officers and the software vendor. Hackers can exploit the weakness, as long as it is not mitigated, through Zero-Day exploit or, indeed, attack.
The term “zero-day” originally referred to the number of days after the software was released. A “zero-day” software, therefore, meant a program obtained by forcing a developer’s computer before release. The term was then applied to the vulnerabilities that this practice allows to exploit. Once the vendor becomes aware of the vulnerability, they usually patch or recommend solutions to mitigate it.
Software vulnerabilities
Software often has vulnerabilities. These are unintentional flaws, or code problems that could hypothetically be exploited.For example, there may be a flaw that allows a cybercriminal to access otherwise secure data. Programmers are often on the lookout for these vulnerabilities and when they discover them, they analyze them, produce a patch to fix them, then distribute that patch in a new version of the software.
However, this is a time-consuming process. When the flaw becomes known, hackers around the world can start trying to exploit it.
Zero-Day Attack
If a hacker manages to exploit the vulnerability before the developers find a solution, this exploit then becomes known as a Zero-Day attack.
Zero-day vulnerabilities can take almost any form, because they can manifest themselves as any type of vulnerability in software. For example, they can take the form of missing data encryption, SQL injection, buffer overflows, missing permissions, bugs, or problems with password security.
This makes these vulnerabilities difficult to find before they are exploited in zero-day attacks. This, in some ways, is good news: it also means that hackers will have a hard time finding them. But also that it is difficult to defend against these vulnerabilities effectively.
How to protect yourself
We have seen how difficult it is to protect yourself from the possibility of a zero-day attack, because it can take many forms. Almost any type of security vulnerability could be exploited as a zero-day if a patch is not produced in time. Also, many software developers intentionally try not to disclose the vulnerability publicly in the hope that they can distribute a patch before any hacker discovers the vulnerability.
There are a few strategies that can help you defend your business against zero day attacks:
Stay informed on Zero-Day attacks
Zero-day exploits aren’t always advertised, but occasionally we hear about a vulnerability that could potentially be exploited. If you stay tuned to the news and pay attention to releases from your software vendors, you may have time to put security measures in place or respond to a threat before it is exploited. A good way to do this is to follow your suppliers’ newsletters. At the bottom of this page you will find the form to subscribe to the SOD one.
Keep your systems up to date
Developers are constantly working to keep their software up to date and secure to prevent the possibility of exploits.When a vulnerability is discovered, it is only a matter of time before they produce a patch. However, it is up to you and your team to make sure your software platforms are always up to date. The best approach in this case is to enable automatic updates, so that the software is updated routinely, and without the need for manual intervention.
Use additional security measures
Make sure you’re using security solutions that protect you from a zero-day attack. SOD offers a solution that includes a set of tools that allow you to raise your defenses significantly. SOCaaS is a real security operations center for your company. Using state-of-the-art tools such as SIEM and UEBA and thanks to granular control over the monitored network, every attack attempt is identified in the shortest possible time.
Each type of data produced by the interconnected systems in the infrastructure is collected, normalized and analyzed for anomalies. This means that not only are you checking for known indicators of compromise (IOC), but suspicious operations and behavior of facility users are also monitored. In this way, it is also possible to identify attack attempts that are normally very difficult to detect, such as those involving Zero-Day Attacks, but not only. In fact, through the SOCaaS service, it is possible to identify compromised accounts, the violation of protected data, lateral movement attacks, phishing, etc.
The security of a company’s IT system is a very important topic that we care a lot about. The compromise or loss of sensitive data can cost a lot from both an economic and a reputational point of view. Do not neglect this important aspect for the safety of your business, contact us to tell us about your situation, we will be happy to show you how we can help you.
Useful links:
Vulnerability Assessment and Penetration test
Protecting a site in WordPress: security package
Long-term search: what’s new in the SOCaaS service
Contact us

The IT world continues to evolve and the same goes for industry acronyms. One of these is the term MSSP which, in a sense, is the evolution of MSP. The two abbreviations mean: Managed Service Provider (MSP) and Managed Security Service Provider (MSSP). The latter, in general, could be considered as an organization that provides outsourced security services to other organizations. This definition is very vague and somewhat obvious. So what is an MSSP?
Definition: what is an MSSP?
An MSSP offers Security-as-a-Service, ensuring that organizations, end users and systems have the security, protection and compliance with the necessary compliance requirements. In reality, MSSPs have been around for a while, but have recently gained more attention and focus as the cybersecurity landscape continues to evolve rapidly. End users are more aware of the threats and consequences they face if they are not proactive.
MSP
Let’s take a step back, let’s examine what an MSP is, to better distinguish it from an MSSP. In simple terms, a managed service provider (MSP) is an organization commissioned by a customer to perform various IT services. MSPs typically partner with their clients for annual or multi-year periods, receiving recurring income for ongoing services.
An MSP can help a client at any stage of their IT cycle, including:
– the creation of policies and programs
– discover potential solutions
– implementation of solutions
– performance monitoring
MSPs can also manage ongoing IT services, such as updating systems and making configuration changes to suit business needs. These line-of-service elements can include help desk support, network and application management and monitoring, hardware repair, and more. These services are generally outlined and agreed upon in a Service Level Agreement (SLA).
MSSP
What is it that distinguishes MSSPs from MSPs? The extra “S” in MSSP indicates that these are more security focused than a typical MSP. While MSPs often offer other IT services and something related to security, MSSPs focus solely on security. However, even in this case, they could include a fairly large set of services in addition to security.
For example, the MSSP technology offering may include the implementation, configuration and / or management of the following technologies:
– Intrusion Prevention Systems (IPS)
– Filtering of web content
– Anti-virus, anti-spam, firewall
– VPN
– Vulnerability scanning
– Patch management
– Data loss prevention
– Information on threats
In addition, MSSP services may include:
– Risk assessment and gap analysis
– Policy development and risk management
– Search for the solution
– Search and requisition of solutions and tools
– Implementation of the solution
– Management of security systems
– Configuration management
– Security updates
– Reporting, review and compliance
– Training and education
An MSSP may offer a broad and generalized range of security capabilities and services, or it may specialize in one or a few areas of interest. Another thing that differentiates between MSP and MSSP are the NOCs and SOCs.
MSPs often establish their own network operational network (NOC) from which they monitor and administer customer operations, MSSPs instead establish a security operations center (SOC), which is responsible for protecting the infrastructure (networks, applications, database, server, etc.).
Why choose an MSSP?
Now that we know what an MSSP is, we need to understand why such a service should be chosen.
The reason is to be found in the digitalization of the business, which is the biggest driver of company growth in recent years. As companies become more and more interconnected through technology, the opportunities grow, but with them so do the security threats. In this case, executives and boards of directors are looking to transform their companies into power centers of the digital age and are taking a closer look at their position on security.
But this is where things get real: the solutions are complicated, and building your own cybersecurity department 24/7 takes time, money and people. On the other hand, a single data breach can seriously damage the value of your company and cost you a considerable economic loss.
This is why outsourcing your company’s entire IT security solution to a Managed Security Service Provider (MSSP) is an increasingly common decision. This cybersecurity-as-a-service model is popular with businesses, regardless of size. This is because cyber defense is becoming so complex and takes so long that companies have no choice but to outsource security services to follow best practices.
We at SOD provide exactly this type of security services, through various modalities. In addition to the typical services of an MSP, such as VPS, Super Cloud, etc., we are able to cover every need for corporate security through our SOCaaS which implements various solutions including UEBA, SIEM, Vulnerability Assessment & Penetration Test, Active Protection, Log Management, IT Monitoring Service, Management Services, GDPR and Privacy.
If you are interested in knowing how SOD can help your company in improving applied cybersecurity, you can get in touch with us, we will be happy to answer questions and propose a solution suitable for the situation.
Useful links:
Next Generation SIEM: where are we?




SIEM has existed for quite some time, but it is not yet well understood. Also, the fact that technology has evolved significantly in recent years doesn’t help shed some light. Today we see where we are, trying to understand the Next Generation SIEM and the managed systems offered as services that make use of the latest generation SIEM (SOCaaS, for example). Let’s see what all this means for companies.
Being a fundamental part of the SOCaaS offered by SOD, it seems appropriate to explain in detail what a Next Generation SIEM is and what its functions are.
A brief history of SIEM
Before examining what a Next Generation SIEM is, it is right to briefly review the history of this technology and its beginning.
The term Security Information and Event Management (SIEM) was coined in 2005 by Mark Nicolett and Amrit T. Williams of Gartner. The word is the merger of Security Event Management (SEM) and Security Information Management (SIM).
Its original definition given by the creators of the term is: a technology that supports the detection of threats and the response to security incidents, through the collection in real time and historical analysis of events from a wide variety of sources of contextual data.
SIEM was born out of the need to address the huge number of alarms issued by intrusion prevention systems (IPS) and intrusion detection systems (IDS) that were overwhelming IT departments. By helping organizations aggregate events and better analyze those within the network, SIEM has helped organizations improve threat detection. It has also led organizations to take a more proactive approach to security. Preventive security technologies are no longer sufficient on their own.
The difficulties of SIEMs in the early years
Eager to improve their cybersecurity situation, many enterprise-wide organizations have rapidly adopted SIEM technology. Over the years, however, inherited problems have emerged from the past:
1. The datasets were inflexible, so some SIEMs were unable to process the required data, which meant their effectiveness was limited
2. They were difficult to maintain and manage, which added complexity and drained staff resources
3. SIEMs produced a high number of false positives, creating even more work for the security teams
4. With the advancement of technology, SIEMs have struggled to keep up with the evolution of threats and therefore the IT risk for companies has grown
The Next Generation SIEM arrives
Many advanced threats are now polymorphic rather than static. That is, they are able to constantly modify their behavior to evade detection. As such, Next Generation SIEM systems must not only process more data, but also become much more capable of recognizing new patterns within them.
Given the difficulties and limitations of inherited SIEM systems, many thought they would disappear over time. But this did not happen, SIEM still remains a key technology used by companies. However, technology has had to evolve.
While SIEM once relied on only a handful of data sources, the “Next Generation” of SIEM systems was developed to process a greater volume and variety of data, as well as correlating it in a timely fashion.
Gartner reported that the SIEM market is continuously growing. One reason for this growth is that Next Gen SIEM systems are now used by midsize organizations, not just large enterprises.
What are the capabilities of Next Gen SIEM?
Next Gen SIEMs, sometimes referred to as analytical SIEMs or SIEM 3.0, have brought new capabilities to organizations and their security teams.
– Allow faster integration into a corporate infrastructure through an open architecture to cover cloud, on-premise and BYOD resources
– Include real-time visualization tools to understand the most important and high-risk activities
– Use scenario and behavior analysis to “photograph” well understood scenarios and highlight significant changes in behavior
– Integrate and use Threat Intelligence information from customized, open source and commercial sources
– Provide a flexible framework that allows for the implementation of a tailored workflow for key organizational use cases
– Measure status against regulatory frameworks (e.g. PCI DSS) for prioritization and risk management
Security Orchestration, Automation and Response
Security Orchestration, Automation and Response (SOAR) is a growing security area that Next Gen SIEM vendors are exploiting to contribute and take advantage of the latest features. In its essence, SOAR has two fundamental aspects:
1. It allows to bring more data to a Next Gen SIEM for analysis
SOAR is helping SIEM technology to become smarter and big data oriented, thus enabling security teams to make faster and better informed decisions. Broader intelligence means more reliable threat identification and fewer false positives.
2. Help automate incident response
Another important way SOAR is influencing the evolution of SIEM Next Gen is to help standardize incident analysis and response procedures. The goal is to partially or completely automate response activities in order to reduce the potential harm and inconvenience that breaches can cause. Such response activities could include blocking compromised user accounts and blocking IP addresses on a firewall.
By automating routine actions, SOAR helps security teams become more efficient and frees them up time to focus on threat hunting and patch management.
User Behavior Analysis (UEBA)
Another important feature of Next Generation SIEMs is the use of User and Entity Behavior Analytics (UEBA). UEBA does not track security events or monitor devices, but instead focuses on monitoring and analyzing the behavior of an organization’s users.
UEBA can be extremely useful in helping organizations identify compromised accounts, as well as insider threats. It works using advanced machine learning and behavioral profiling techniques to identify anomalous activity such as account compromise and abuse of privileges. By not using rules-based monitoring, the UEBA is more effective in detecting anomalies over time.
The challenges for a modern SIEM
Despite unquestionable advances in detecting complex cyber threats, SIEM Next Gens can still, if not used and maintained properly, generate a large number of alerts. For organizations without IT resources and dedicated security personnel, researching these alerts to distinguish true network security problems from false positives can be extremely complex and time-consuming.
Even when real threats are identified, knowing how to respond to them can be just as challenging.
Getting the most out of SIEM to help address growing security challenges will also depend on better trained personnel who can use the systems more effectively and validate alarms. For organizations that lack in-house knowledge or skills, it therefore makes sense to work with an external vendor who can cover or augment security capabilities.
A full SOCaaS service, including Next Generation SIEM and UEBA for threat hunting, is the ideal choice. Not only does it save time in terms of validating and checking alarms, but also in economic terms, not having to face installation costs and staff training.
If you are interested in learning more, do not hesitate to contact us, we will answer your questions.
[btnsx id=”2931″]
Useful links:
Security: Pentest and verification of vulnerabilities
What is a Network Lateral Movement and how to defend yourself
Is SOCaaS useful for your business?
Computer network security: PT vs. VA
SIEM in computer science: history
SIEM software: what it is and how it works

A SIEM solution in IT is one of the essential components of a SOC (Security Operation Center). Its task is to collect information and analyze it in search of anomalies and possible breaches in the system. But the defense process hasn’t always been that simple. What we now call SIEM, Security Information and Event Management, is the union of two different types of cyber security tools.
SIM and SEM: the origins
Before the arrival of a complete SIEM solution in computing, security was heavily focused on perimeter security and did not keep the internal network adequately controlled. The first solutions developed in the 90s were basic and basically dealt with security information management (SIM) or security event management (SEM). They were solutions available as tools that had to be deployed on-site in the data center to be protected. This limited scalability, because adding capacity required the purchase of additional equipment.
These early solutions were also built on proprietary databases that forced customers to use technology from a single vendor. If you wanted to move your data to another system, the process was long and complicated. It should also be noted that archiving was more expensive, so only the most valuable data was collected. Furthermore, although the SIM and SEM solutions contained all the data necessary for the defense, the search and alarm were rudimentary. Additionally, they depended on experienced security analysts to research, understand and interpret what they found in the data.
SIEM origins in computer science
As data became more sensitive and technology more powerful, SIEM systems (SIM + SEM) became capable of ingesting, processing and storing a great deal of data. Next-generation SIEM IT solutions are able to use signature-based alerts to identify threats in collected data. However, only those alerts that have identified indicators of compromise (IOC) of a certain threat can be identified in this way.
To be clear, if the type of attack to which a system is subjected has not been cataloged in a series of IOCs, a first generation SIEM is not able to detect it. The main drawback of those systems was the very limited ability to detect unknown cyber threats.
To give a practical example: it was possible to use a rule like this: “give a warning if a user enters 10 consecutive wrong passwords“. In theory this could be used to detect brute force password attacks. But what if the attacker only tried 9 passwords in a row? Or what if the alarm was given for a very forgetful user?
Next Gen SIEM (NGS)
A next generation SIEM is built on a large data platform that provides unlimited scalability and is hosted in the cloud. A next gen SIEM includes log management, advanced threat detection based on behavior analysis and automatic incident response, all on a single platform.
This eliminates the problems that old on-premises systems were prone to. Not having to install anything and being able to send the necessary data to the cloud quite simply, the computing power of the local machine is not compromised and the SIEM can manage all the data safely.
How a SIEM proceeds in cyber threat analysis
1. Data Collection: An IT SIEM solution collects data from across the organization using agents installed on various devices, including endpoints, servers, network equipment and other security solutions. Next generation SIEM includes support for cloud applications and infrastructure, business applications, identity data and non-technical data feeds.
2. Data enrichment: Enrichment adds further context to events. SIEM will enrich data with identity, resources, geolocation and threat information.
3. Data storage: The data will then be stored in a database so that it can be searched for during investigations. The next generation SIEM exploits open source architectures and big data architectures, exploiting their scalability.
4. Correlation and Analysis: SIEM solutions use several techniques to draw actionable conclusions from SIEM data. These techniques vary greatly.
5. Report: A SIEM, particularly a next generation SIEM, gives you the ability to quickly search for data, allowing you to dig through alerts and search for threat actors and indicators of compromise. The displayed data can be saved or exported. It is also possible to use out-of-the-box reports or create ad hoc reports as needed.
What a SIEM is used for
Threat hunting and investigation
The ability to perform threat hunting on a SIEM is critical to understanding the true patterns of attacks based on access, activity and data breaches. By developing a detailed and contextual view of attacks, security analysts can more easily develop policies, countermeasures and incident response processes to help mitigate and remove the threat.
Response in case of an accident
An effective response to incidents is essential to intervene more quickly and reduce the residence time of the threat. For this, a SIEM provides an incident response playbook with configurable automated actions. A SIEM is able to integrate with third party solutions for security orchestration (SOAR) or individual case management.
Defense against insider threats
The reason why insider threats are such a big problem is because it’s not about entering the perimeter, but about exploiting insider positions. They can be your employees, contractors or business associates. It may be they themselves wanting to exploit their location, or their account may have been hacked.
With all kinds of internal threats, the attacker tries to stay hidden, gathering sensitive data to exploit. This could cause significant damage to the company, its position in the industry and its relationship with consumers or investors. By using a SIEM, you avoid this risk.
Cyber threat detection
Your organization is likely to have at least one sensitive data repository. Cybercriminals thrive on looting this data for financial gain. Many breaches begin with a simple phishing email against an organization’s target. Simply clicking on an attachment can leave malicious code behind. A SIEM will allow you to monitor advanced cyberthreat patterns such as phishing, beaconing and lateral movement.
Compliance standards
For many industries, adherence to compliance standards is critical. A SIEM can help by providing reports focused on data compliance requests. Integrated packages covering all major mandates, including PCI DSS, SOX, and ISO 27001, are a standard feature of SIEMs as well.
Next Generation SIEM
A next generation SIEM is not just a cloud hosted system. It also makes use of the implementation of AI and Machine Learning to increase the defense of the IT system.
We will see it in a future article, but it is right to specify that the SOCaaS offered by SOD makes use of the latest generation technology offered by Next Gen. SIEM systems. Contact us to find out more about it and talk to experts who can dispel all your doubts.
[btnsx id=”2931″]
Useful links:
Security: Pentest and verification of vulnerabilities
What is a Network Lateral Movement and how to defend yourself
Is SOCaaS useful for your business?
Computer network security: PT vs. VA

During a cyber attack, hackers have only one goal in mind. This goal could be accessing a developer’s machine and stealing a project’s source code, analyzing emails from a particular executive, or extracting customer data from a server. All they have to do is log into the machine or system that contains the data they want, right? Not exactly. Actually, it’s a little more complicated than that. To achieve their goal, hackers are likely to break into a low-level web server, email account, or employee device, to name a few. From that node, they will move sideways (hence the name network lateral movement) to achieve their goal.
In fact, when attackers compromise a resource on a network, that device is almost never their final destination. In addition, the initial compromise rarely causes serious damage and may go unnoticed. Only if the security teams are able to detect a lateral movement before the attackers reach their intended goal, it is possible to prevent the data breach.
In this article, we will look at some of the more common types of network lateral movement and identify ways in which we can detect the attack and defend ourselves.
Understanding the network lateral movement
Lateral movement occurs when an attacker takes possession of a resource within a network and then extends its reach from that device to others within the same network. Let’s see it with an outline to help us understand better.
The perimeter of the infrastructure to be penetrated is represented with a horizontal line. The upper half represents what is outside the net, while what is below the line represents what is inside. In order for an attacker to enter the network, it must move vertically, ie from the outside to the inside (also called North-South traffic). But once a foothold has been established, it is possible to move sideways or horizontally, ie within the same network (called East-West traffic) to reach the final goal of the attack.
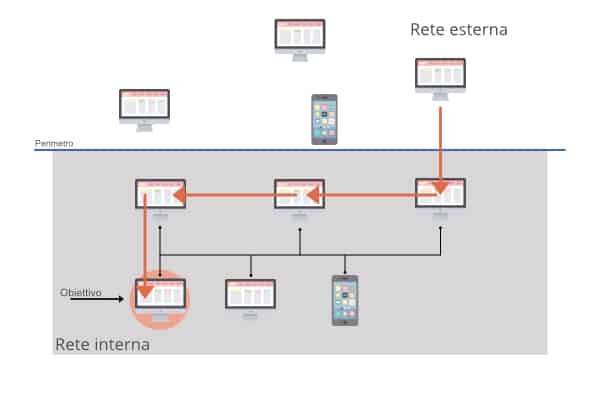
Possible path of a lateral movement. The arrow indicates the network nodes that are involved in the attack.
Approaches to the Lateral Movement
Overall, there are two common methods by which a hacker applies the lateral movement.
First approach: The attacker performs an internal scan to find out what other machines are on the network. In particular, it scans open ports that are listening and machines that suffer from vulnerabilities. At that point, the attacker can abuse these weaknesses to move sideways to another resource.
The second approach to the lateral movement exploits stolen credentials, and is the more common of the two. In this type of attack, the hacker could use an email phishing technique to infect a machine that interfaces with a particular server. Then he can use his login to recover passwords via a keylogger or other similar tools. At this point, he can use whatever credentials he was able to obtain to impersonate the user who was the victim of the phishing and log in to another machine. Once you have established access to that computer, you can repeat the tactic looking for additional credentials and / or privileges to exploit. In this way, the attacker can make their way and create remote connections to the target device.
In both cases it is difficult to identify the attack, because it does not occur through software or application malfunctions.
How to defend yourself
A lateral movement often manifests itself through anomalous network activity. For example, it is suspicious that a machine, which normally communicates with a few others, starts scanning the entire network. The same is true if that machine tries to connect to open ports, to interact with services and credentials with which it normally has no contact, or to use a username that has never been used before.
The list of alarm bells goes on and on. The key thing to understand is that a lateral movement involves machines doing something out of their routine, without proper authorization from IT.
This is what gives organizations the ability to detect this type of attack. Implementing log file monitoring is a first step in defense. Ideally, the data should be constantly analyzed for anomalies and possible breaches.
Defense issues
These defenses are not infallible. Security teams that simply rely on log files limit the scope of their defensive position, for example, due to log files collected only from particular applications. You might decide to monitor a certain service for credential theft, but attackers might not use that particular service to perform a lateral movement. This means that any malicious actions that do not use the monitored services will not be detected promptly.
In addition to this, hackers know the types of protocols that security personnel tend to monitor, making their task even more complex. Attackers can use this knowledge to model their attack campaigns in order to have a better chance of going unnoticed. It is one of the reasons why the MITER ATT & CK database was created to collect known techniques and raise the defenses.
The advantage of a SOCaaS
It is not enough for organizations to seek lateral movement using log files or an EDR tool. It is necessary to turn attention to the network as a whole. In this way it is possible to see all network traffic, establish a baseline of normal network activity for each user and device, and then monitor any unusual actions that could be indicative of attacks. It is known as anomaly detection, and is more comprehensive and often easier than examining each log file for out-of-the-ordinary events.
The problem with anomaly detection is that many of these irregularities are benign, and a lot of time is spent analyzing them. What is needed to separate harmful lateral movement from benign network anomalies is an understanding of the aspect of harmful behavior.
This is where a complete system that uses both behavioral analysis tools and professional security technicians comes into play.
The SOCaaS offered by SOD includes a Security Data Lake (SDL) for data collection and various tools for data analysis. One of these is the UEBA, particularly suitable for the detection of social threats, as it analyzes user behavior through AI using their actions as a source of data.
With these and other tools that make up the SOC, you can actively reduce the risk of attacks on your corporate data. If you are interested in learning more about SOD SOCaaS, I invite you to visit the dedicated page or contact us directly.
[btnsx id=”2931″]
Useful links:
Is SOCaaS useful for your business
Computer Network Security: PT vs. VA
Cyber Security: Pentest and verification of vulnerabilities

Mitre Att&ck is a global knowledge base of adversary tactics and techniques based on real observations of cyber attacks. These are displayed in arrays organized by attack tactics, from initial system access and data theft to machine control. There are arrays for common desktop platforms (Linux, macOS and Windows) and for mobile ones.
What is MITRE ATT&CK ™ and what does it mean?
ATT&CK stands for “adversarial tactics, techniques, and common knowledge” and that is: tactics, adversary techniques and common knowledge. Let’s try to go deeper.
Tactics and techniques are a modern way of thinking about cyber attacks. Rather than looking at the results of an attack – an indicator of compromise (IoC) – security analysts should look at the tactics and techniques that indicate an attack is in progress. Tactics represent the goal you want to achieve, while techniques represent how an opponent plans to achieve it.
Common knowledge is the documented use of tactics and techniques used by opponents. Essentially, common knowledge is the documentation of the procedures used by the attacker. Those familiar with cybersecurity may be familiar with the term “tactics, techniques and procedures” or TTP. This same concept has been used by ATT&CK ™, replacing the term procedure with common knowledge.
Who is MITRE and what is the goal of ATT&CK ™?
MITRE is a US government funded research organization based in Bedford, MA, and McLean, VA. The company was spun off from MIT in 1958 and was involved in a number of top secret commercial projects for various agencies. These included the development of the FAA’s air traffic control system and the AWACS radar system. MITRE has a substantial cybersecurity practice funded by the National Institute of Standards and Technology (NIST).
A curiosity: the word Mitre means nothing. Apparently one of the first members, James McCormack, wanted a name that meant nothing but was evocative. Some mistakenly think it means Massachusetts Institute of Technology Research and Engineering.
ATT&CK’s goal is to create a comprehensive list of known opponent tactics and techniques used during a cyber attack. Open to governmental, educational and commercial organizations, it should be able to gather a wide, and hopefully comprehensive, range of attack phases and sequences. MITRE ATT&CK aims to create a standard taxonomy to make communications between organizations more specific.
How is the ATT&CK ™ matrix used?
The matrix visually organizes all known tactics and techniques in an easy to understand format. Attack tactics are shown above, and individual techniques are listed below in each column. An attack sequence would involve at least one technique per tactic, and a complete attack sequence would be constructed by moving from left (Initial Access) to right (Command and Control). It is possible to use more techniques for a single tactic. For example, an attacker might try both a Spearphishing Attachment and a Spearphishing Link as initial login tactics.
Here is an example of a matrix:
In this matrix there are all the phases of an attack sequence. It is organized so that the tactics are ordered from right to left according to the attack sequence. Under each tactic the corresponding techniques, some of which contain sub-techniques. The two techniques mentioned above are actually sub-techniques of phishing which are part of the first step in the sequence (first column on the left).
Example
It is not necessary for an attacker to use all eleven tactics at the top of the matrix. Rather, the attacker will use the minimum number of tactics to achieve his goal, as it is more efficient and provides less chance of discovery. In this attack (illustrated in the diagram below), the adversary performs initial access to the CEO’s administrative assistant credentials using a Spearphishing link delivered in an email. Once in possession of the administrator’s credentials, the attacker searches for a Remote System Discovery of the Discovery phase.
Let’s say they’re looking for sensitive data in a Dropbox folder that the admin also has access to, so there’s no need to increase privileges. The collection, which is the last stage, is done by downloading the files from Dropbox to the attacker’s machine.
Note that if you are using behavior analysis, a security analyst could detect the attack in progress by identifying abnormal user behavior.
And that’s exactly what a SOC should do, here, roughly, how the attack could be mitigated: suppose the administrator clicked a link that no one in the company has ever clicked before, then the administrator logged in a particular Dropbox folder at an unusual time. During the final phase of the attack, the attacker’s computer entered the Dropbox folder for the first time. With behavioral analysis, these activities would be flagged as suspicious user behavior.
To consult ATT&CK
To consult this resource just visit his site and you will find yourself in front of the matrix of which I published a screenshot a little while ago. Suppose we want to consult the Spearphishing Link technique. By clicking on it, the corresponding page will open containing in-depth information about it, such as a description of the technique, what sub-techniques exist, examples of procedures that include it and suggestions for risk mitigation.
Basically all the information necessary to know and defend oneself appropriately from each technique is available.
Conclusions
The advantages of a resource like MITRE ATT&CK are truly remarkable. Cyber security teams have a valuable ally at their disposal, to which they can add dedicated tools for its consultation.
While it is almost certain that attackers are adapting as defenders deploy new skills, it is also true that ATT&CK provides a way to describe the new techniques they develop.
[btnsx id=”2931″]
Useful links:
Security: Pentest and verification of vulnerabilities
What is a Network Lateral Movement and how to defend yourself
Is SOCaaS useful for your business?
Computer network security: PT vs. VA

In today’s article, we’ll explain what a Security Operations Center (SOC) is and help determine if a SOC-as-a-Service (SOCaaS) solution is right for your business. Just because you have to manage cybersecurity doesn’t mean your business has to deal with cybersecurity. In fact, your core business could be pretty much anything else.
Proper management of IT security, however, is essential to allow your company to grow and to obtain the certifications for data processing required by law. Having the right cybersecurity skills available at the right time is critical to your success, but you have no idea when that time will be.
Choosing the right technology, people and processes to build a modern security operations section is one of the biggest challenges for IT security managers.
What is a SOCaaS and what it can do for you
Before understanding what the management challenges are, it is good to understand what a SOC is. It performs the following functions:
Plan, configure and maintain your security infrastructure.
With a SOC it is possible to configure the technology stack (endpoint, SaaS applications, cloud infrastructure, network, etc.) to identify the relevant activity and eliminate unnecessary data. Monitor data sources to ensure the ecosystem is always connected.
Detect and respond
In addition, it is possible to monitor the incoming alarm activity. Investigate alarms to determine if it is a true security issue or a false alarm. If something is a real security threat, you can evaluate the magnitude of the situation and take response actions.
Threat hunting
The activity of a certain event can be examined to determine if there are any signs of impairment that may have eluded the automated controls. The most common scenario is to review the history of an IP address or file that has been determined to be malicious.
Storage of log files
Another possibility is to securely collect and archive log files, for up to seven years, for compliance with regulations. The team will need to provide this critical data for forensic analysis in the event of a security situation.
Measure performance indicators
Obviously it is possible to monitor the KPIs (performance indicators). In detail it is possible to measure and report the KPIs to demonstrate to the executive team how the SOC is working.
The challenges of implementing your own SOC
Finding, training and retaining cybersecurity professionals is expensive
The skills needed to manage IT security tasks are in high demand. Unfortunately, the shortage is bound to get worse before it gets better. According to the International Certification Organization (ISC), the number of vacant positions worldwide was over 4 million professionals in 2019, up from nearly three million the previous year.
Training personnel with a broad IT background in cybersecurity skills is an option, but retaining these people is expensive. Their replacement, when eventually taken elsewhere, starts a cycle that usually ends up being more expensive than expected, especially compared to SOCaaS.
Also, people who work well in this industry usually want to explore new topics and take on new challenges. You will need to find other related projects or roles to rotate SOC staff to keep them engaged. This also helps build their skills, so they are ready to respond and act promptly when needed.
Cyber security is a team sport
It is important to have a diverse set of skills and a team that works well as a team. Security threats evolve rapidly, proper investigation and responses require people who understand endpoints, networks, cloud applications, and more. Often you end up being a SOC manager, a sysadmin and a threat hunter, depending on the day and what happens in your environment.
This means that you will need a team that is constantly learning, so that you have the right skills when you need them. People who do well in this industry thrive in a team environment where they can learn and challenge each other. For this, you need a workflow that regularly brings together several SOC analysts.
Think of it this way: you wouldn’t put a football team on the pitch that didn’t train together. Your SOC team collides with an opponent who plays as a team every day. To be successful, you need professionals who have a lot of playing experience to build their skills both in the single position and as a team.
A team of SOC analysts who do not do regular training will not be ready when hit by a well-trained opponent. It is difficult to get this experience in a small organization.
A SOCaaS is the immediate answer to this need. The team that will take care of your IT security is trained and stimulated every day by ever new challenges, having to deal with different infrastructures every day.
24/7 coverage is a necessity
Letting an opponent be free to bait for hours, days or weeks makes it infinitely more difficult to contain and remove threats. The adversary knows they have limited time to do as much damage as possible, as in the case of ransomware, or to overshadow ports, as in the case of data extrusion.
You will have the best chance of recovery if you can investigate and respond within minutes. A solution that provides 24 × 7 coverage is therefore essential.
In computer security there are no “working hours” for one particular reason: an attack could come from anywhere on the globe, consequently you cannot rely on conventional hours. This is the result of the spread of the network as an instrument of worldwide connection, we can only deal with it adequately. A SOCaaS relieves the company using it from keeping a division open 24/7.
Managing suppliers and integrating tools is quite expensive
Cyber security is complex and technology evolves rapidly. There will be more and more technologies that need to work together, which requires maintaining the skills to implement, update and configure each component and train your staff on new versions and features. If you have your own SOC, you also need to manage these supplier relationships, licensing, and training.
The bottom line is that building the skills you need requires a lot of low-level tasks and extensive daily work. For organizations that can support it, the effort makes sense. For most organizations, the task is best left to a partner who can provide this service, allowing you to get all the benefits of a high-end SOC without the expense and distraction of building it yourself.
Conclusions
If budget is not an issue and you have enough staff to focus on building and maintaining a 24 × 7 SOC, then it may make sense to go this route. If you are constrained on one of these two fronts, then SOCaaS will be the best approach.
In summary, SOCaaS allows you to:
1. Spend time managing security, not technology and vendors
2. Have a predictable expense. No surprise budget requests
3. Obtain security information from other organizations
4. Manage alarms more efficiently and with more predictable results
5. Be agile and keep up with the IT needs of your evolving organization
6. Stay abreast of today’s security tool innovations.
If your company wants to know more about Secure Online Desktop SOCaaS solutions, contact us for a non-binding consultation. We will show you all the advantages and clear up any doubts regarding this solution.
[btnsx id=”2931″]
Useful links:
Customers
Twitter FEED
Recent activity
-
SecureOnlineDesktop
Estimated reading time: 6 minutes L'impatto crescente delle minacce informatiche, su sistemi operativi privati op… https://t.co/FimxTS4o9G
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The growing impact of cyber threats, on private or corporate operating systems… https://t.co/y6G6RYA9n1
-
SecureOnlineDesktop
Tempo di lettura stimato: 6 minuti Today we are talking about the CTI update of our services. Data security is… https://t.co/YAZkn7iFqa
-
SecureOnlineDesktop
Estimated reading time: 6 minutes Il tema della sicurezza delle informazioni è di grande attualità in questo peri… https://t.co/tfve5Kzr09
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The issue of information security is very topical in this historical period ch… https://t.co/TP8gvdRcrF
Newsletter
{subscription_form_1}© 2024 Cyberfero s.r.l. All Rights Reserved. Sede Legale: via Statuto 3 - 42121 Reggio Emilia (RE) – PEC [email protected] Cod. fiscale e P.IVA 03058120357 – R.E.A. 356650 Informativa Privacy - Certificazioni ISO